More than 25,000 Fortinet devices vulnerable to remote attacks due to FortiCloud SSO authentication flaw
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Over 25000 FortiCloud SSO devices exposed to remote attacks
1. BLUF (Bottom Line Up Front)
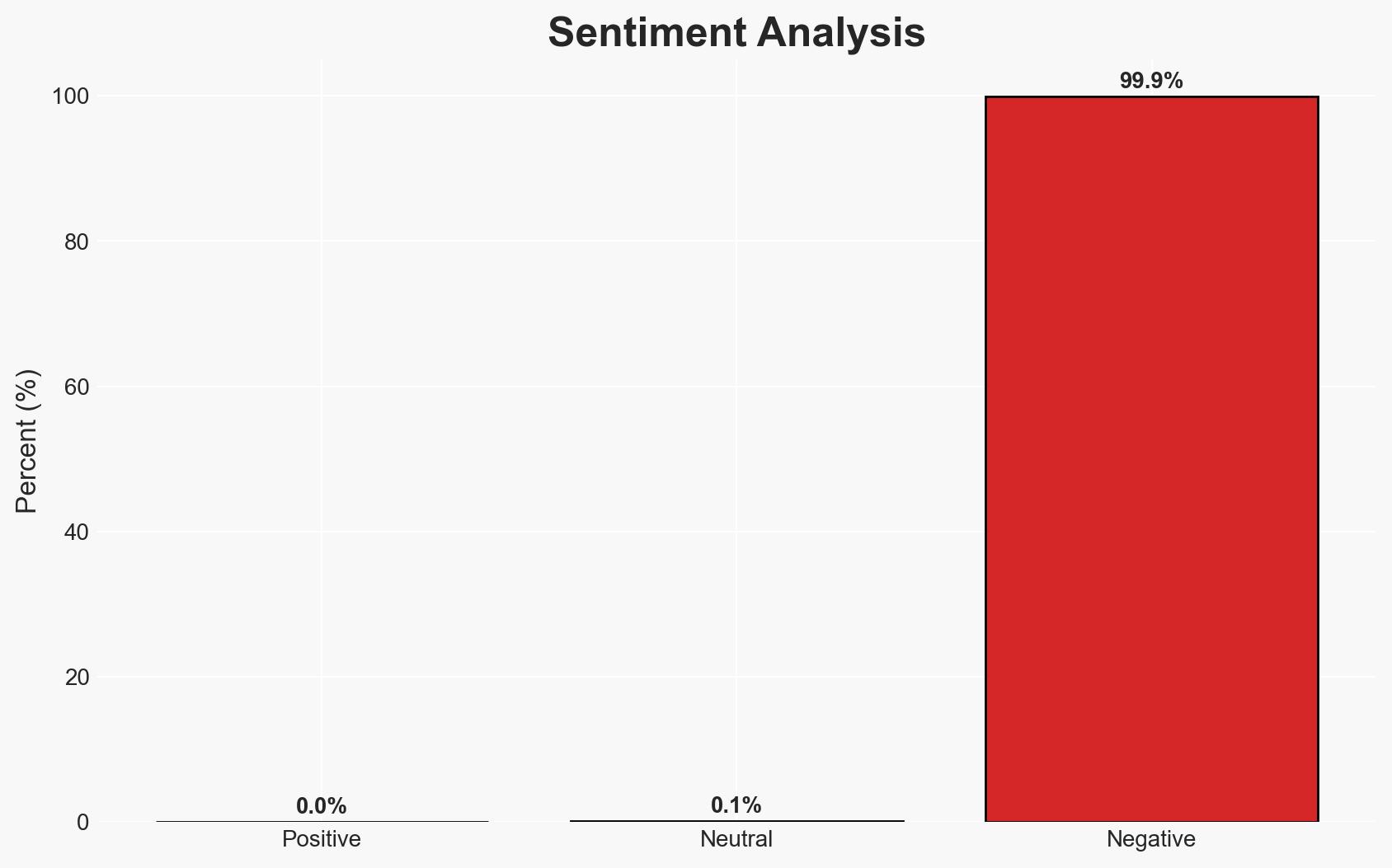
Over 25,000 Fortinet devices with FortiCloud SSO are exposed to a critical authentication bypass vulnerability, posing significant cybersecurity risks. The vulnerability is actively exploited, potentially compromising sensitive data and network configurations. This situation primarily affects organizations using Fortinet products, with a notable concentration in the United States and India. Overall confidence in this assessment is moderate, given the lack of precise data on the number of devices secured against the vulnerability.
2. Competing Hypotheses
- Hypothesis A: The majority of exposed Fortinet devices remain unpatched, increasing the risk of exploitation. This is supported by the high number of devices identified with FortiCloud SSO enabled and historical trends of exploitation. However, the exact number of devices patched remains unknown, introducing uncertainty.
- Hypothesis B: A significant portion of the exposed devices may have already been patched or secured, reducing the overall risk. This hypothesis is less supported due to the lack of evidence indicating widespread patching efforts and the urgency of CISA’s directive to U.S. agencies.
- Assessment: Hypothesis A is currently better supported due to the high number of exposed devices and the active exploitation of the vulnerability. Indicators such as a decrease in exploitation reports or confirmation of widespread patching could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Fortinet users are aware of the vulnerability; CISA’s directive will lead to timely patching; threat actors will continue to exploit unpatched devices.
- Information Gaps: Precise data on the number of devices patched; specific threat actor identities and motivations; detailed impact assessments from affected organizations.
- Bias & Deception Risks: Potential over-reliance on reports from cybersecurity firms with vested interests; threat actors may use misinformation to obscure their activities.
4. Implications and Strategic Risks
This development could lead to increased cyber-espionage and data breaches, affecting national security and economic stability. The ongoing exploitation may prompt regulatory and policy changes in cybersecurity practices.
- Political / Geopolitical: Potential diplomatic tensions if state-sponsored actors are involved; increased pressure on governments to enhance cybersecurity frameworks.
- Security / Counter-Terrorism: Elevated risk of cyber-attacks on critical infrastructure and government networks; possible use of compromised data in broader threat campaigns.
- Cyber / Information Space: Heightened alert in the cybersecurity community; potential for increased investment in cyber defenses and threat intelligence sharing.
- Economic / Social: Possible financial losses for affected organizations; erosion of trust in digital security solutions, impacting market dynamics.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch vulnerable systems; enhance monitoring for signs of exploitation; engage in information sharing with cybersecurity partners.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular vulnerability assessments; strengthen partnerships with cybersecurity firms and government agencies.
- Scenario Outlook:
- Best: Rapid patching and coordinated response mitigate risks, with minimal exploitation.
- Worst: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Continued exploitation of unpatched systems with gradual improvements in security posture.
6. Key Individuals and Entities
- Shadowserver (Internet security watchdog)
- Fortinet (Cybersecurity company)
- Arctic Wolf (Cybersecurity company)
- CISA (U.S. Cybersecurity and Infrastructure Security Agency)
- Macnica (Threat researcher Yutaka Sejiyama)
- Volt Typhoon (Chinese hacking group)
7. Thematic Tags
cybersecurity, vulnerability management, cyber-espionage, Fortinet, SSO exploitation, network security, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us