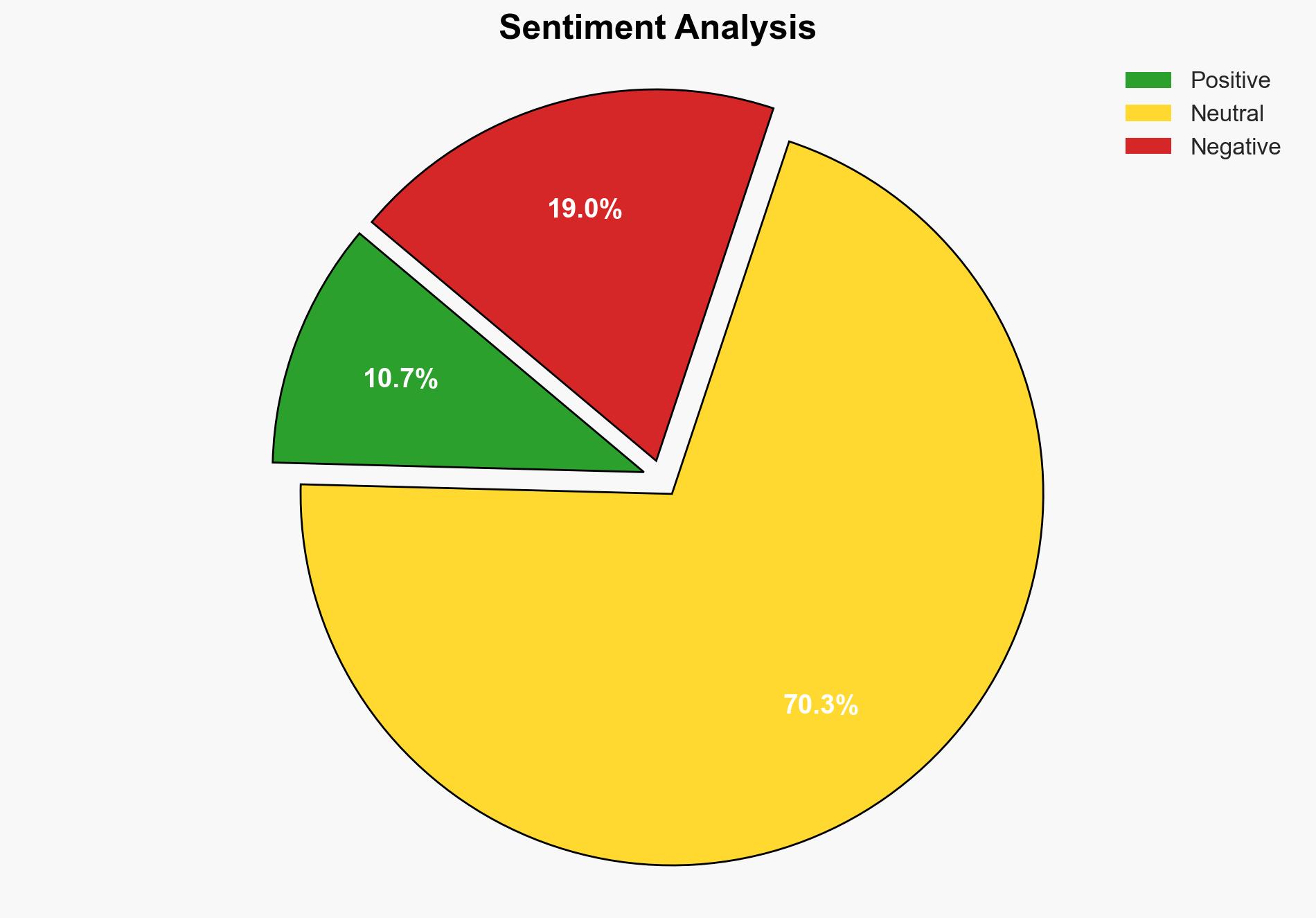
Microsoft Windows CLFS zero-day exploited by ransomware gang – BleepingComputer
Published on: 2025-04-08
Intelligence Report: Microsoft Windows CLFS zero-day exploited by ransomware gang – BleepingComputer
1. BLUF (Bottom Line Up Front)
A high-severity zero-day vulnerability in the Microsoft Windows Common Log File System (CLFS) has been exploited by the RansomEXX ransomware gang. This flaw, tracked as CVE, allows attackers to gain system privileges on victim systems. The exploitation has been observed in targeted attacks against sectors including technology, real estate, and finance in the United States, Venezuela, Spain, and Saudi Arabia. Microsoft has issued a security update and urges immediate application to mitigate risks.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The vulnerability in the Windows CLFS is being actively exploited by the RansomEXX gang, which has a history of targeting high-profile organizations. The exploitation involves the installation of the PipeMagic backdoor malware, allowing for further malicious activities such as data harvesting and lateral movement within networks. The vulnerability is characterized by its low complexity and does not require user interaction, making it a significant threat.
3. Implications and Strategic Risks
The exploitation of this vulnerability poses significant risks to national security and economic interests, particularly in the targeted sectors. The ability of attackers to gain system privileges can lead to data breaches, operational disruptions, and financial losses. The trend of targeting critical sectors suggests a strategic intent to undermine economic stability and technological infrastructure.
4. Recommendations and Outlook
Recommendations:
- Immediate application of the security update issued by Microsoft to all affected systems.
- Enhancement of network monitoring to detect and respond to suspicious activities promptly.
- Implementation of robust backup and recovery procedures to mitigate the impact of potential ransomware attacks.
- Consideration of regulatory measures to enforce timely patch management across critical sectors.
Outlook:
Best-case scenario: Rapid patch deployment curtails further exploitation, minimizing impact on targeted sectors.
Worst-case scenario: Delayed patching leads to widespread exploitation, resulting in significant economic and operational damage.
Most likely scenario: Mixed compliance with patching recommendations results in continued, albeit reduced, exploitation incidents.
5. Key Individuals and Entities
The report mentions significant individuals and organizations involved in the exploitation and mitigation efforts. Notable entities include Microsoft, RansomEXX, Kaspersky, and ESET. These entities play critical roles in both the threat landscape and the defensive measures being implemented.