Microsoft Confirms Password Spraying Attack What You Need To Know – Forbes
Published on: 2025-04-28
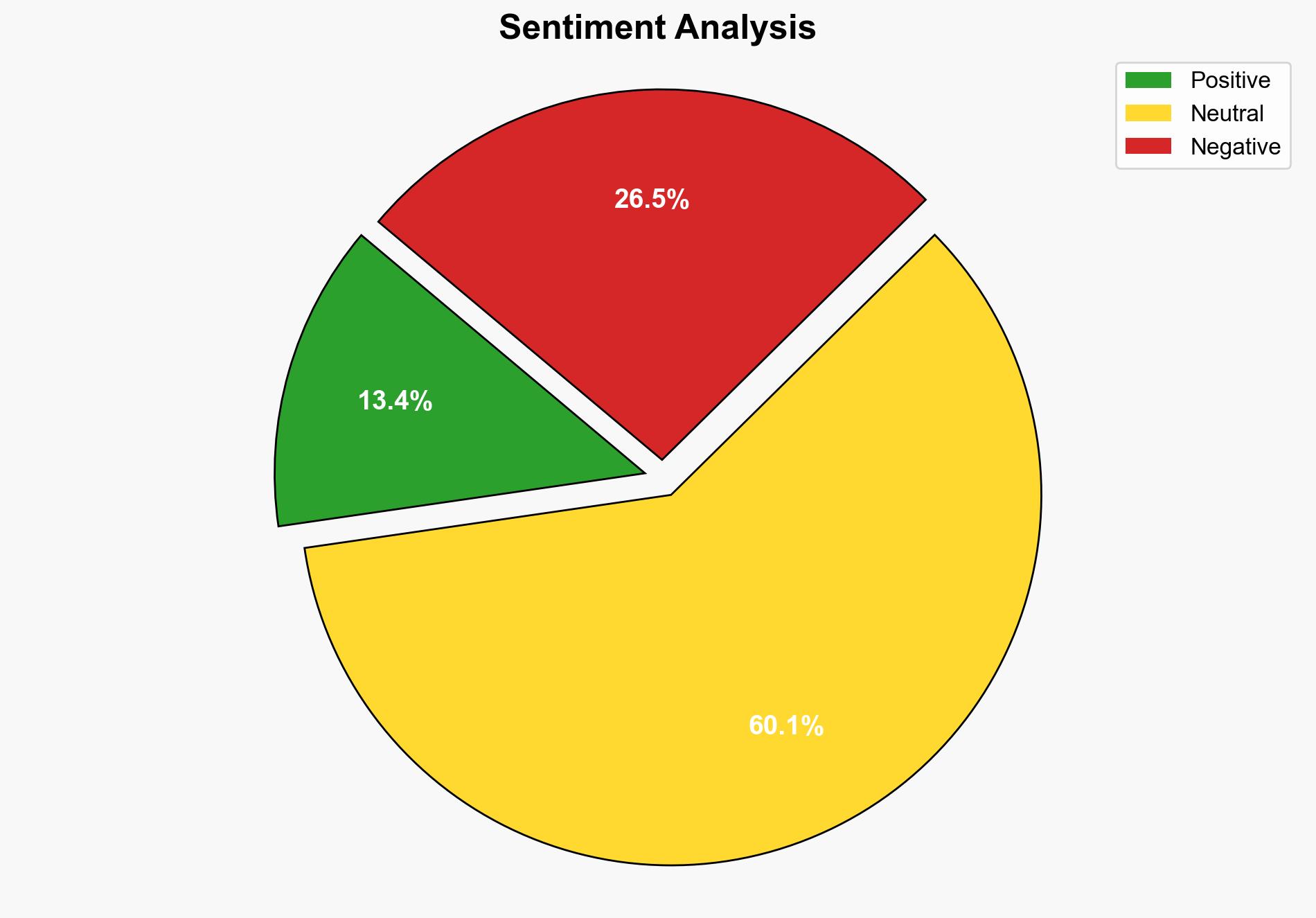
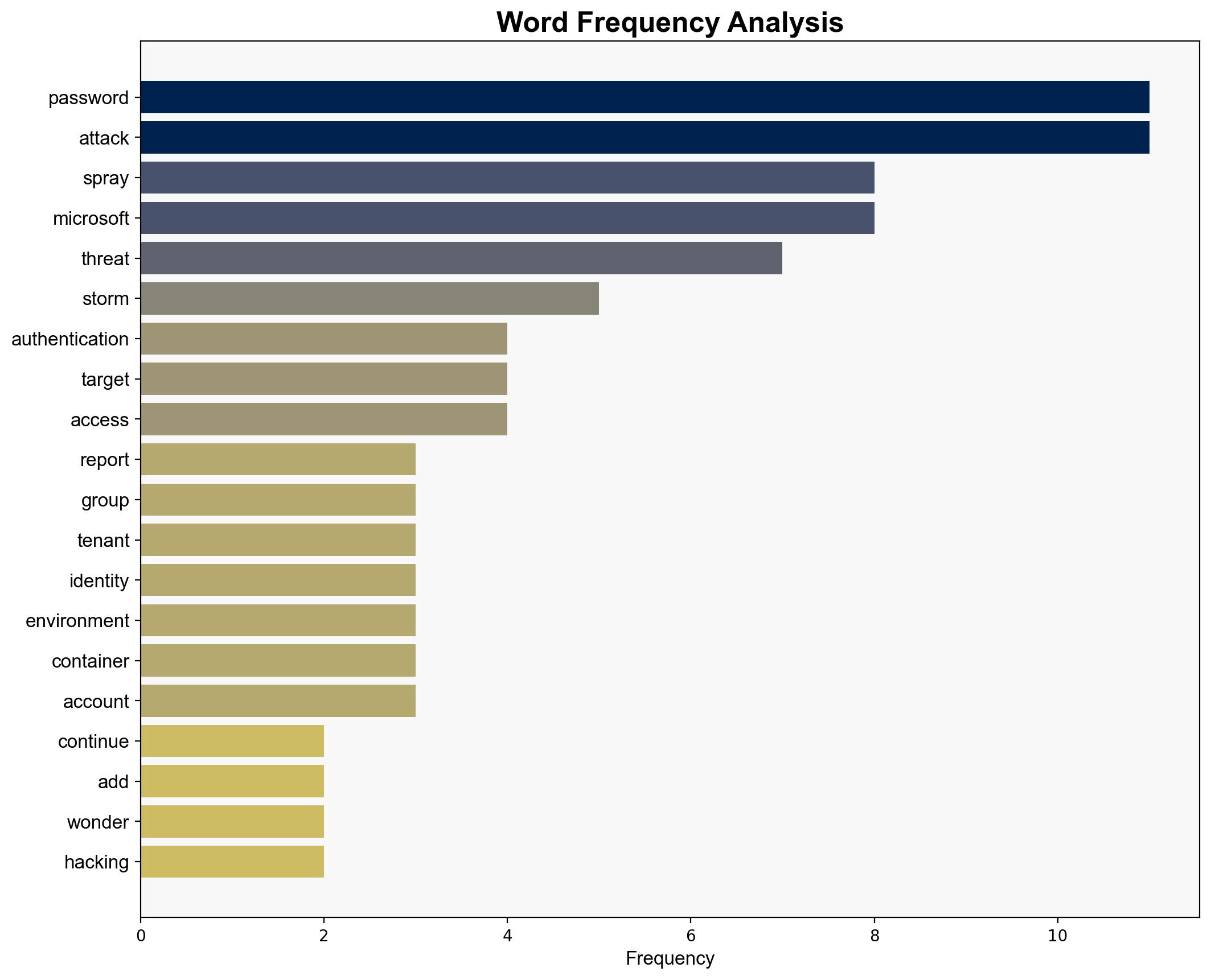
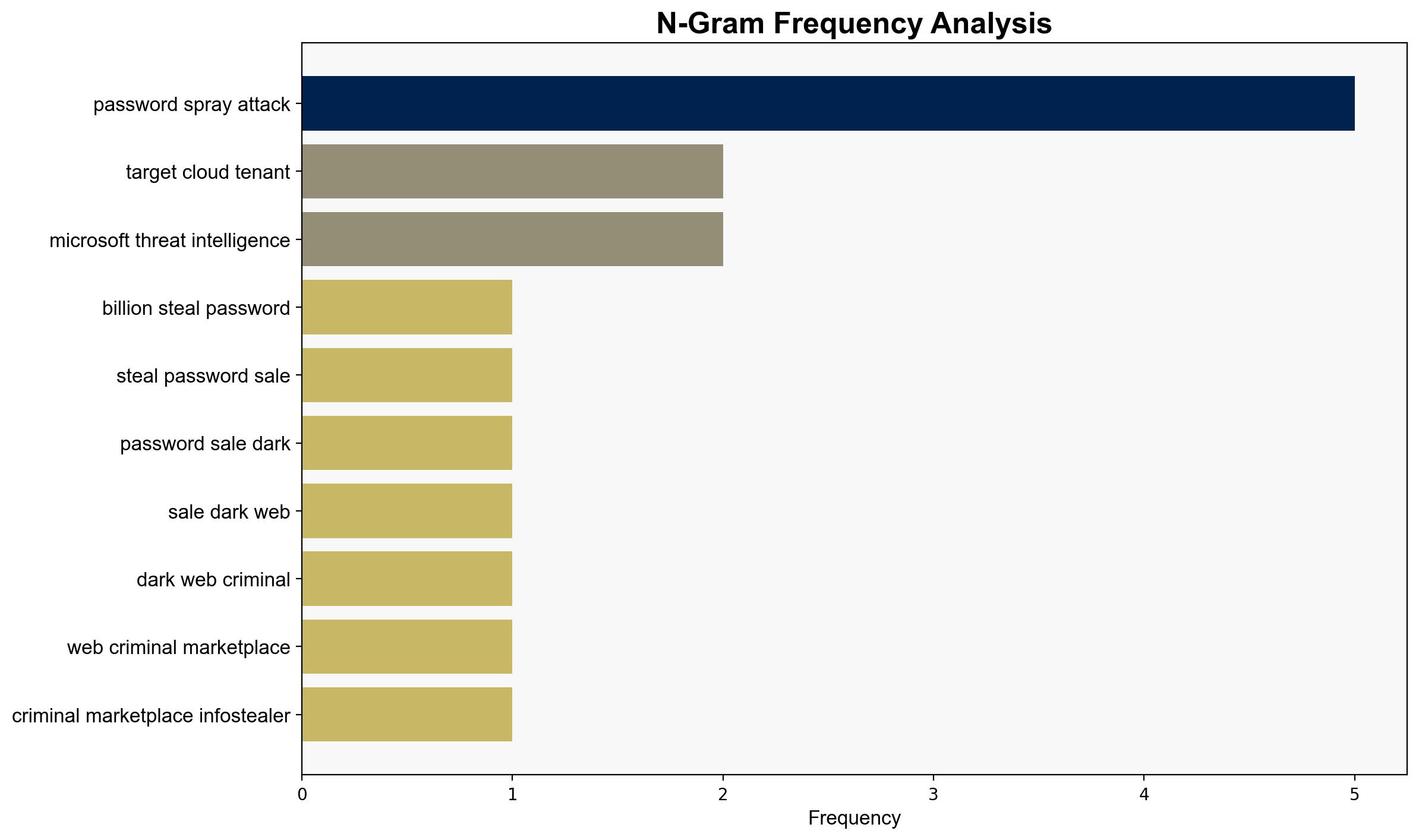
Intelligence Report: Microsoft Confirms Password Spraying Attack What You Need To Know – Forbes
1. BLUF (Bottom Line Up Front)
Microsoft has identified a significant password spraying attack targeting cloud tenants, particularly in the education sector. The attack is attributed to a hacking group known as Storm. The attackers exploit unsecured workload identities to gain access to containerized environments. Immediate implementation of strong authentication measures is recommended to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The hypothesis that the attack is primarily targeting unsecured cloud environments is supported by the evidence of exploitation of workload identities and container services. Alternative hypotheses, such as targeting on-premises systems, are less supported by the current data.
SWOT Analysis
Strengths: Microsoft’s proactive threat intelligence capabilities.
Weaknesses: Vulnerability in workload identity security.
Opportunities: Enhanced security protocols for cloud services.
Threats: Increasing sophistication of cybercriminal groups like Storm.
Indicators Development
Key indicators include increased unauthorized access attempts, use of command-line interface tools like AzureChecker, and the presence of AES-encrypted data files.
3. Implications and Strategic Risks
The attack underscores a growing trend of targeting cloud services, which could lead to widespread disruptions if not addressed. The education sector’s vulnerability highlights systemic weaknesses that could have broader implications for data security and privacy.
4. Recommendations and Outlook
- Implement robust authentication methods, including multi-factor authentication, to secure cloud interfaces.
- Regularly update and audit security protocols for containerized environments.
- Best Case: Enhanced security measures prevent further breaches.
- Worst Case: Failure to act leads to significant data breaches and operational disruptions.
- Most Likely: Incremental improvements in security posture reduce but do not eliminate risks.
5. Key Individuals and Entities
The hacking group identified as Storm is central to this attack. No specific individuals are named in the report.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)