Microsoft Alerts on Phishing Risks from Misconfigured Email Routing and Spoofing Tactics
Published on: 2026-01-07
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Warns Misconfigured Email Routing Can Enable Internal Domain Phishing
1. BLUF (Bottom Line Up Front)
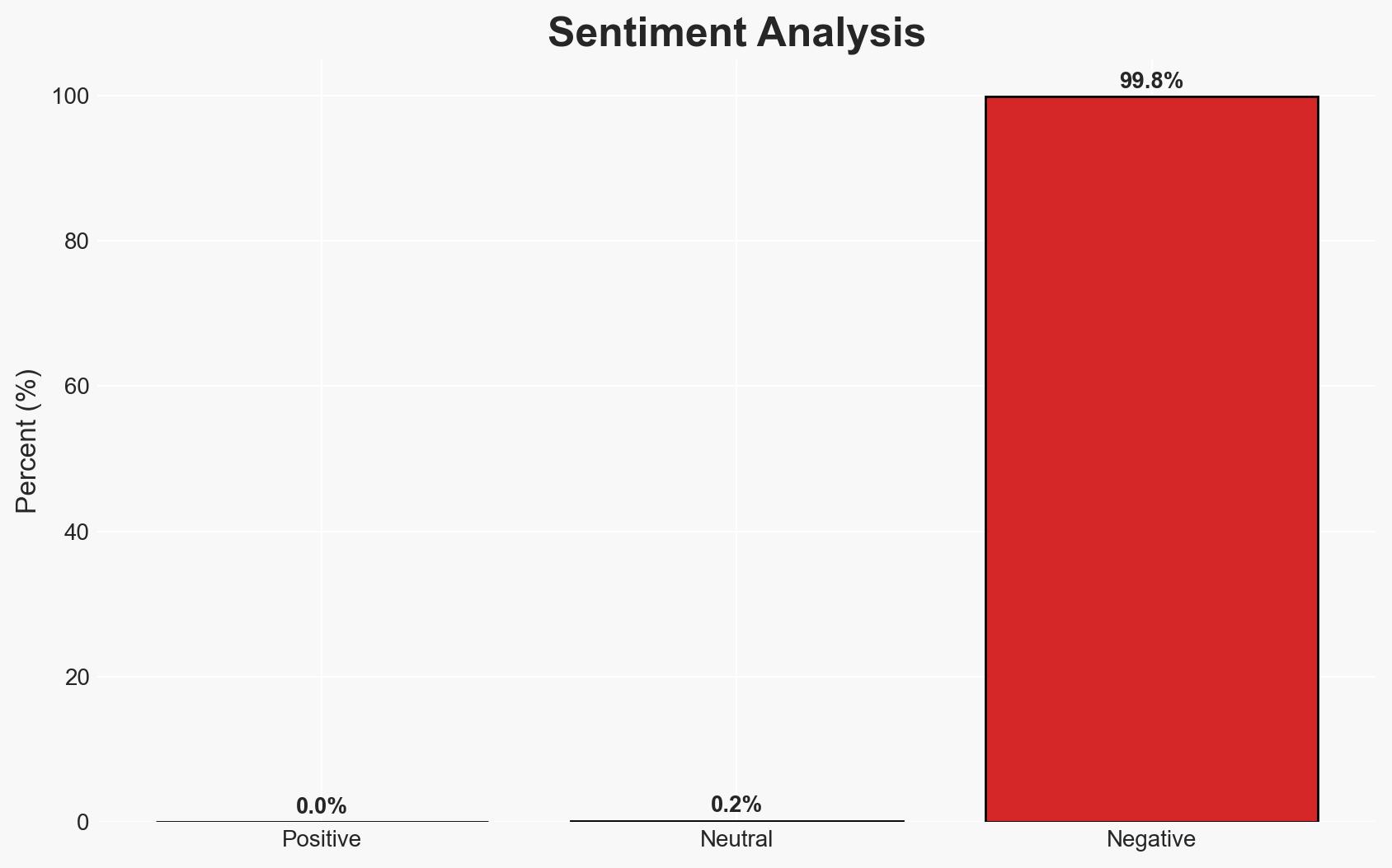
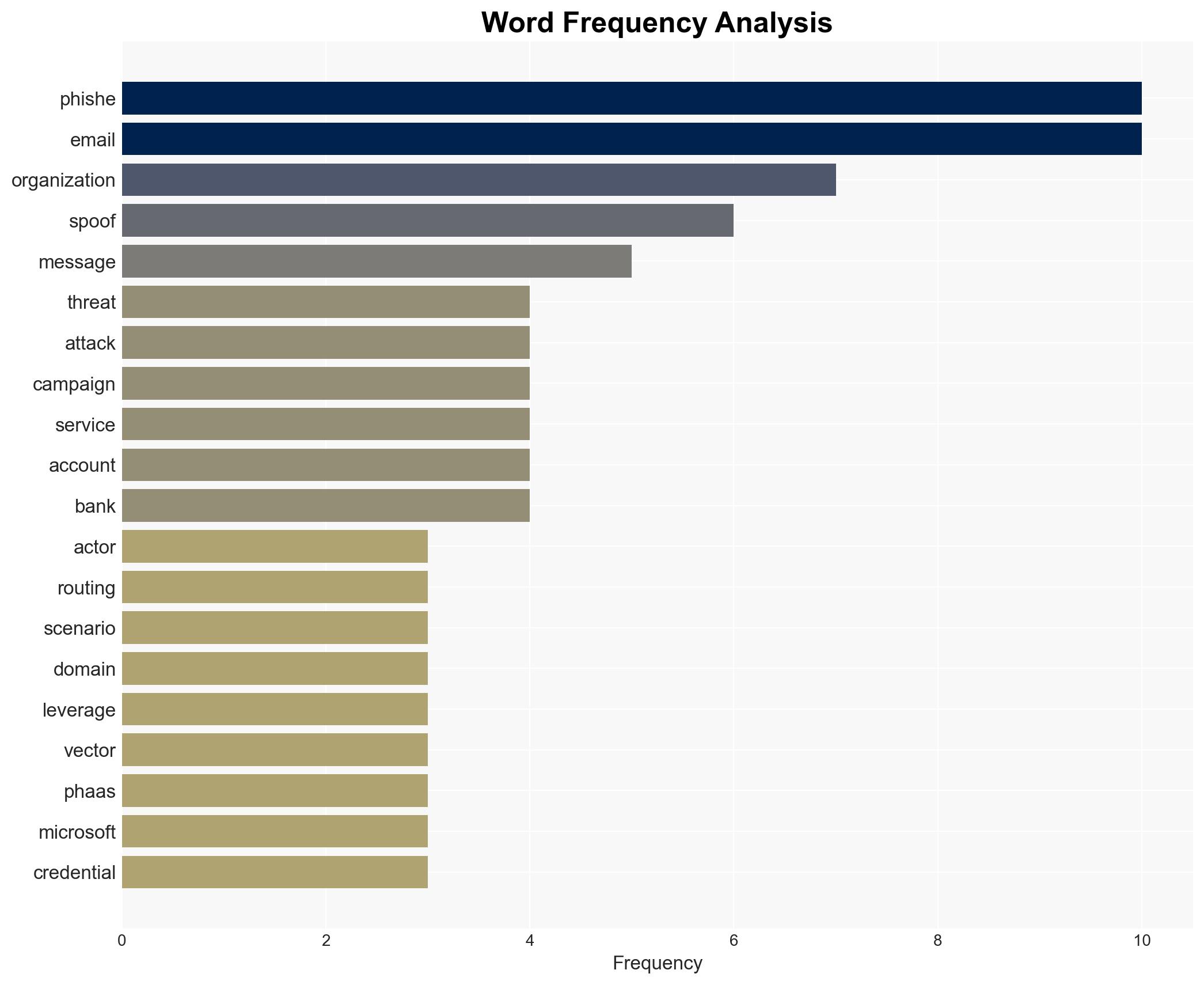
Threat actors are exploiting misconfigured email routing and spoof protections to conduct internal domain phishing, posing a significant risk to organizations across multiple sectors. The surge in these phishing campaigns, particularly using Phishing-as-a-Service (PhaaS) platforms, is likely to lead to credential theft and financial scams. This development affects organizations with complex email routing configurations. Overall, there is moderate confidence in the assessment due to the reliance on available technical data and observed trends.
2. Competing Hypotheses
- Hypothesis A: The increase in phishing attacks is primarily due to the exploitation of technical vulnerabilities in email routing and spoof protection configurations. This is supported by the reported surge in attacks since May 2025 and the use of PhaaS platforms. However, the extent to which these configurations are widespread remains uncertain.
- Hypothesis B: The surge in phishing attacks is driven more by the increased accessibility and sophistication of PhaaS platforms rather than technical misconfigurations alone. This hypothesis is supported by the widespread use of Tycoon 2FA PhaaS kits, which lower the barrier for conducting phishing campaigns.
- Assessment: Hypothesis A is currently better supported due to the specific mention of misconfigured routing and spoof protections as a primary vector. Indicators such as changes in PhaaS platform usage or new technical mitigations could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Threat actors will continue to exploit technical vulnerabilities; PhaaS platforms will remain accessible and effective; organizations will not rapidly correct misconfigurations.
- Information Gaps: Detailed data on the prevalence of misconfigured email systems and the specific industries most affected.
- Bias & Deception Risks: Potential bias in reporting from Microsoft as a vendor; threat actors may intentionally mislead about the origins or methods of attacks.
4. Implications and Strategic Risks
The exploitation of email routing vulnerabilities could lead to increased credential theft and financial losses, impacting organizational trust and operational security. Over time, this could erode confidence in digital communications and necessitate regulatory responses.
- Political / Geopolitical: Potential for international tensions if state actors are implicated or if attacks target critical infrastructure.
- Security / Counter-Terrorism: Increased operational risk for organizations; potential for these tactics to be adopted by terrorist groups.
- Cyber / Information Space: Escalation in cyber threat landscape; potential for more sophisticated phishing techniques to emerge.
- Economic / Social: Financial losses from scams could impact economic stability; increased demand for cybersecurity solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct audits of email routing configurations; enhance spoof protection measures; increase staff awareness and training on phishing risks.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in advanced threat detection and response capabilities; advocate for industry-wide standards on email security.
- Scenario Outlook:
- Best: Organizations rapidly address vulnerabilities, reducing phishing success rates.
- Worst: Phishing tactics evolve faster than defenses, leading to widespread breaches and financial losses.
- Most-Likely: Continued moderate success of phishing campaigns with incremental improvements in defenses.
6. Key Individuals and Entities
- Microsoft Threat Intelligence team
- Tycoon 2FA PhaaS platform
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, phishing, email security, PhaaS, credential theft, financial scams, Microsoft
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us