Microsoft to Retire Vulnerable RC4 Encryption Cipher After Years of Exploitation and Criticism
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Will Finally Kill an Encryption Cipher That Enabled a Decade of Windows Hacks
1. BLUF (Bottom Line Up Front)
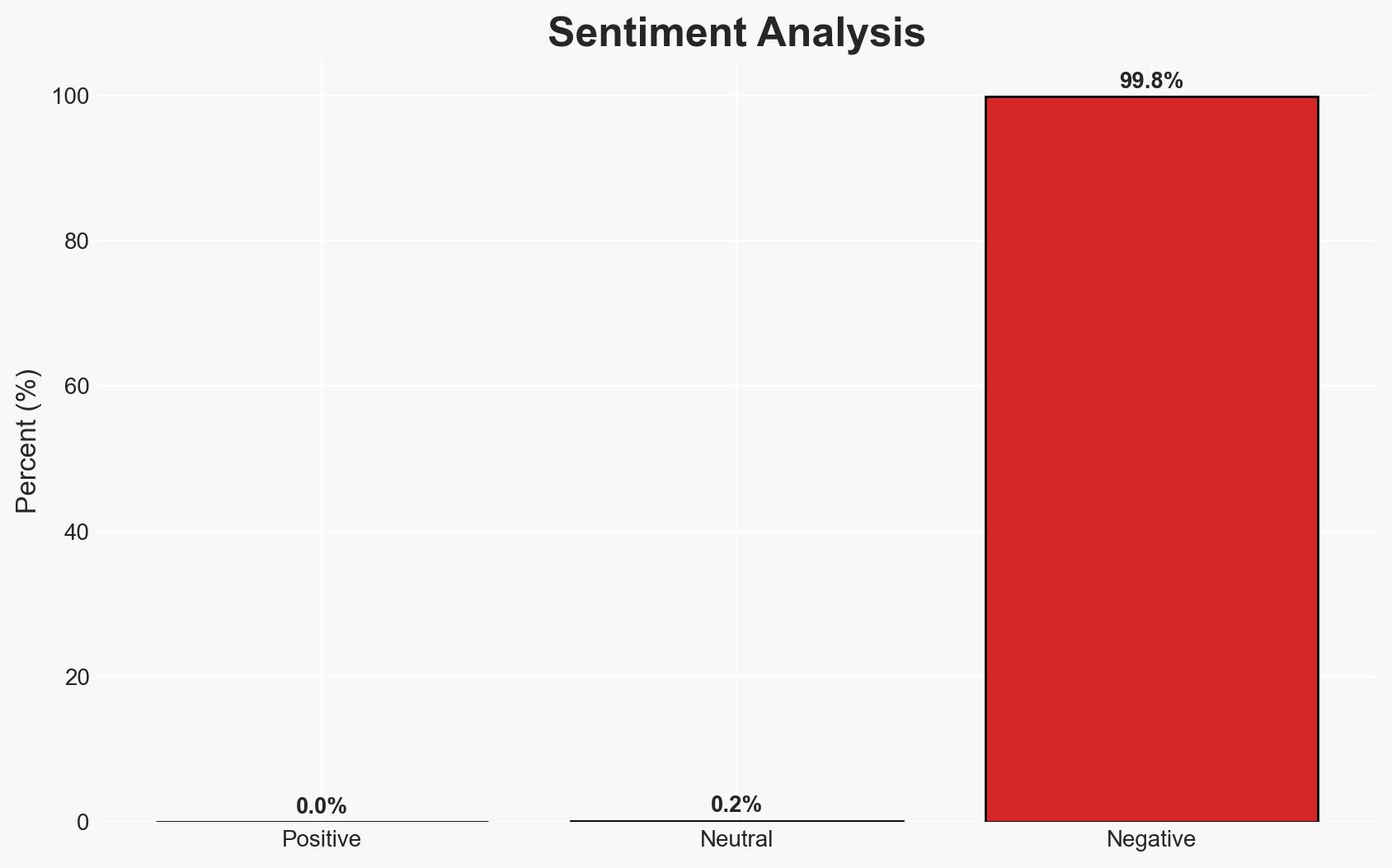
Microsoft’s decision to disable the RC4 encryption cipher by default addresses longstanding vulnerabilities exploited in numerous cyberattacks. This move is likely to enhance the security of Windows-based systems, particularly in enterprise environments. The change is driven by both technical necessity and external pressure, including criticism from U.S. policymakers. Overall, this assessment is made with moderate confidence, given the historical context and the planned timeline for implementation.
2. Competing Hypotheses
- Hypothesis A: Microsoft is disabling RC4 primarily due to technical vulnerabilities and the need to protect its user base from known exploits. Supporting evidence includes the historical weaknesses of RC4 and its role in recent high-profile breaches. However, the timeline for implementation suggests a gradual approach, which may indicate internal challenges or resource constraints.
- Hypothesis B: The decision is largely influenced by external pressures, such as criticism from policymakers and potential regulatory actions. The recent call for investigation by a U.S. senator supports this view. However, Microsoft’s prior updates to support AES suggest a longstanding awareness of the issue.
- Assessment: Hypothesis A is currently better supported due to the technical history of RC4 vulnerabilities and Microsoft’s incremental updates towards more secure encryption standards. Key indicators that could shift this judgment include changes in regulatory actions or additional public pressure.
3. Key Assumptions and Red Flags
- Assumptions: Microsoft has the technical capability to implement the change effectively; AES-SHA1 is sufficiently secure for current threat landscapes; enterprises will adopt the changes without significant disruption.
- Information Gaps: Detailed timelines for full implementation across all Microsoft products; specific enterprise readiness for the transition; potential undisclosed vulnerabilities in AES-SHA1.
- Bias & Deception Risks: Potential bias from Microsoft’s public statements minimizing the impact of RC4 vulnerabilities; lack of transparency in the decision-making process could obscure true motivations.
4. Implications and Strategic Risks
This development could lead to a more secure enterprise environment, reducing the risk of cyberattacks exploiting RC4. However, the transition period may expose vulnerabilities if not managed effectively.
- Political / Geopolitical: Increased scrutiny on tech companies’ cybersecurity practices; potential for regulatory actions if vulnerabilities persist.
- Security / Counter-Terrorism: Reduced attack surface for cybercriminals and state actors exploiting RC4; potential shift in attack vectors.
- Cyber / Information Space: Encouragement for other tech companies to phase out outdated encryption methods; potential increase in cyber hygiene awareness.
- Economic / Social: Potential short-term costs for enterprises updating systems; long-term benefits from reduced breach incidents.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor Microsoft’s implementation progress; encourage enterprises to audit systems for RC4 dependencies.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance threat detection; invest in training for IT staff on new encryption standards.
- Scenario Outlook: Best: Smooth transition with enhanced security; Worst: Delays or vulnerabilities in AES-SHA1; Most-Likely: Gradual improvement with some transitional challenges.
6. Key Individuals and Entities
- Microsoft
- US Senator Ron Wyden
- Matthew Palko, Microsoft Principal Program Manager
- Ascension (Health Giant)
7. Thematic Tags
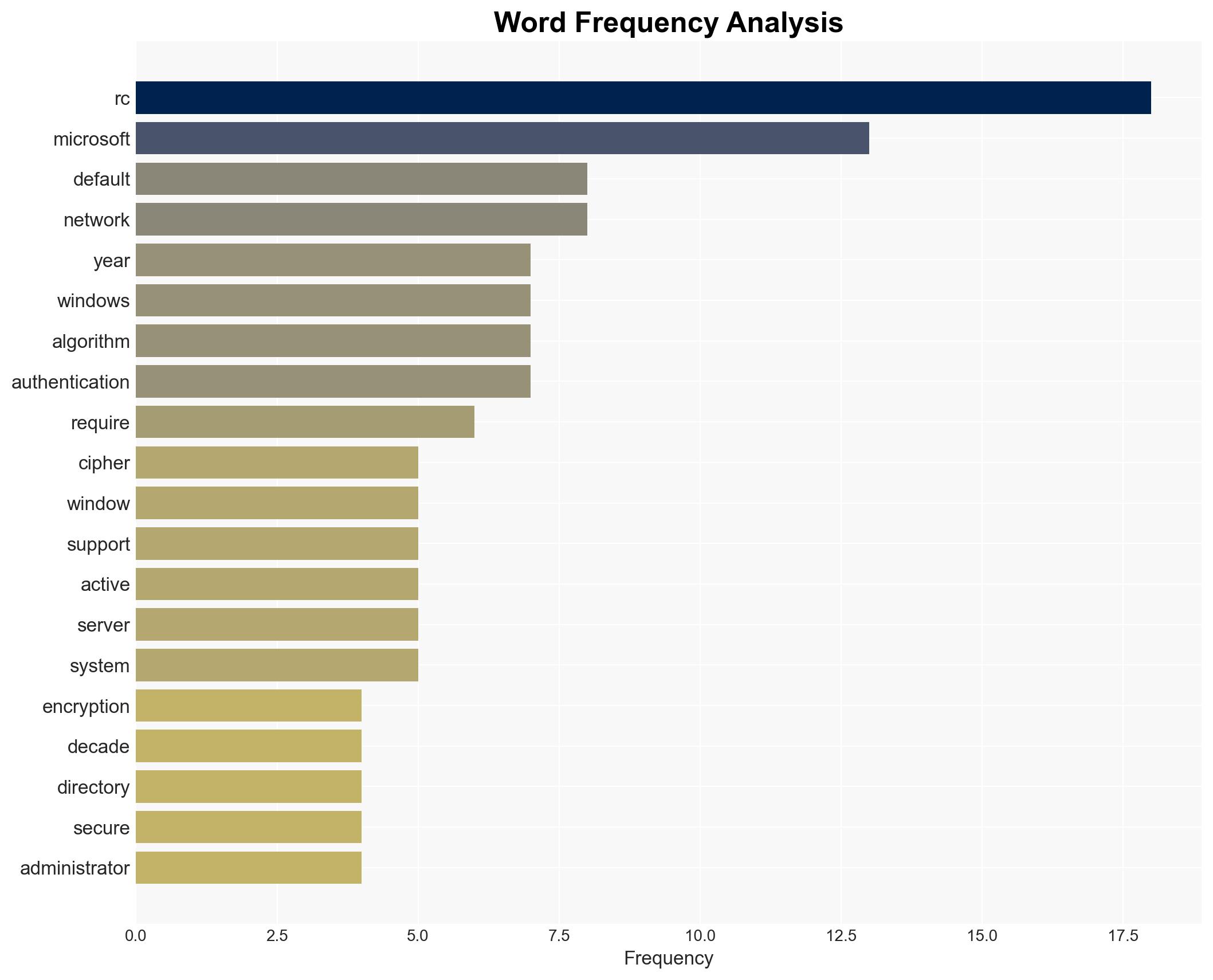
cybersecurity, encryption, Microsoft, RC4, AES, regulatory pressure, enterprise security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us