Mirai botnets exploit Wazuh RCE Akamai warned – Securityaffairs.com
Published on: 2025-06-10
Intelligence Report: Mirai botnets exploit Wazuh RCE Akamai warned – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
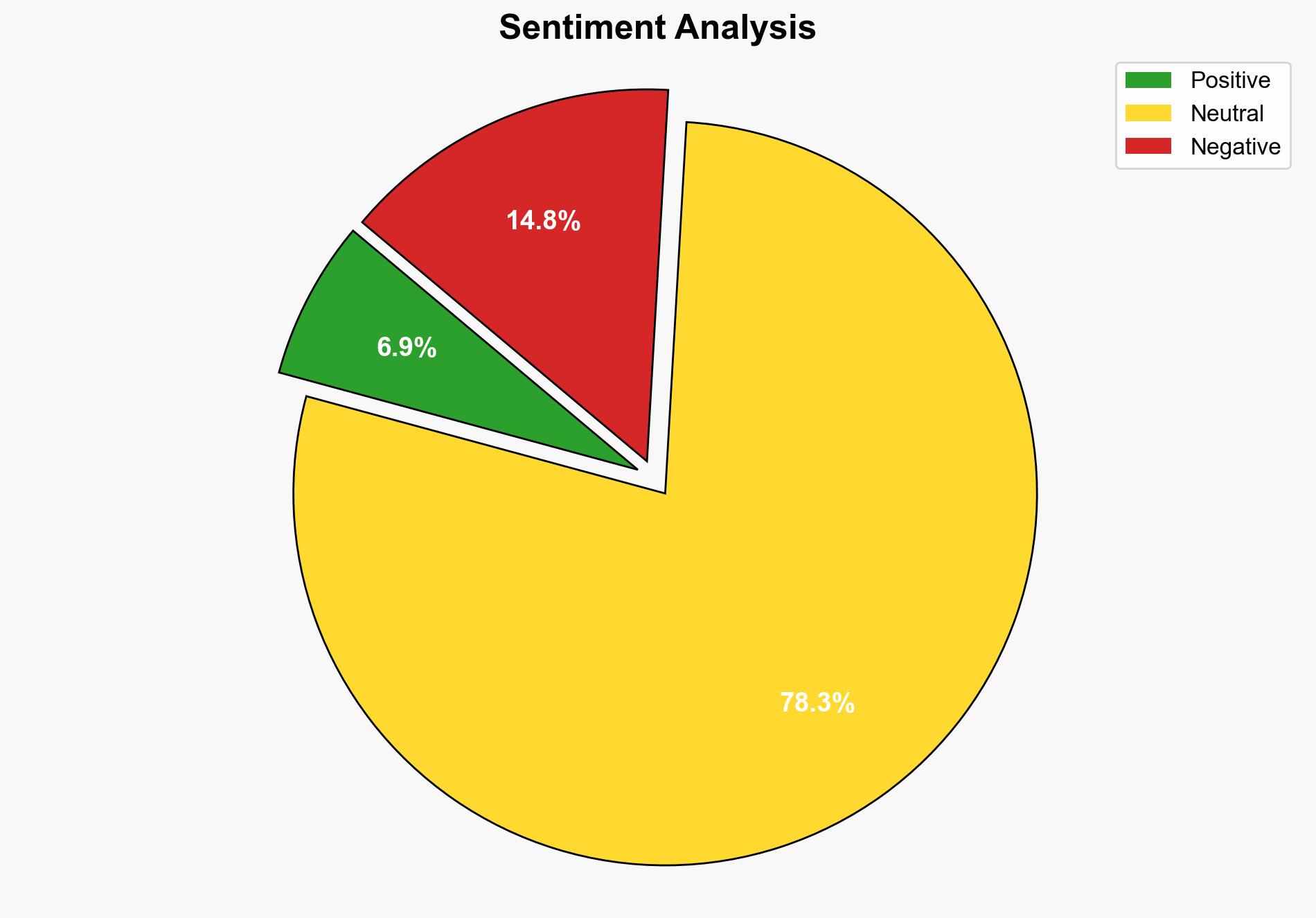
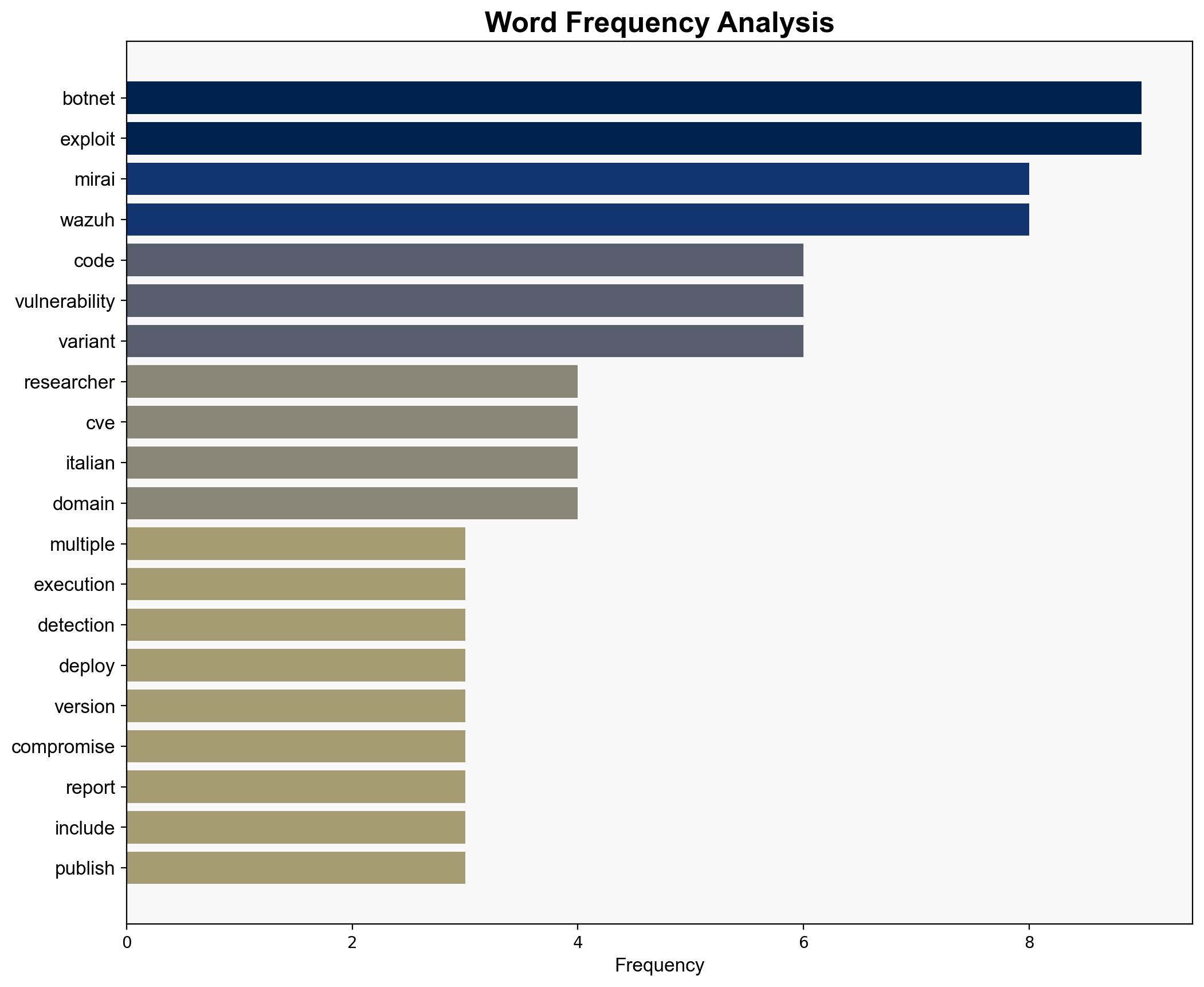
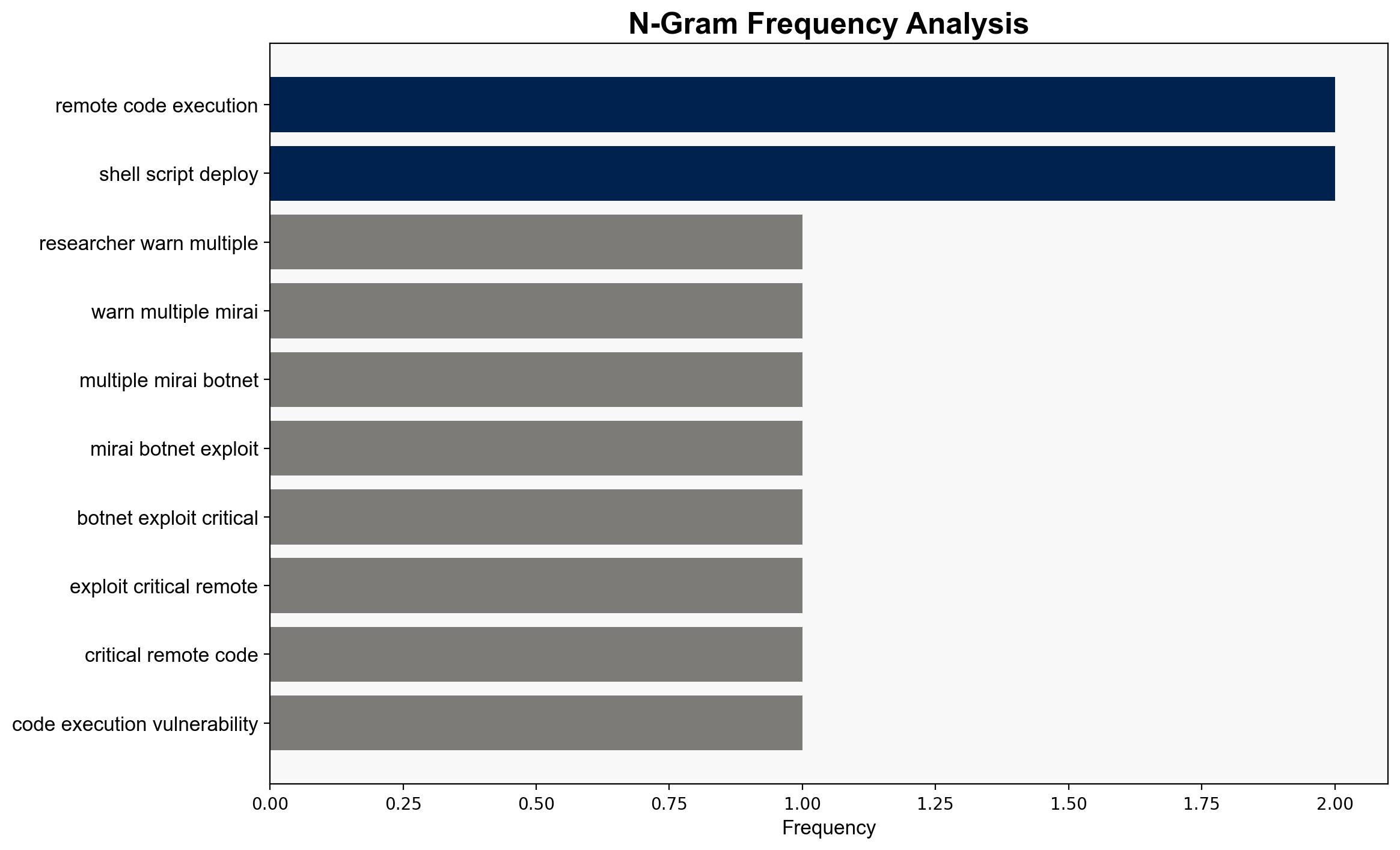
The Mirai botnet has been observed exploiting a critical remote code execution (RCE) vulnerability in Wazuh servers, identified as CVE, with a high CVSS score. This vulnerability allows attackers to execute arbitrary code, posing significant risks to organizations using Wazuh for security monitoring. Immediate patching and enhanced monitoring are recommended to mitigate this threat.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The exploitation of the Wazuh RCE vulnerability by Mirai botnets demonstrates a sophisticated adversarial approach, leveraging unsafe deserialization to inject malicious code. This highlights the need for robust deserialization practices and continuous threat modeling to anticipate and counter such tactics.
Indicators Development
Indicators of Compromise (IOCs) include domain names like nuklearcnc.duckdns.org and galaxia.cc, and TCP port communications. Monitoring these IOCs can aid in early detection of botnet activity.
Bayesian Scenario Modeling
Probabilistic modeling suggests a high likelihood of continued exploitation of this vulnerability, given the ease of repurposing existing Mirai code. This underscores the importance of proactive defense measures.
3. Implications and Strategic Risks
The exploitation of Wazuh servers by Mirai botnets poses systemic risks to cybersecurity infrastructure, potentially disrupting critical services and leading to data breaches. The rapid propagation capability of these botnets could lead to widespread impact, affecting multiple sectors and geographies, particularly those with high IoT device deployment.
4. Recommendations and Outlook
- Immediate patching of Wazuh servers to the latest version to close the RCE vulnerability.
- Enhanced network monitoring for IOCs and unusual traffic patterns.
- Scenario-based projections suggest that without intervention, the botnet could expand its reach, increasing the risk of large-scale disruptions.
5. Key Individuals and Entities
The report does not identify specific individuals by name. However, entities involved include Mirai botnet operators and organizations using Wazuh for security monitoring.
6. Thematic Tags
national security threats, cybersecurity, botnet exploitation, IoT vulnerabilities