Microsoft Unveils Defender Experts Suite to Strengthen Cybersecurity with Expert Services and Integrated Solu…
Published on: 2026-01-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Introducing the Microsoft Defender Experts Suite Elevate your security with expert-led services
1. BLUF (Bottom Line Up Front)
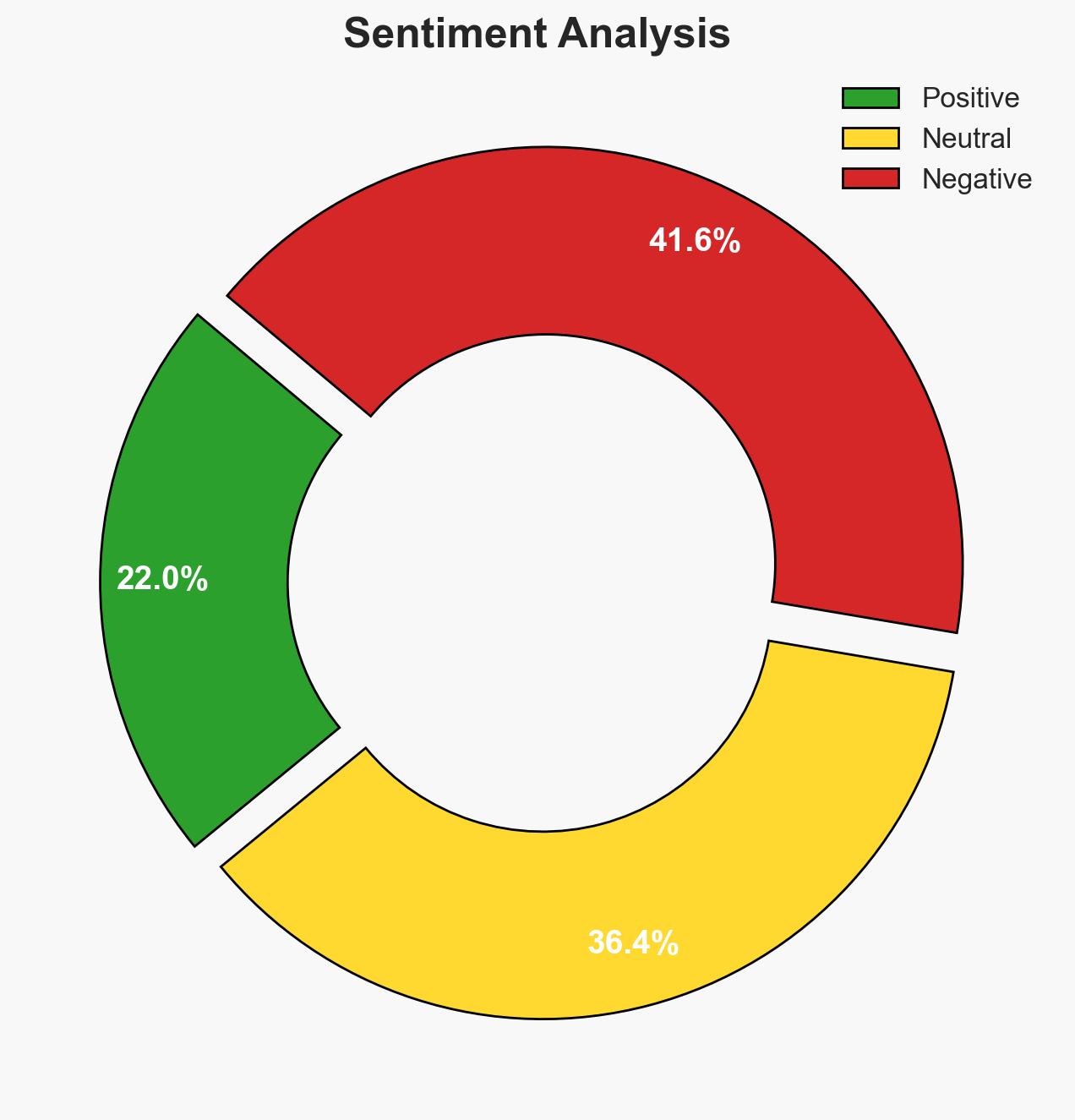
The introduction of the Microsoft Defender Experts Suite addresses the growing need for advanced cybersecurity solutions as AI-powered cyberattacks increase in complexity and frequency. This service aims to enhance organizational resilience and security operations, particularly benefiting those lacking adequate cybersecurity resources. Overall confidence in this assessment is moderate due to limited information on the suite’s effectiveness and adoption rate.
2. Competing Hypotheses
- Hypothesis A: The Microsoft Defender Experts Suite will significantly enhance cybersecurity defenses for organizations, reducing the impact of AI-powered cyberattacks. This is supported by the comprehensive services offered, including proactive threat hunting and incident response. However, the effectiveness of these services in diverse organizational contexts remains uncertain.
- Hypothesis B: The suite may not substantially improve cybersecurity outcomes due to potential integration challenges and resource constraints within organizations. While the suite offers advanced features, its success depends on the ability of organizations to effectively implement and utilize these services.
- Assessment: Hypothesis A is currently better supported due to the suite’s comprehensive approach and Microsoft’s established reputation in cybersecurity. Key indicators that could shift this judgment include user feedback on integration challenges and measurable improvements in cybersecurity metrics.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have the necessary infrastructure to integrate the suite; Microsoft can maintain service quality at scale; AI-powered threats will continue to evolve.
- Information Gaps: Detailed case studies or metrics demonstrating the suite’s effectiveness; specific adoption rates across different sectors.
- Bias & Deception Risks: Potential bias in Microsoft’s promotional materials; lack of independent evaluations of the suite’s performance.
4. Implications and Strategic Risks
The deployment of the Microsoft Defender Experts Suite could lead to a shift in the cybersecurity landscape, influencing how organizations approach threat management and resilience.
- Political / Geopolitical: Enhanced cybersecurity capabilities could reduce vulnerabilities to state-sponsored cyberattacks, potentially altering geopolitical dynamics.
- Security / Counter-Terrorism: Improved defenses might deter cyberterrorism activities, but could also drive adversaries to develop more sophisticated attack vectors.
- Cyber / Information Space: The suite may set new standards for cybersecurity solutions, prompting competitors to innovate and improve their offerings.
- Economic / Social: Widespread adoption could lead to increased cybersecurity spending, impacting organizational budgets and potentially driving market growth in cybersecurity services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor early adopter feedback and case studies; assess integration challenges and initial performance metrics.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance threat intelligence sharing; invest in workforce training to maximize suite utilization.
- Scenario Outlook:
- Best: Widespread adoption leads to significant reductions in successful cyberattacks.
- Worst: Integration issues and high costs limit adoption, resulting in minimal impact on cybersecurity outcomes.
- Most-Likely: Moderate adoption with incremental improvements in organizational cybersecurity postures.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, AI-powered threats, Microsoft Defender, incident response, threat hunting, organizational resilience, cybersecurity services
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us