Minnesota Man Becomes Third to Admit Guilt in Major Fantasy Sports Betting Cyberattack
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Third Defendant Pleads Guilty in Fantasy Sports Betting Hack Case
1. BLUF (Bottom Line Up Front)
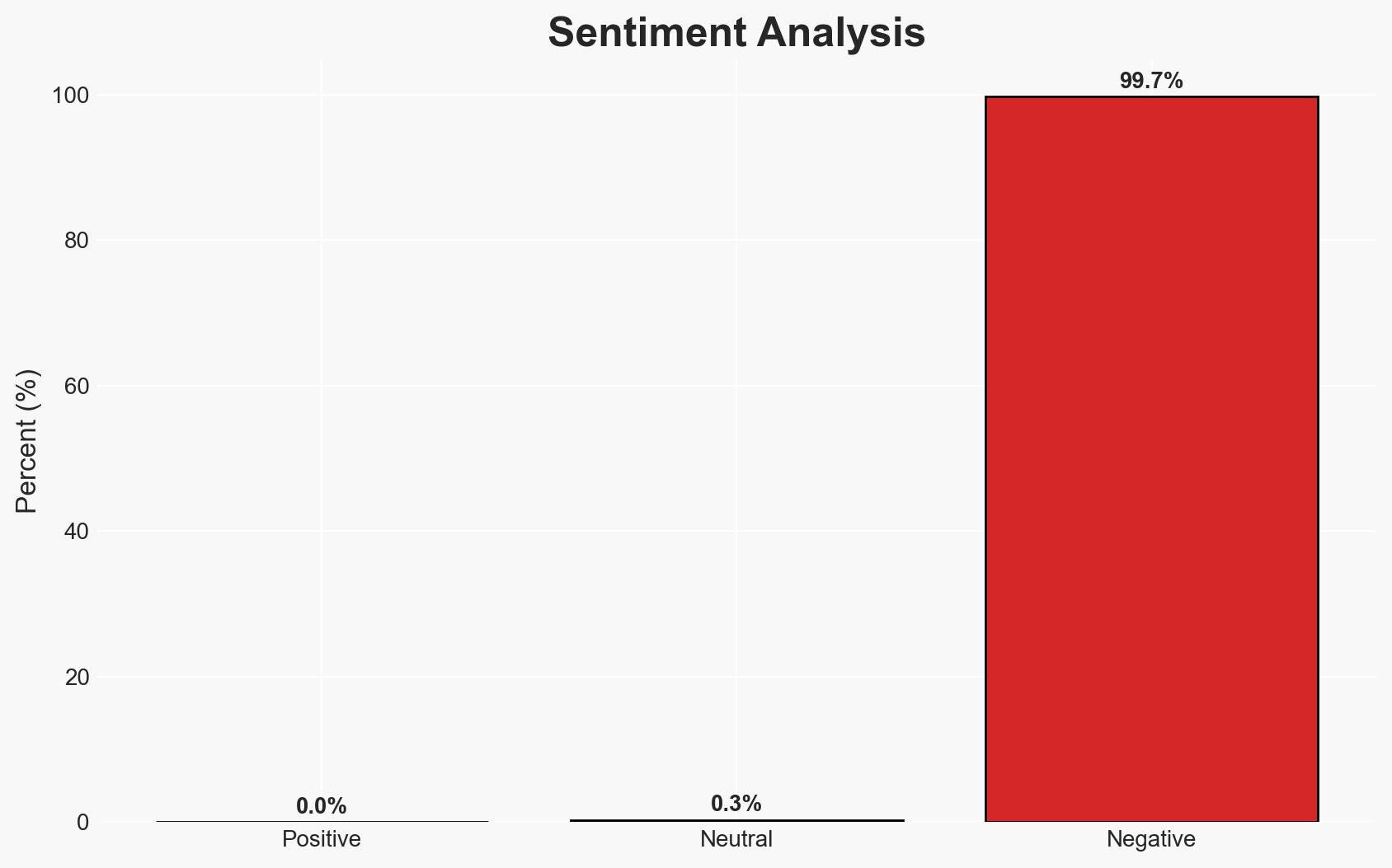
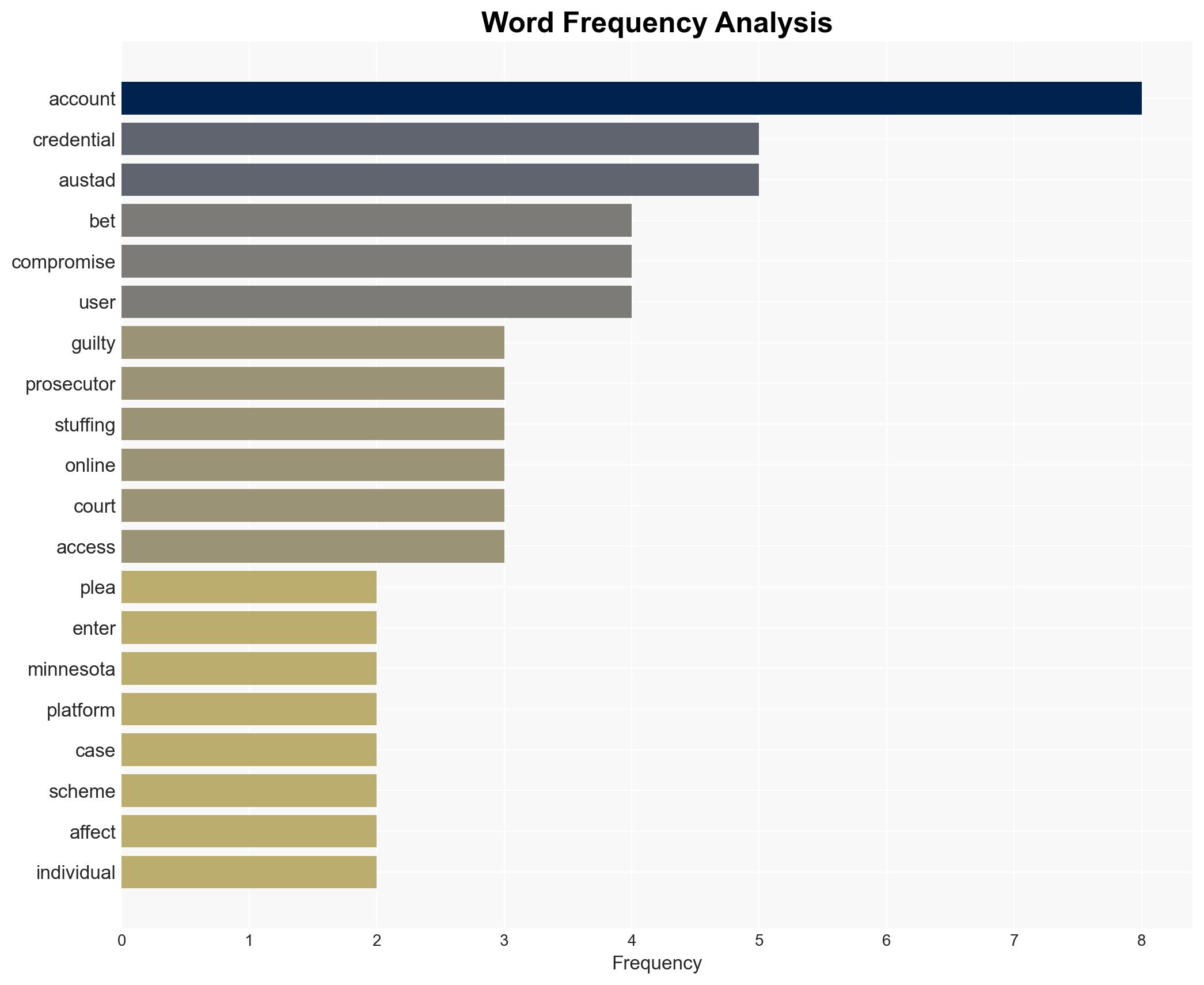
The guilty plea of Nathan Austad in the cyber-attack on a fantasy sports betting platform highlights the vulnerabilities of online services to credential stuffing attacks. This case underscores the need for enhanced cybersecurity measures across similar platforms. The most likely hypothesis is that this was a financially motivated cybercrime operation exploiting weak password practices. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was primarily financially motivated, targeting the betting platform to exploit weak user password practices for monetary gain. Supporting evidence includes the use of credential stuffing and the financial transactions linked to Austad. Key uncertainties include the full extent of the network and any potential state or non-state actor involvement.
- Hypothesis B: The attack may have been part of a broader campaign to disrupt online betting platforms, possibly involving ideological motives. While the financial gain is evident, there is no direct evidence of ideological motives, making this hypothesis less supported.
- Assessment: Hypothesis A is currently better supported due to the clear financial transactions and the modus operandi of credential stuffing aimed at monetary theft. Indicators that could shift this judgment include evidence of communications suggesting ideological motives or links to larger disruptive campaigns.
3. Key Assumptions and Red Flags
- Assumptions: The primary motivation was financial gain; Austad’s guilty plea reflects accurate involvement; the attack was not state-sponsored.
- Information Gaps: Details on other potential co-conspirators; the full scale of the financial network and its beneficiaries; the exact security measures of the compromised platform.
- Bias & Deception Risks: Potential bias in focusing solely on financial motives without considering broader implications; reliance on court documents which may not capture the full scope of the operation.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on cybersecurity practices within the online betting industry and potentially inspire similar attacks if vulnerabilities remain unaddressed.
- Political / Geopolitical: Minimal direct implications, but potential for increased regulatory pressure on online platforms.
- Security / Counter-Terrorism: Highlights the need for improved cybersecurity measures to prevent similar attacks, though not directly linked to terrorism.
- Cyber / Information Space: Demonstrates the effectiveness of credential stuffing and the need for better user authentication practices.
- Economic / Social: Financial losses for affected users and potential reputational damage to the platform, which could impact user trust and engagement.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor similar platforms for signs of credential stuffing; enhance user education on password security; engage with cybersecurity firms for immediate threat assessments.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity experts to improve defenses; implement multi-factor authentication across platforms; conduct regular security audits.
- Scenario Outlook:
- Best: Enhanced security measures prevent further attacks, restoring user confidence.
- Worst: Continued attacks lead to significant financial and reputational damage.
- Most-Likely: Incremental improvements in security reduce attack frequency but do not eliminate the threat entirely.
6. Key Individuals and Entities
- Nathan Austad (aka “Snoopy”), Joseph Garrison, Kamerin Stokes
- DraftKings (implied affected entity)
7. Thematic Tags
cybersecurity, credential stuffing, online betting, financial crime, digital assets, cybercrime, user authentication
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us