Microsoft reports widespread exploitation of React2Shell vulnerability, affecting hundreds of organizations g…
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: React2Shell exploitation spreads as Microsoft counts hundreds of hacked machines
1. BLUF (Bottom Line Up Front)
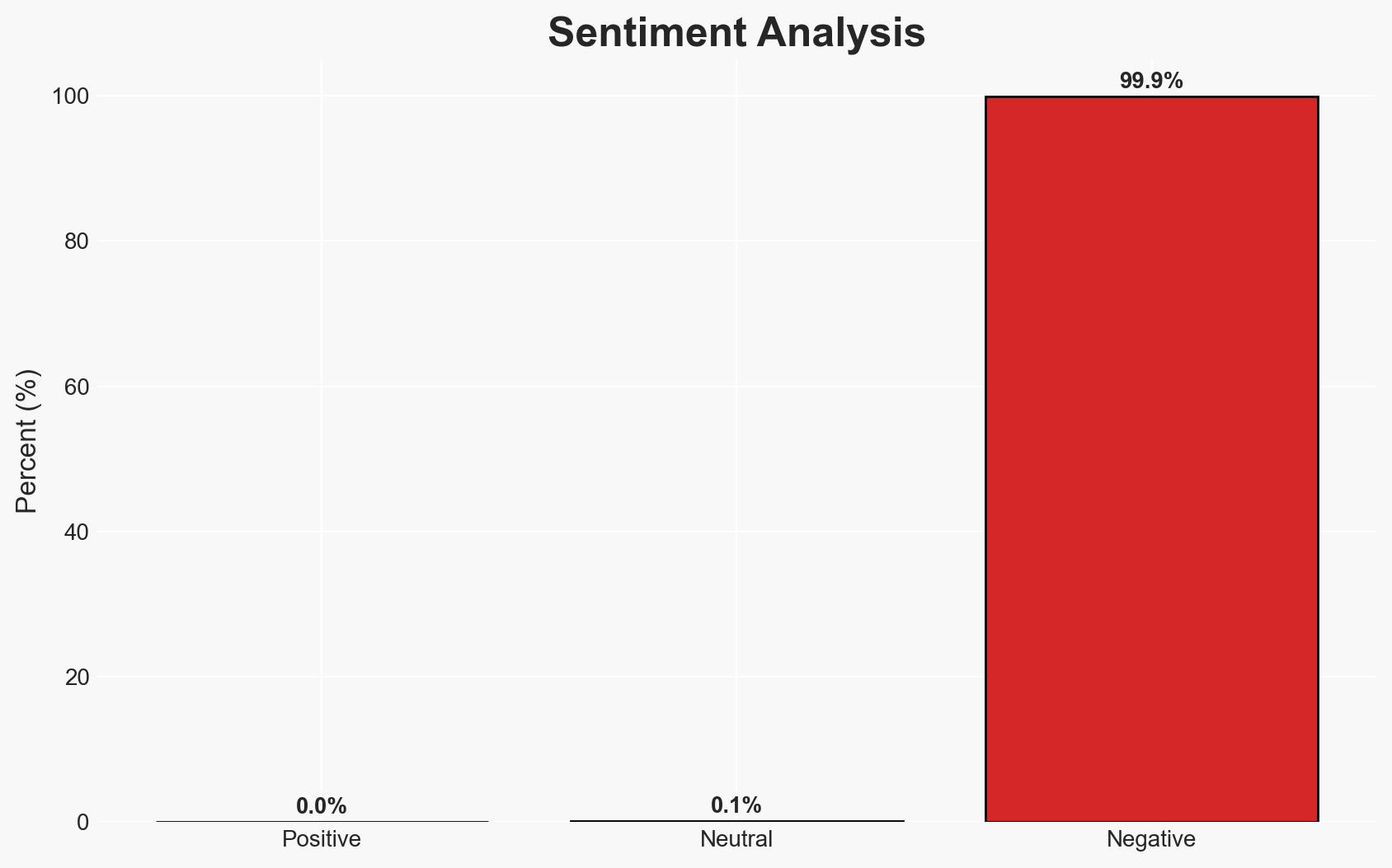
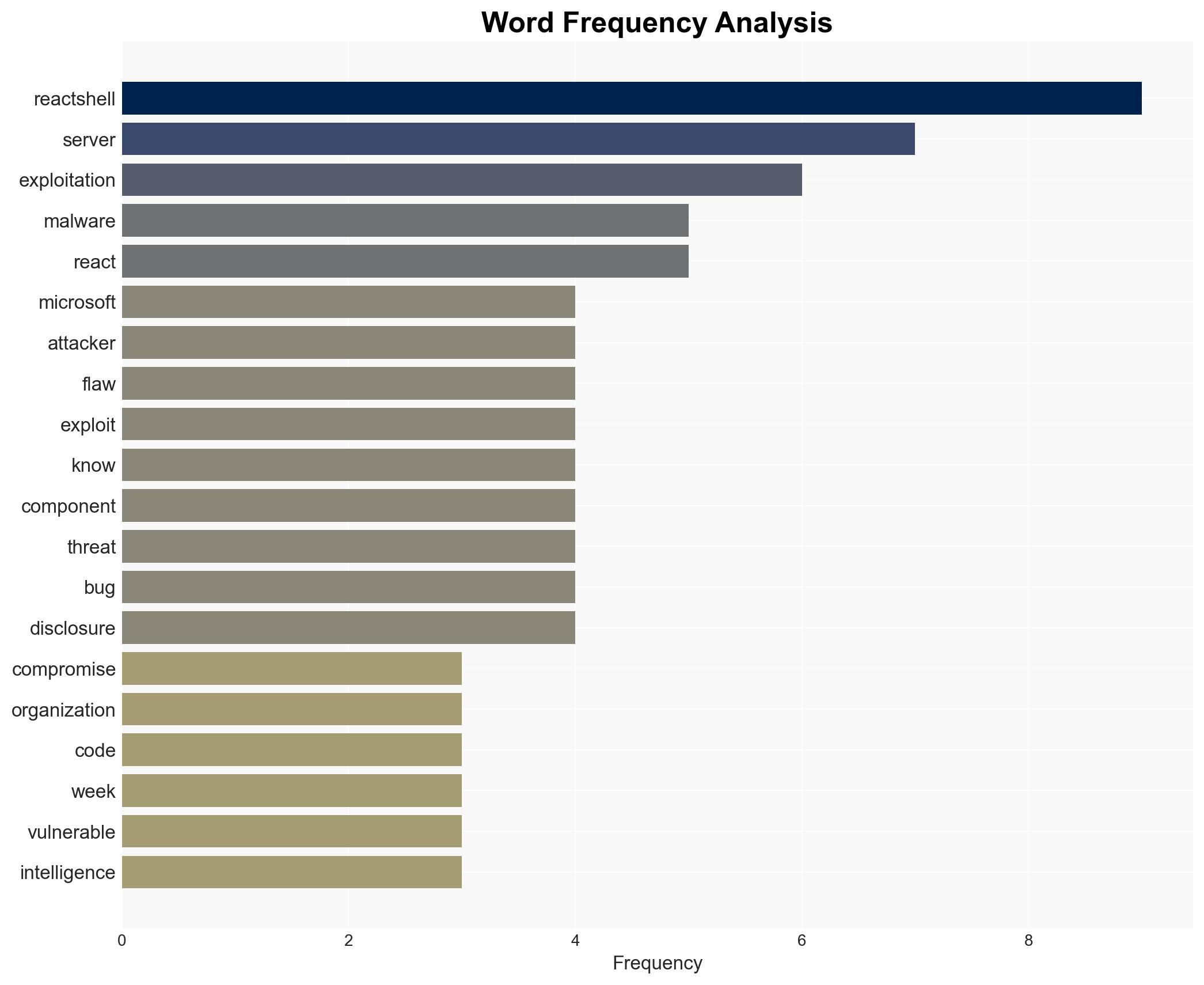
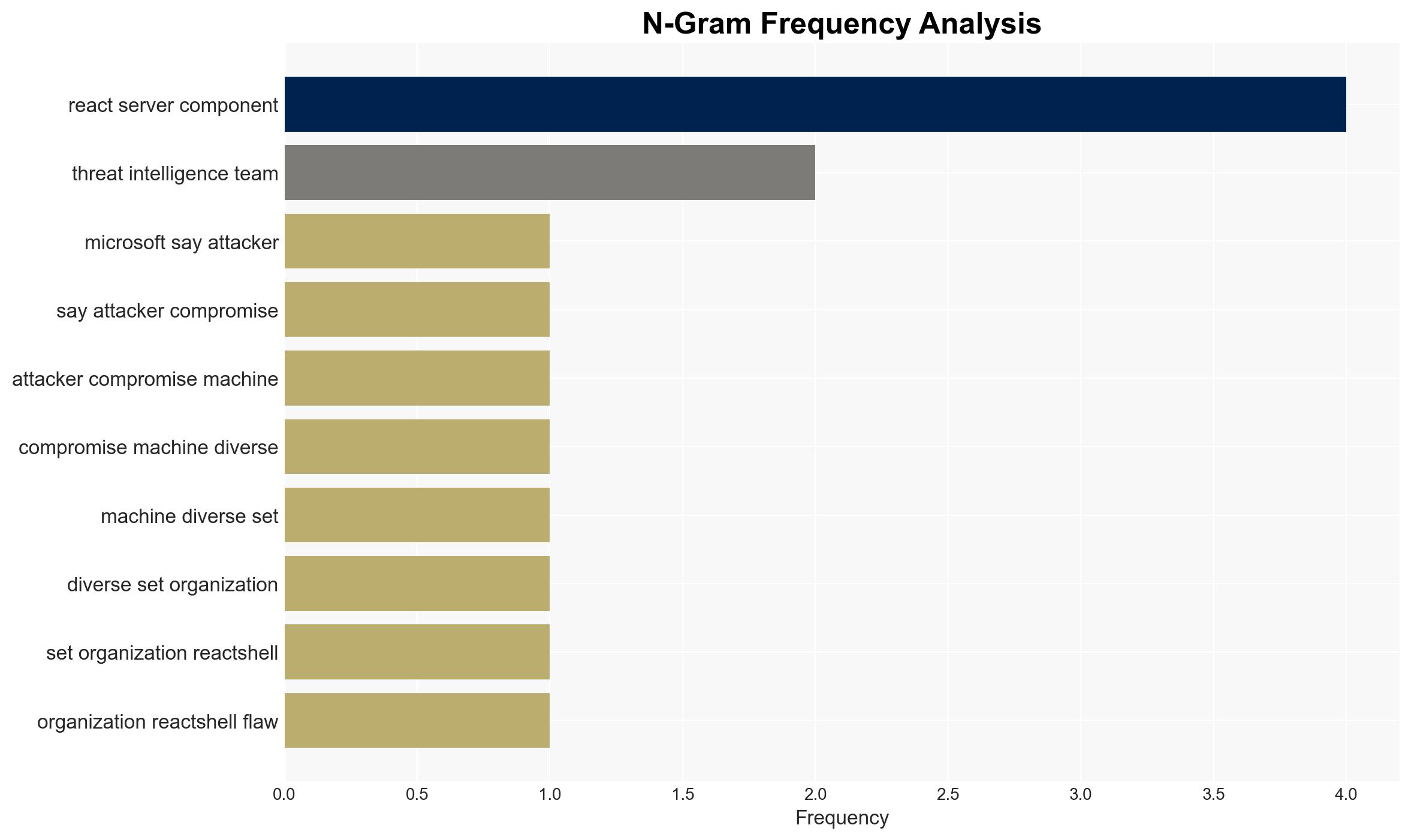
The React2Shell vulnerability is being actively exploited by threat actors, compromising hundreds of machines across various sectors. The exploitation is primarily used for deploying malware and ransomware, indicating a significant threat to organizations using React Server Components. This assessment is made with moderate confidence, given the rapid spread and diverse impact of the exploitation.
2. Competing Hypotheses
- Hypothesis A: The React2Shell exploitation is primarily driven by financially motivated threat actors seeking to deploy ransomware and cryptominers. This is supported by reports of ransomware deployment and the financial motivations of observed threat actors. However, the full extent of actor motivations remains uncertain.
- Hypothesis B: The exploitation is part of a broader state-sponsored cyber-espionage campaign, potentially linked to China and Iran, aiming to gather intelligence or disrupt operations. This is supported by early links to China and Iran-nexus activity, but there is limited direct evidence of state sponsorship.
- Assessment: Hypothesis A is currently better supported due to the observed financial motivations and the use of ransomware. Future indicators such as attribution to specific state actors or shifts in targeting could alter this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The exploitation is primarily financially motivated; React Server Components are widely adopted; the vulnerability is not yet fully patched across all affected systems.
- Information Gaps: Specific attribution to threat actor groups; comprehensive data on the full scope of affected organizations; detailed analysis of the malware payloads used.
- Bias & Deception Risks: Potential bias in attributing activity to state actors without conclusive evidence; risk of over-reliance on vendor-reported data without independent verification.
4. Implications and Strategic Risks
The ongoing exploitation of React2Shell could lead to increased financial losses and operational disruptions for affected organizations. The widespread adoption of React Server Components exacerbates the potential impact.
- Political / Geopolitical: Potential for increased tensions if state-sponsored involvement is confirmed, particularly involving China or Iran.
- Security / Counter-Terrorism: Heightened threat environment for organizations using vulnerable systems, with increased risk of ransomware attacks.
- Cyber / Information Space: Escalation in cyber threat landscape; potential for further exploitation of related vulnerabilities.
- Economic / Social: Potential economic impact on affected businesses; increased demand for cybersecurity solutions and expertise.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch vulnerable systems; enhance monitoring for signs of exploitation; engage with cybersecurity firms for threat intelligence sharing.
- Medium-Term Posture (1–12 months): Develop resilience measures, including incident response plans; foster partnerships with cybersecurity entities; invest in capability development for threat detection and response.
- Scenario Outlook:
- Best: Rapid patching and mitigation efforts reduce exploitation incidents significantly.
- Worst: Continued exploitation leads to widespread operational disruptions and significant financial losses.
- Most-Likely: Ongoing exploitation with periodic spikes as new vulnerabilities or attack vectors are discovered.
6. Key Individuals and Entities
- Microsoft (Threat Intelligence Team)
- S-RM (Security Firm)
- Andrew Morris (Founder of GreyNoise)
- Not clearly identifiable from open sources in this snippet for specific threat actors.
7. Thematic Tags
cybersecurity, ransomware, vulnerability exploitation, threat intelligence, state-sponsored activity, financial crime, cyber-espionage
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us