Microsoft revokes 200 certs used to sign malicious Teams installers – Help Net Security
Published on: 2025-10-17
Intelligence Report: Microsoft revokes 200 certs used to sign malicious Teams installers – Help Net Security
1. BLUF (Bottom Line Up Front)
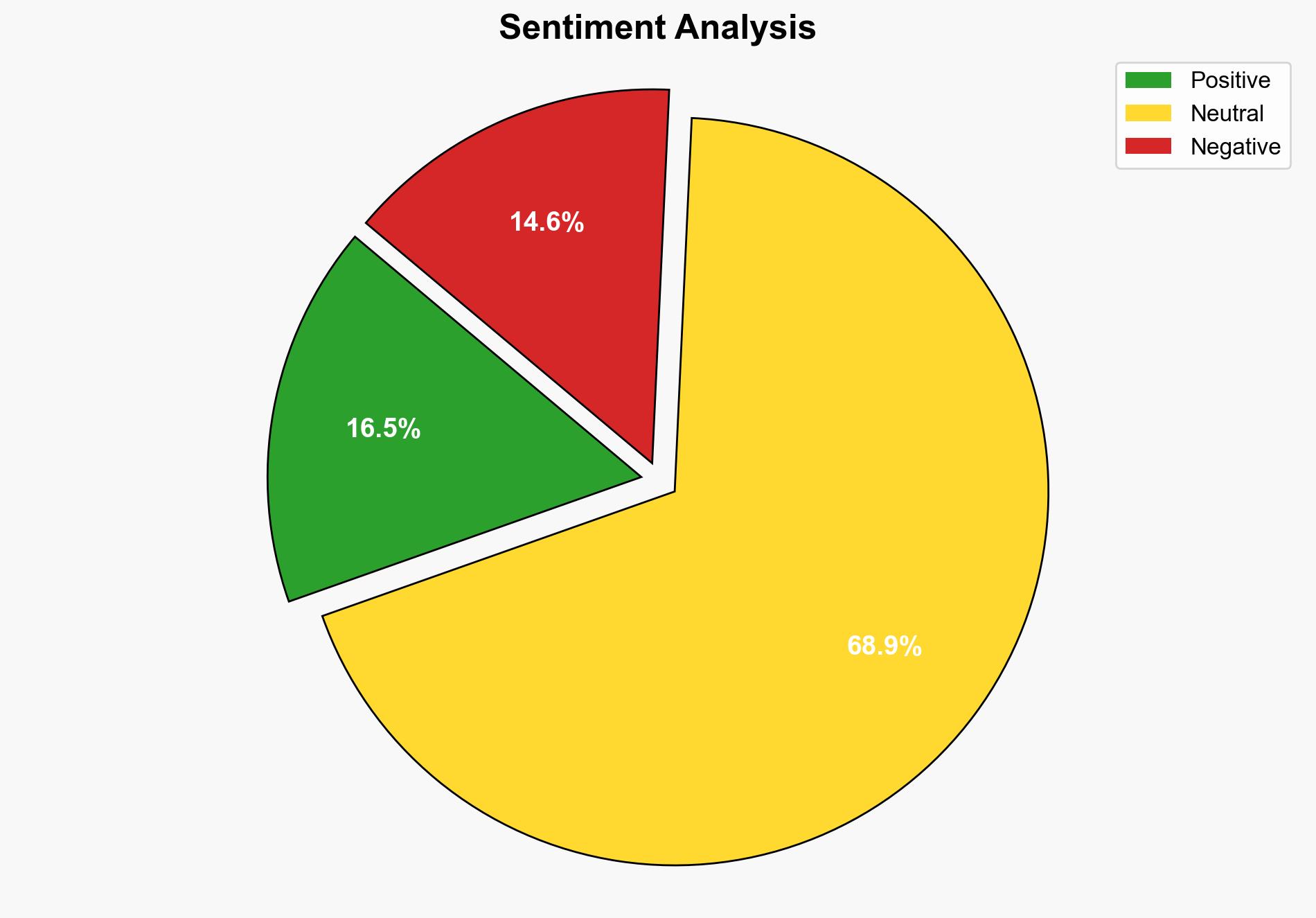
Microsoft’s revocation of 200 certificates used to sign malicious Teams installers highlights a significant cybersecurity threat posed by the group known as Vanilla Tempest. The most supported hypothesis is that Vanilla Tempest is strategically evolving its tactics to exploit trusted platforms for ransomware deployment. Confidence in this assessment is moderate due to the complexity and evolving nature of cyber threats. Recommended actions include enhanced monitoring of certificate usage and bolstering defenses against ransomware.
2. Competing Hypotheses
Hypothesis 1: Vanilla Tempest is deliberately targeting Microsoft Teams to exploit its widespread use in organizations, aiming to maximize the impact of their ransomware campaigns.
Hypothesis 2: The use of Microsoft Teams installers is opportunistic, with Vanilla Tempest leveraging any available platform to distribute their malware, indicating a broader, less targeted approach.
Using Analysis of Competing Hypotheses (ACH), Hypothesis 1 is better supported due to the specific targeting of Microsoft Teams and the strategic use of SEO poisoning to direct users to malicious sites, suggesting a calculated effort to exploit a trusted platform.
3. Key Assumptions and Red Flags
Assumptions:
– Vanilla Tempest has the capability to consistently exploit trusted platforms.
– The revocation of certificates will significantly disrupt their operations.
Red Flags:
– Lack of detailed information on how Vanilla Tempest obtained the certificates.
– Potential underestimation of Vanilla Tempest’s ability to adapt to certificate revocation.
Blind Spots:
– The full scope of Vanilla Tempest’s network and potential collaborators remains unclear.
4. Implications and Strategic Risks
The incident underscores the vulnerability of trusted platforms to exploitation by sophisticated threat actors. If not mitigated, this could lead to increased ransomware attacks, causing economic damage and undermining trust in digital communication tools. The potential for similar tactics to be adopted by other groups poses a broader cybersecurity risk.
5. Recommendations and Outlook
- Enhance monitoring and validation of software certificates to prevent misuse.
- Implement robust user education programs to recognize and avoid phishing attempts.
- Scenario Projections:
- Best Case: Effective mitigation strategies prevent further exploitation of trusted platforms.
- Worst Case: Widespread adoption of similar tactics by other threat actors leads to a surge in ransomware incidents.
- Most Likely: Continued attempts by Vanilla Tempest to adapt and exploit other vulnerabilities.
6. Key Individuals and Entities
Vanilla Tempest (also known as Vice Spider, Vice Society) is the primary entity involved. No specific individuals are named in the intelligence.
7. Thematic Tags
national security threats, cybersecurity, ransomware, digital trust, threat actor tactics