Microsoft server hack has hit about 100 victims researcher says – The Times of India
Published on: 2025-07-21
Intelligence Report: Microsoft Server Hack Affects Approximately 100 Victims – The Times of India
1. BLUF (Bottom Line Up Front)
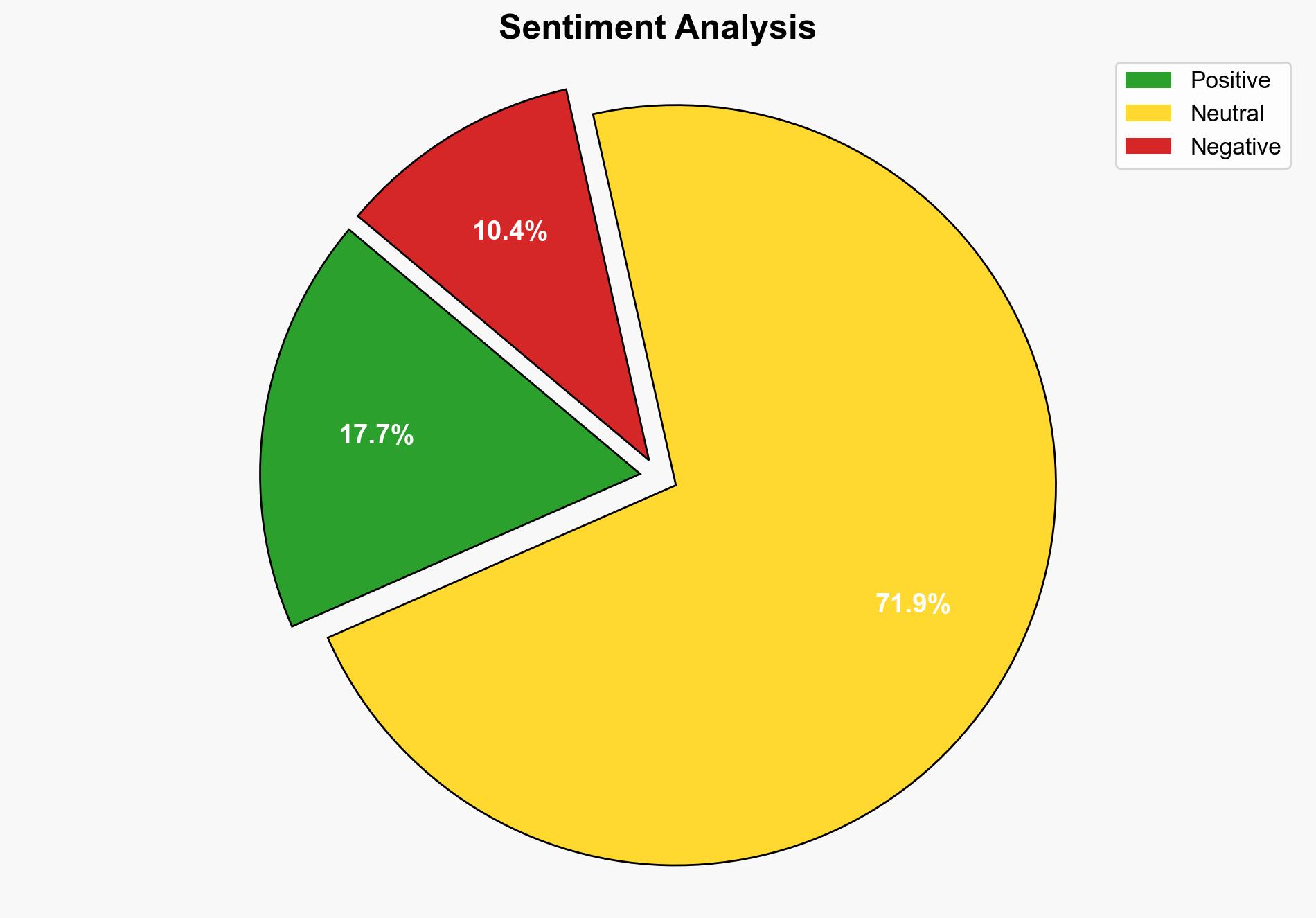
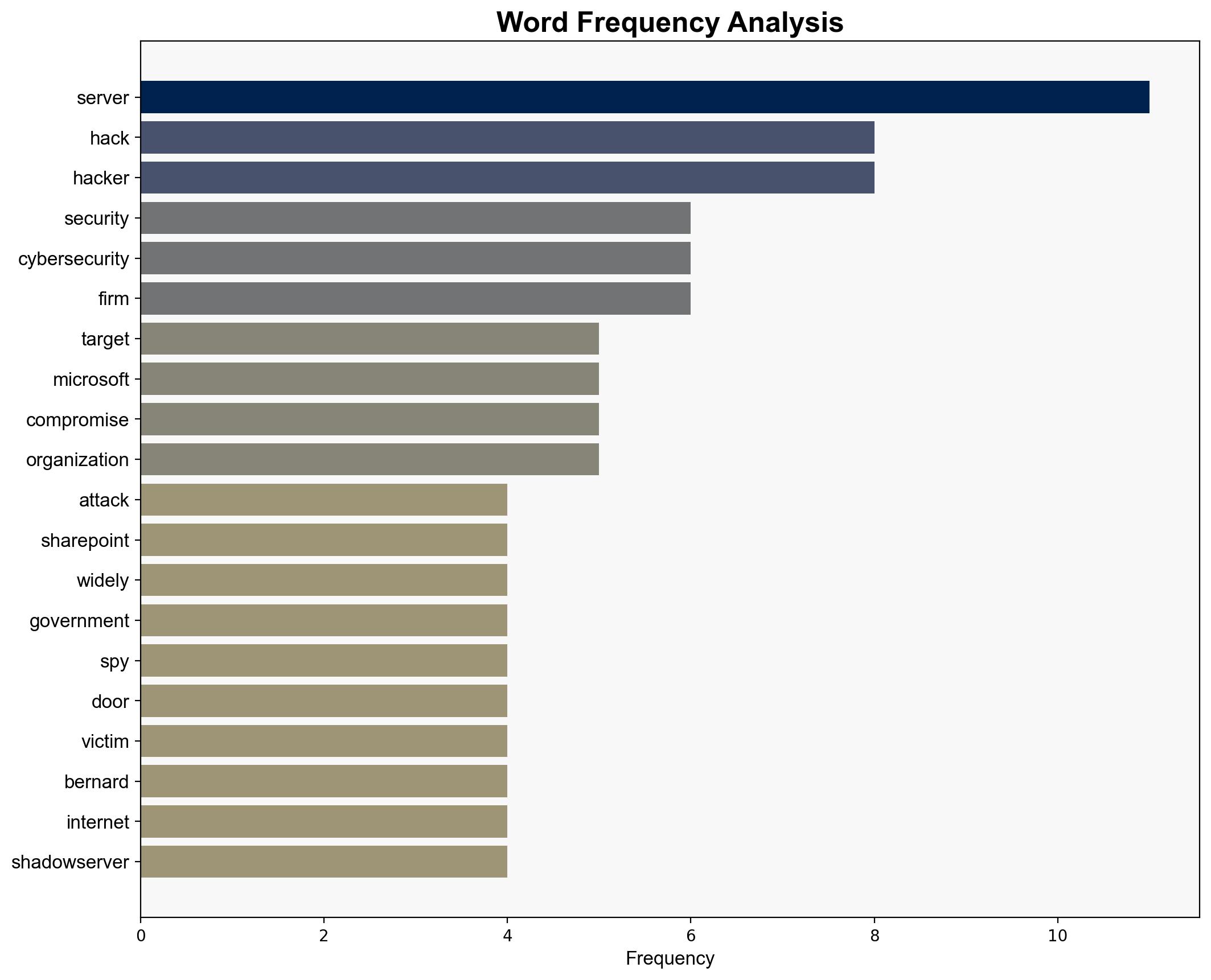
A cyberespionage operation has compromised Microsoft server software, affecting around 100 organizations globally. The attack exploits a zero-day vulnerability in self-managed SharePoint servers, potentially allowing persistent unauthorized access. Immediate action is required to mitigate risks and secure affected systems.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Cognitive Bias Stress Test
Potential biases were addressed by considering alternative hypotheses and employing red teaming to challenge initial assessments. This approach confirmed the likelihood of a sophisticated, targeted cyberespionage campaign.
Bayesian Scenario Modeling
Probabilistic forecasting suggests a moderate likelihood of further escalation if vulnerabilities remain unpatched, with potential for increased targeting of high-value sectors.
Network Influence Mapping
Analysis indicates a coordinated effort possibly involving state-sponsored actors, given the strategic targeting of government agencies and critical infrastructure sectors.
3. Implications and Strategic Risks
The attack highlights significant vulnerabilities in widely used software systems, posing risks to national security and economic stability. The potential for cascading effects includes data breaches, intellectual property theft, and disruption of critical services. Cross-domain risks may involve economic espionage and geopolitical tensions.
4. Recommendations and Outlook
- Urgently apply Microsoft’s security updates to all vulnerable systems.
- Enhance monitoring and incident response capabilities to detect and mitigate unauthorized access.
- Conduct a comprehensive review of cybersecurity protocols and employee training programs.
- Scenario-based projections:
- Best Case: Rapid patch deployment and enhanced security measures prevent further breaches.
- Worst Case: Continued exploitation leads to significant data loss and operational disruptions.
- Most Likely: Short-term disruptions with gradual containment as patches are applied.
5. Key Individuals and Entities
Vaisha Bernard, Rafe Pilling
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus