Mosyle uncovers first AI-enhanced Mac malware threat disguised as popular app Grok
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Mosyle identifies one of the first known AI-assisted Mac malware threats
1. BLUF (Bottom Line Up Front)
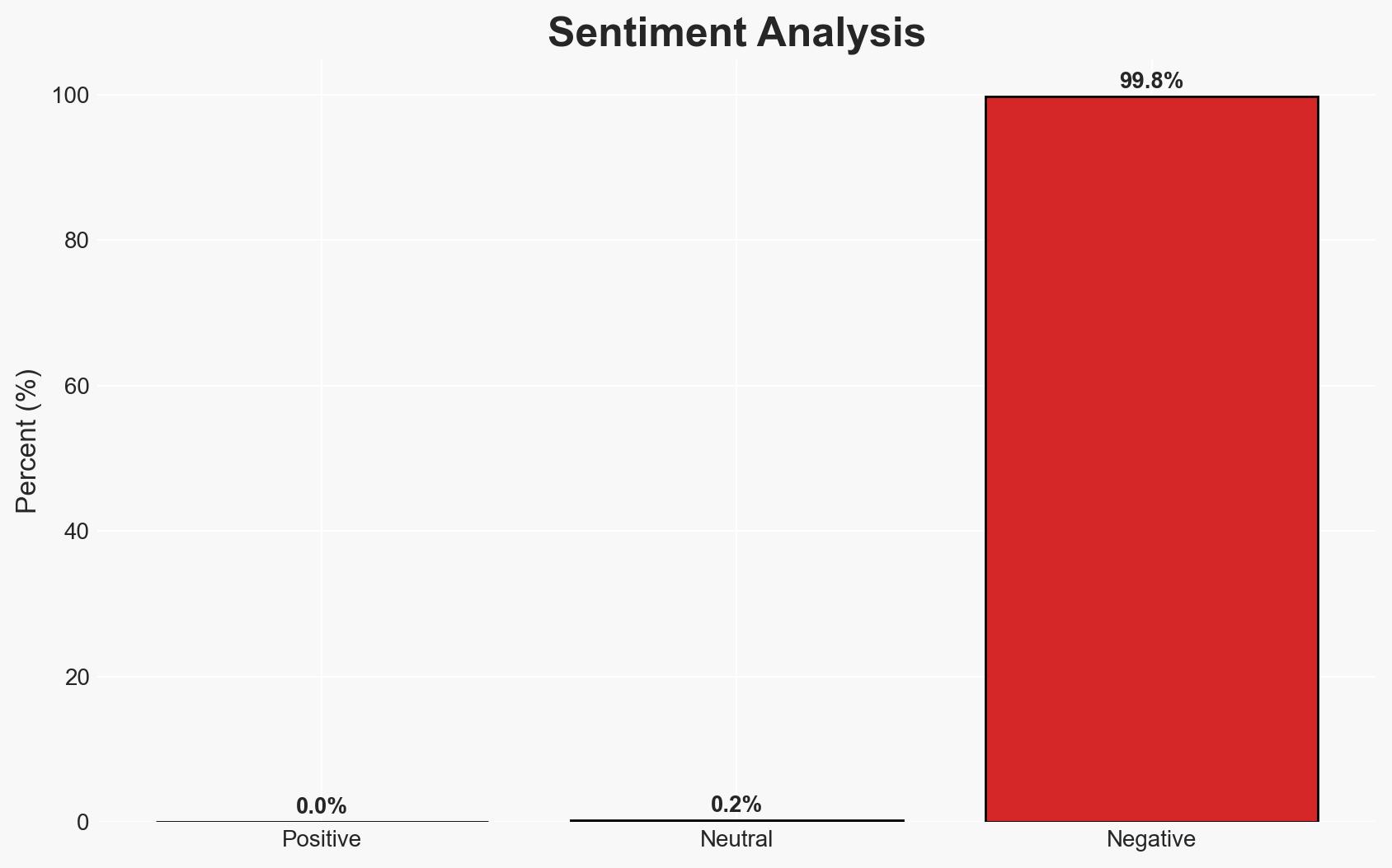
The discovery of AI-assisted Mac malware, SimpleStealth, marks a significant evolution in cyber threats, leveraging generative AI to enhance deception and persistence. This development primarily affects macOS users and highlights vulnerabilities in current antivirus capabilities. The most likely hypothesis is that AI will increasingly be used to create sophisticated malware, posing a growing threat to cybersecurity. Overall confidence in this assessment is moderate due to existing information gaps.
2. Competing Hypotheses
- Hypothesis A: The SimpleStealth malware is an isolated incident, primarily targeting macOS users through a specific fake app. Supporting evidence includes the use of a look-alike domain and the focus on a single type of payload (crypto mining). However, the lack of detection by major antivirus engines suggests broader implications.
- Hypothesis B: SimpleStealth represents the beginning of a broader trend of AI-assisted malware campaigns across multiple platforms. Evidence includes the use of generative AI in its code and previous warnings about AI in malware development. Contradicting evidence is the current focus on macOS and crypto mining, which may not indicate immediate cross-platform intentions.
- Assessment: Hypothesis B is currently better supported due to the strategic use of AI in malware development, which aligns with broader trends in cyber threat evolution. Key indicators that could shift this judgment include evidence of similar campaigns on other platforms or the discovery of additional AI-assisted malware.
3. Key Assumptions and Red Flags
- Assumptions: AI will continue to lower barriers for malware creation; macOS will remain a target due to perceived security; threat actors will exploit AI for stealth and persistence.
- Information Gaps: Details on the scale of the SimpleStealth campaign, the identity and motives of the threat actors, and the full extent of AI’s role in the malware’s development.
- Bias & Deception Risks: Potential bias in focusing on AI’s role without considering traditional methods; risk of deception from threat actors using AI as a smokescreen for other activities.
4. Implications and Strategic Risks
This development could lead to increased sophistication in malware, challenging existing cybersecurity defenses and requiring new detection strategies. The use of AI in malware could accelerate the pace of threat evolution.
- Political / Geopolitical: Heightened tensions in cyber diplomacy as nations respond to AI-enhanced cyber threats.
- Security / Counter-Terrorism: Increased operational challenges for cybersecurity and counter-terrorism units in identifying and mitigating AI-assisted threats.
- Cyber / Information Space: Potential for AI-assisted malware to disrupt critical infrastructure and information systems, increasing the complexity of cyber defense.
- Economic / Social: Potential economic impacts from increased cybercrime and the need for businesses to invest in advanced cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of macOS systems, update antivirus definitions, and educate users on the risks of downloading from unofficial sources.
- Medium-Term Posture (1–12 months): Develop partnerships with AI research entities to understand and counter AI-assisted threats, and invest in AI-driven cybersecurity tools.
- Scenario Outlook:
- Best: AI-assisted malware remains isolated to a few incidents, with effective countermeasures developed.
- Worst: Widespread adoption of AI in malware leads to a significant increase in successful cyberattacks.
- Most-Likely: Gradual increase in AI-assisted threats, prompting ongoing adaptation of cybersecurity strategies.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, AI-assisted malware, macOS threats, generative AI, crypto mining, cyber defense, malware evolution
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us