Microsoft Exposes Scattered Spiders Latest Tactics – Infosecurity Magazine
Published on: 2025-07-17
Intelligence Report: Microsoft Exposes Scattered Spiders Latest Tactics – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
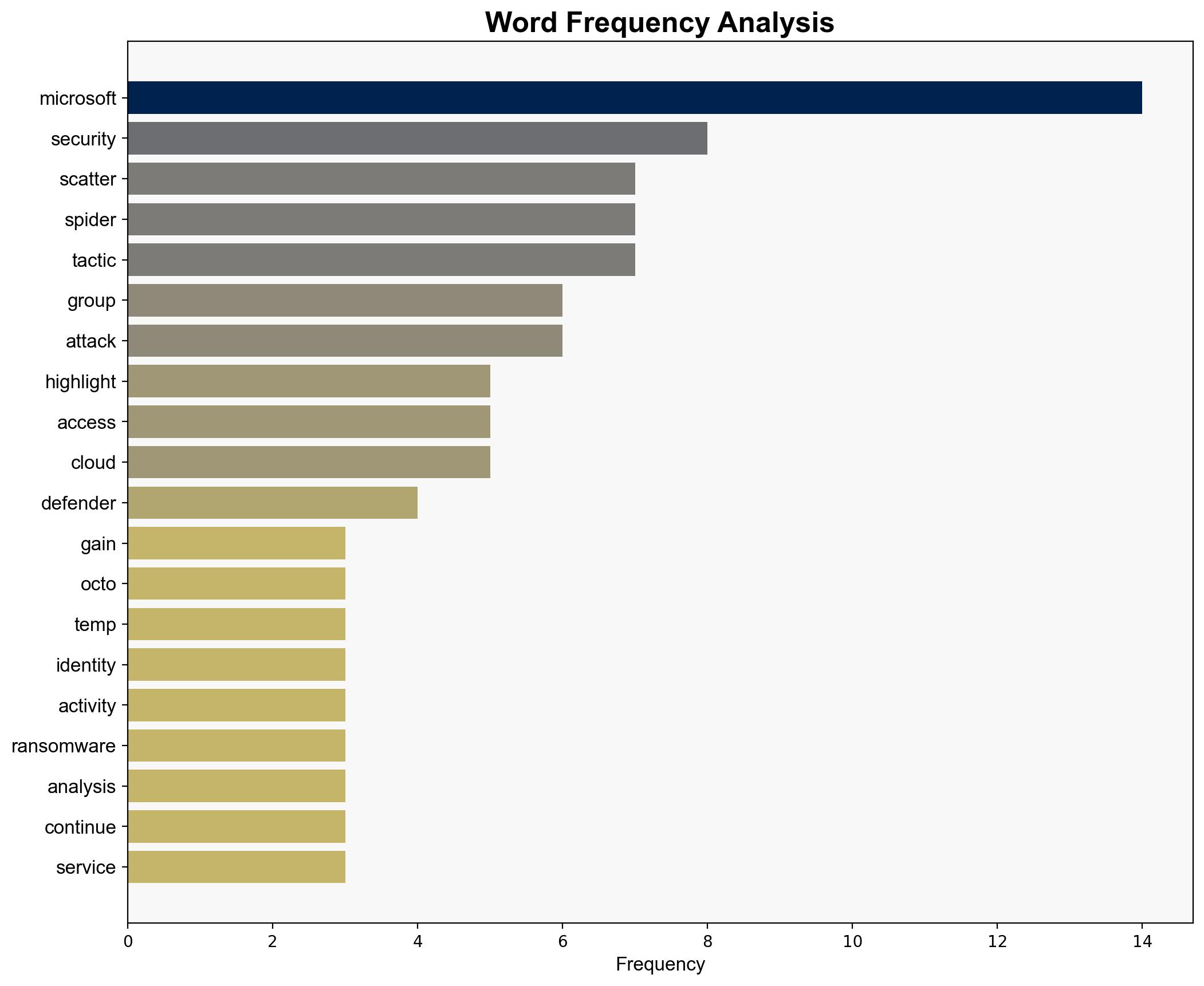
Microsoft has identified evolving tactics by the cyber group known as Scattered Spider, also referred to as Octo Tempest. The group is leveraging advanced social engineering techniques and deploying ransomware, particularly targeting VMware ESX hypervisor environments. Key recommendations include enhancing identity and endpoint security measures and implementing risk-based sign-in policies to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Scattered Spider’s tactics include aggressive social engineering and manipulation of service desk support personnel to gain initial access, followed by the deployment of ransomware. This simulation helps anticipate potential vulnerabilities in cloud environments.
Indicators Development
Microsoft’s security ecosystem, including Microsoft Defender and Microsoft Sentinel, has been updated to detect and monitor anomalies indicative of Scattered Spider’s activities, such as adversary-in-the-middle (AiTM) attacks and SMS phishing.
Bayesian Scenario Modeling
Probabilistic modeling suggests a high likelihood of continued attacks on sectors like airlines, retail, and hospitality, with potential expansion into new industries.
3. Implications and Strategic Risks
The persistent evolution of Scattered Spider’s tactics poses significant risks to cloud infrastructure and enterprise security. The group’s focus on critical sectors like airlines and hospitality could lead to widespread disruptions and economic impacts. Cross-domain risks include potential data breaches and extortion attempts.
4. Recommendations and Outlook
- Enhance multi-factor authentication (MFA) and implement risk-based sign-in policies to limit unauthorized access.
- Conduct regular security audits and penetration testing to identify and mitigate vulnerabilities.
- Scenario-based projections suggest that proactive defense measures could significantly reduce the impact of potential attacks.
5. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus remains on the group Scattered Spider and Microsoft’s security response.
6. Thematic Tags
national security threats, cybersecurity, ransomware, cloud security, social engineering