Microsoft SharePoint server hack sees Chinese threat actor hit roughly 100 orgs – heres what we know so far – TechRadar
Published on: 2025-07-22
Intelligence Report: Microsoft SharePoint Server Hack by Chinese Threat Actor
1. BLUF (Bottom Line Up Front)
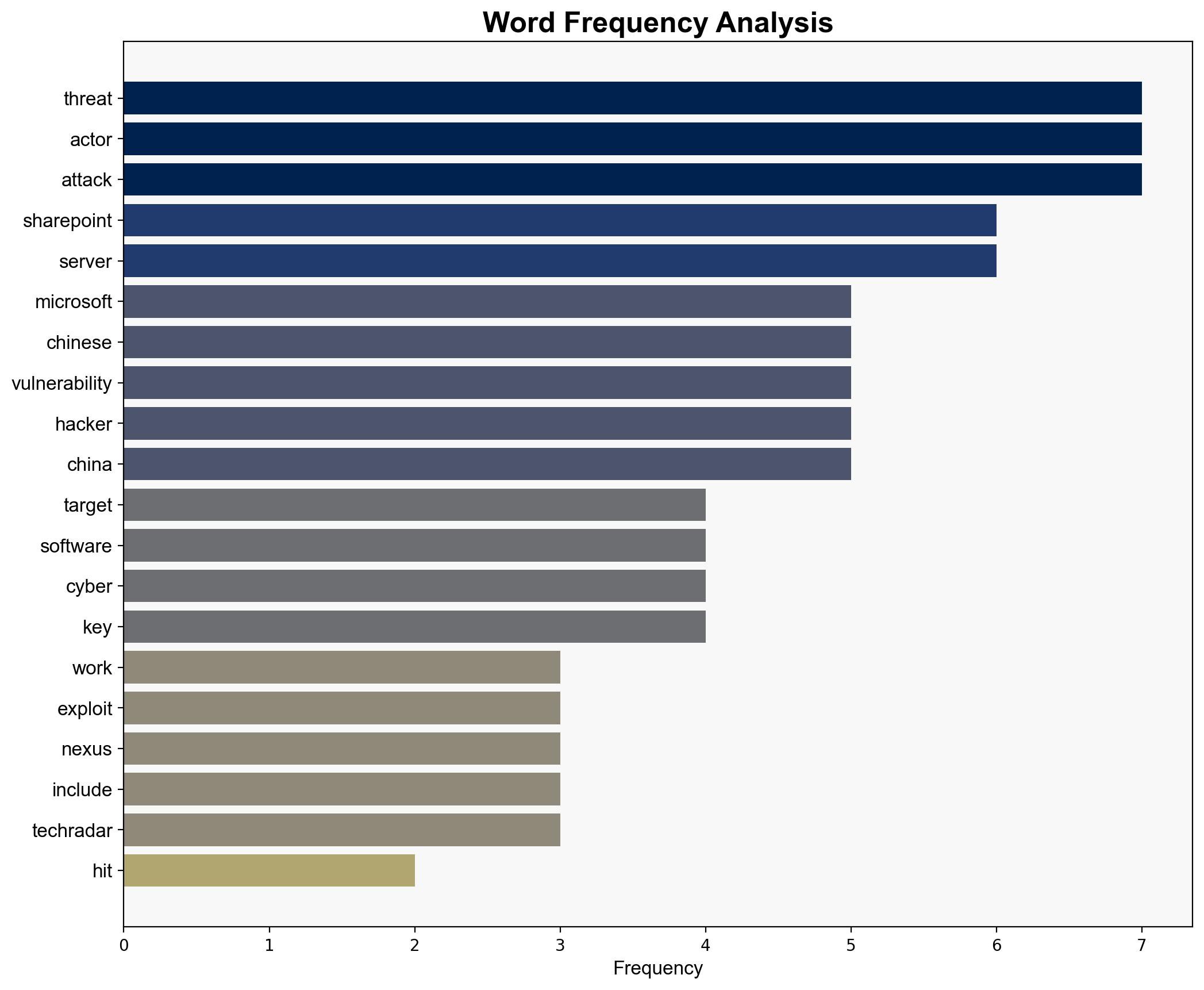
A cyberattack exploiting a Microsoft SharePoint vulnerability has been attributed to a China-nexus threat actor, impacting approximately 100 organizations, including government agencies and private firms. Immediate patching and security measures are recommended to mitigate further risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The attack demonstrates a sophisticated understanding of Microsoft SharePoint vulnerabilities, likely involving reconnaissance and targeted exploitation. Simulating similar adversarial tactics can help anticipate future vulnerabilities and enhance defense mechanisms.
Indicators Development
Key indicators include unusual access patterns, unauthorized data extraction, and cryptographic key manipulation. Monitoring these can provide early warnings of potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued exploitation of unpatched systems, with potential expansion to other software vulnerabilities as threat actors diversify their tactics.
3. Implications and Strategic Risks
The attack underscores significant cybersecurity vulnerabilities within critical infrastructure and private sectors. It highlights the potential for cyberespionage and data theft, posing risks to national security and economic stability. The denial by the Chinese embassy suggests potential diplomatic tensions.
4. Recommendations and Outlook
- Immediate application of Microsoft’s security patch across all vulnerable systems.
- Conduct thorough security audits and rotate machine keys to prevent unauthorized access.
- Deploy advanced antimalware solutions and enhance monitoring for anomalous activities.
- Scenario-based projections:
- Best Case: Rapid patch deployment and enhanced security measures prevent further breaches.
- Worst Case: Continued exploitation leads to significant data breaches and geopolitical tensions.
- Most Likely: Incremental improvements in security posture reduce immediate risks but require ongoing vigilance.
5. Key Individuals and Entities
Charles Carmakal
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus