Microsoft Fixes Over 130 CVEs in April Patch Tuesday – Infosecurity Magazine
Published on: 2025-04-09
Intelligence Report: Microsoft Fixes Over 130 CVEs in April Patch Tuesday – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
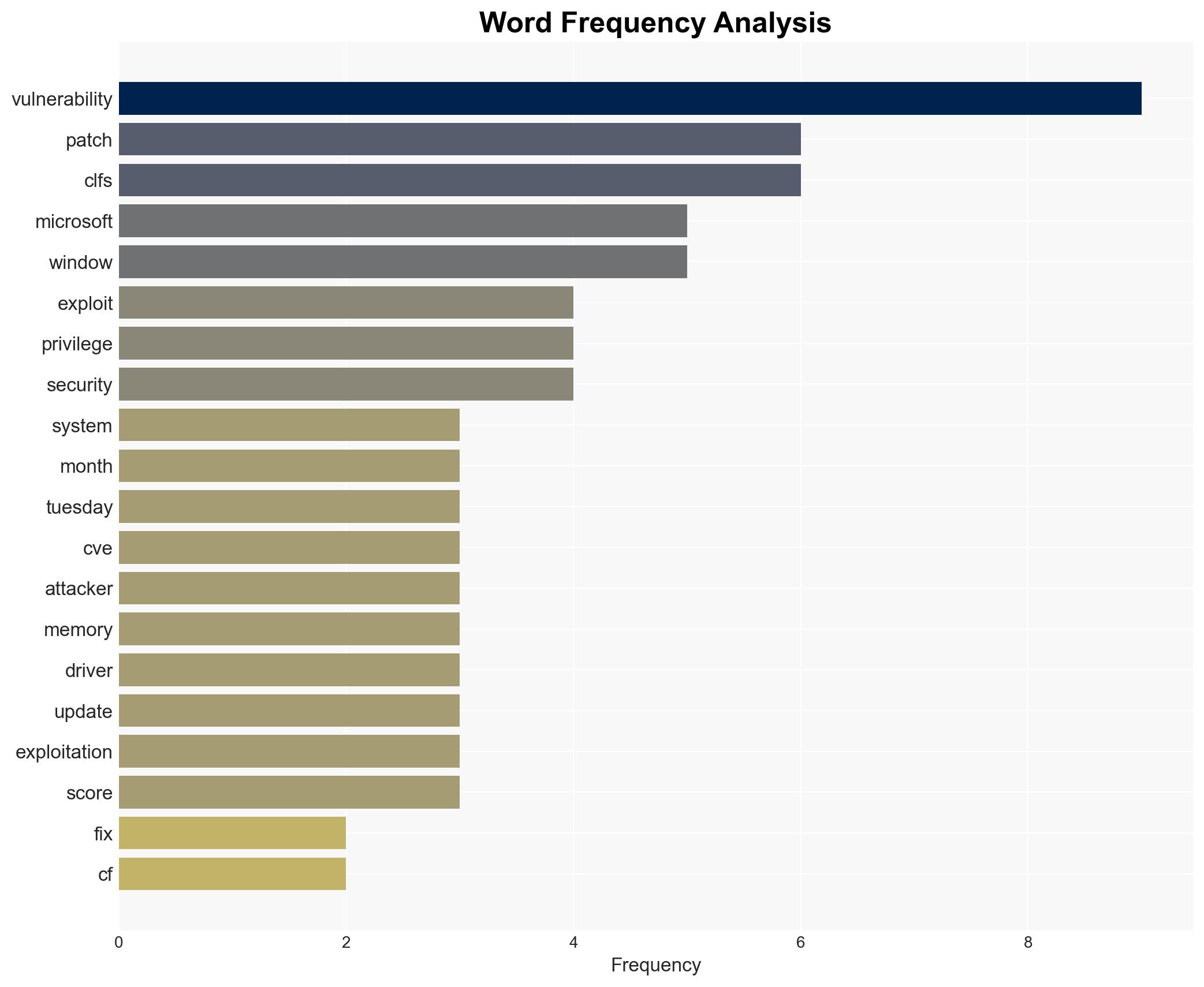
Microsoft has released fixes for over 130 Common Vulnerabilities and Exposures (CVEs) in its April Patch Tuesday update. This includes a critical zero-day vulnerability in the Windows Common Log File System (CLFS) that has been actively exploited. Organizations are urged to prioritize these updates to mitigate potential security threats, particularly those related to privilege escalation and ransomware attacks.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
Microsoft has addressed a significant number of vulnerabilities, with a focus on a zero-day bug in the CLFS driver. This vulnerability allows attackers to execute code at a high privilege level without administrative access, posing a substantial risk in post-compromise scenarios. The exploitation of this vulnerability can facilitate persistent access and lateral movement within enterprise networks, making it a favored target for ransomware operations.
The update also highlights the importance of monitoring the CLFS driver using Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) tools to detect anomalous behavior. The prioritization of patches should not solely rely on CVSS scores but also consider the exploitability index provided by Microsoft.
3. Implications and Strategic Risks
The active exploitation of the CLFS vulnerability poses significant risks to organizational security, potentially impacting national security and economic interests. The vulnerability’s ability to facilitate privilege escalation increases the threat of ransomware attacks, which can disrupt critical infrastructure and services. The widespread use of Windows systems amplifies the potential impact, necessitating immediate attention from security teams.
4. Recommendations and Outlook
Recommendations:
- Organizations should prioritize the deployment of the April Patch Tuesday updates, with particular focus on the CLFS vulnerability.
- Implement robust monitoring of the CLFS driver using EDR and XDR tools to detect and respond to anomalous activities.
- Security teams should consider both CVSS scores and exploitability indices when prioritizing patch deployments.
Outlook:
In the best-case scenario, rapid deployment of patches will mitigate the risk of exploitation, reducing the potential for widespread ransomware attacks. In the worst-case scenario, delayed patching could lead to increased incidents of privilege escalation and ransomware, impacting critical sectors. The most likely outcome is a mixed response, with some organizations effectively mitigating risks while others remain vulnerable.
5. Key Individuals and Entities
The report mentions Ben McCarthy and Tyler Reguly as significant individuals providing insights into the vulnerabilities and patch prioritization strategies.