Middle East Power Dynamics Shift from Geopolitics to Data Control in American Technology
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: From Sykes-Picot to Silicon Valley Why Middle East Fault Lines now run through American Tech
1. BLUF (Bottom Line Up Front)
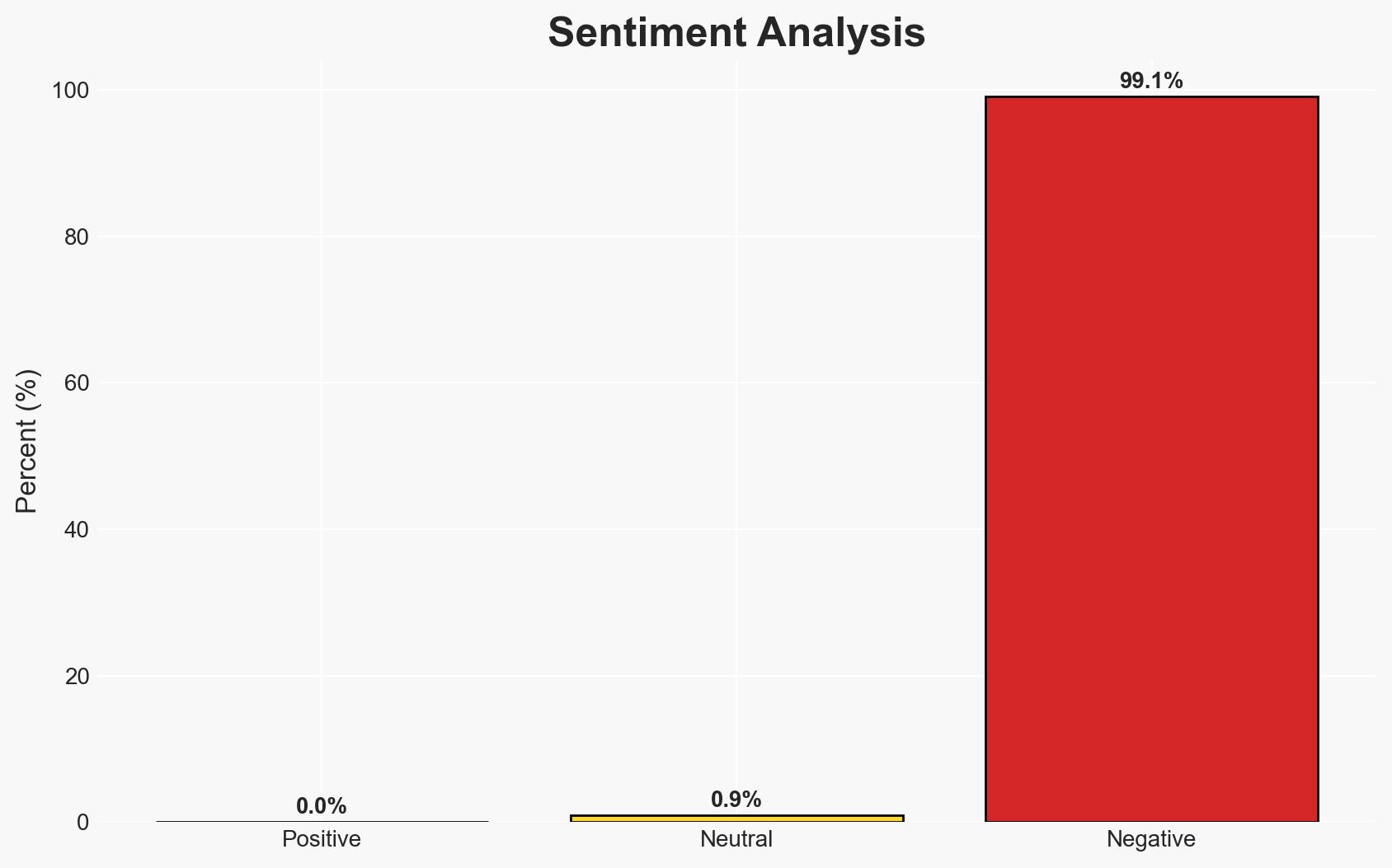
The integration of US technology into Middle Eastern state systems is reshaping power dynamics in the region, with significant implications for sovereignty and control. The most likely hypothesis is that technological influence is supplanting traditional military and geopolitical control, with moderate confidence. This shift affects regional governments, technology companies, and potentially, civil liberties.
2. Competing Hypotheses
- Hypothesis A: US technology is becoming the primary tool for Middle Eastern states to exert control, replacing traditional military and geopolitical methods. This is supported by the increasing use of surveillance and AI technologies for state control, though the extent of reliance on these technologies remains uncertain.
- Hypothesis B: The integration of US technology is a supplementary tool that enhances but does not replace traditional methods of control in the Middle East. Evidence includes ongoing military presence and geopolitical maneuvers, suggesting technology is an adjunct rather than a replacement.
- Assessment: Hypothesis A is currently better supported due to the strategic deployment of technology in state functions, indicating a paradigm shift. However, indicators such as changes in military deployments or geopolitical strategies could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Middle Eastern states have the capability to effectively integrate and utilize US technology; US technology companies will continue to engage with Middle Eastern governments; geopolitical tensions will not significantly disrupt technology flows.
- Information Gaps: Specific details on the extent of technology integration and its direct impact on governance and control; the role of non-state actors in this technological landscape.
- Bias & Deception Risks: Potential bias in reporting from technology companies and Middle Eastern states; risk of deception in the portrayal of technology’s effectiveness or scope.
4. Implications and Strategic Risks
This development could lead to a redefinition of sovereignty and control in the Middle East, with technology becoming a central element of state power. Over time, this may alter regional alliances and power structures.
- Political / Geopolitical: Potential shifts in alliances as states seek technological partnerships; increased influence of tech companies in regional politics.
- Security / Counter-Terrorism: Enhanced state surveillance capabilities could alter threat landscapes and counter-terrorism strategies.
- Cyber / Information Space: Increased cyber dependencies may heighten vulnerabilities to cyber-attacks and information manipulation.
- Economic / Social: Economic benefits for tech companies; potential social unrest due to increased surveillance and control measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor technology agreements and deployments in the region; assess potential impacts on civil liberties and regional stability.
- Medium-Term Posture (1–12 months): Develop resilience measures against potential cyber vulnerabilities; foster partnerships with technology firms to ensure ethical use of technology.
- Scenario Outlook:
- Best: Technology enhances governance without infringing on civil liberties, fostering regional stability.
- Worst: Technology exacerbates authoritarian control, leading to increased unrest and geopolitical tensions.
- Most-Likely: Gradual integration of technology reshapes power dynamics, with mixed impacts on governance and civil liberties.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
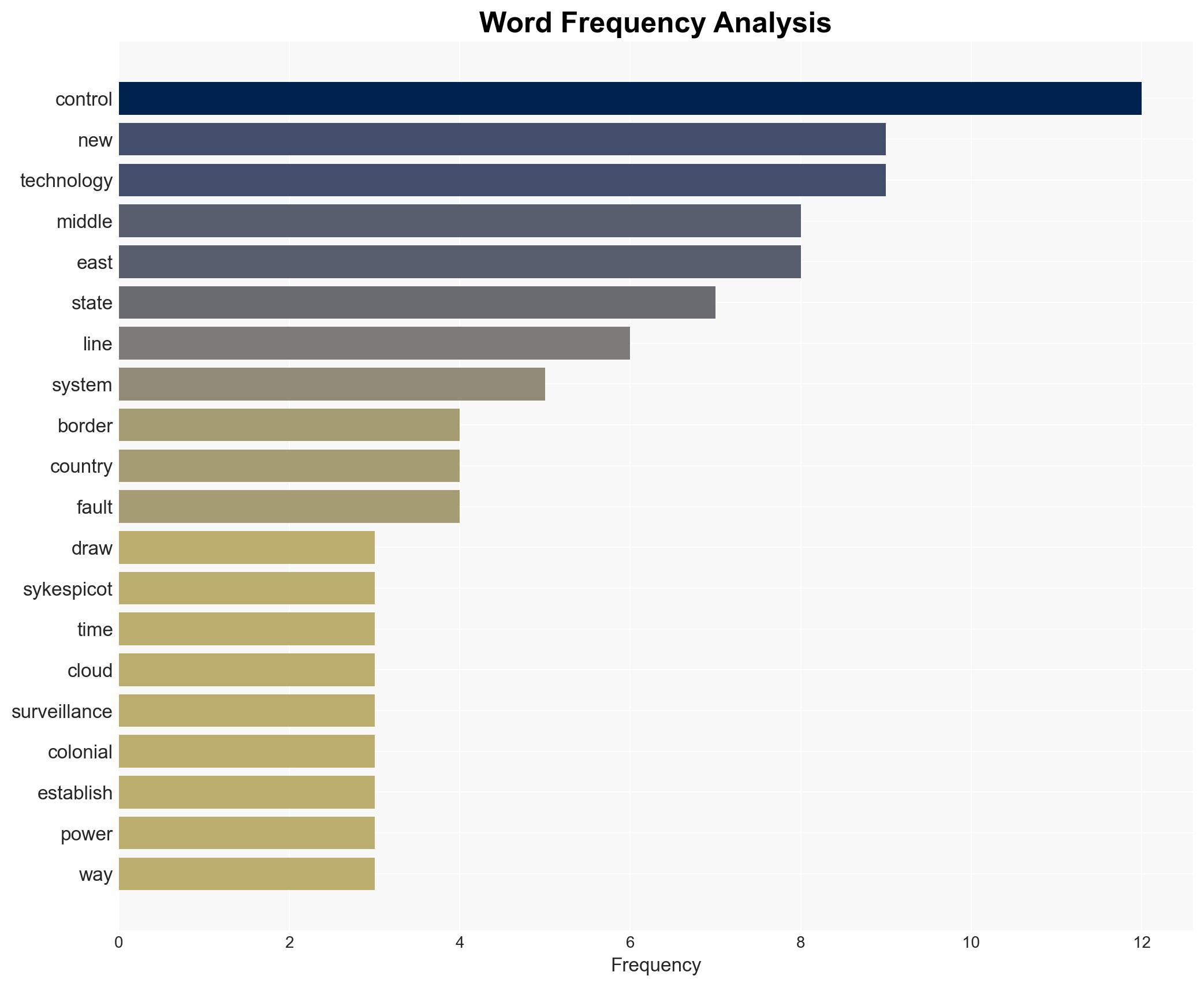
regional conflicts, Middle East, US technology, surveillance, sovereignty, geopolitical dynamics, cyber-security, state control
Structured Analytic Techniques Applied
- Causal Layered Analysis (CLA): Analyze events across surface happenings, systems, worldviews, and myths.
- Cross-Impact Simulation: Model ripple effects across neighboring states, conflicts, or economic dependencies.
- Scenario Generation: Explore divergent futures under varying assumptions to identify plausible paths.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Regional Conflicts Briefs ·
Daily Summary ·
Support us