NATO Official Highlights China’s Threat to European Energy Security Amid Concerns Over Dependence on Renewabl…
Published on: 2025-12-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China poses major risk to Europe’s energy grids, top NATO official warns
1. BLUF (Bottom Line Up Front)
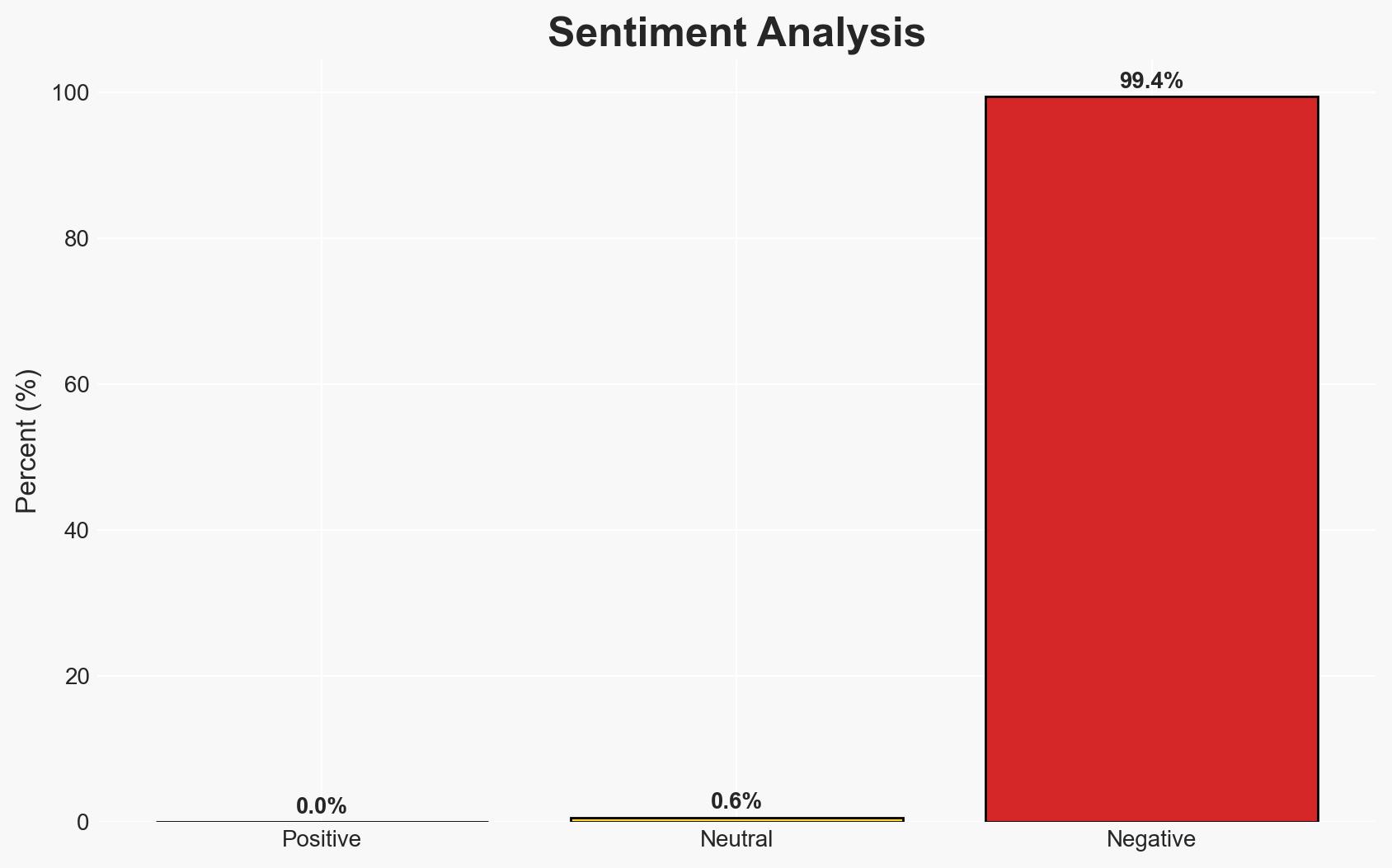
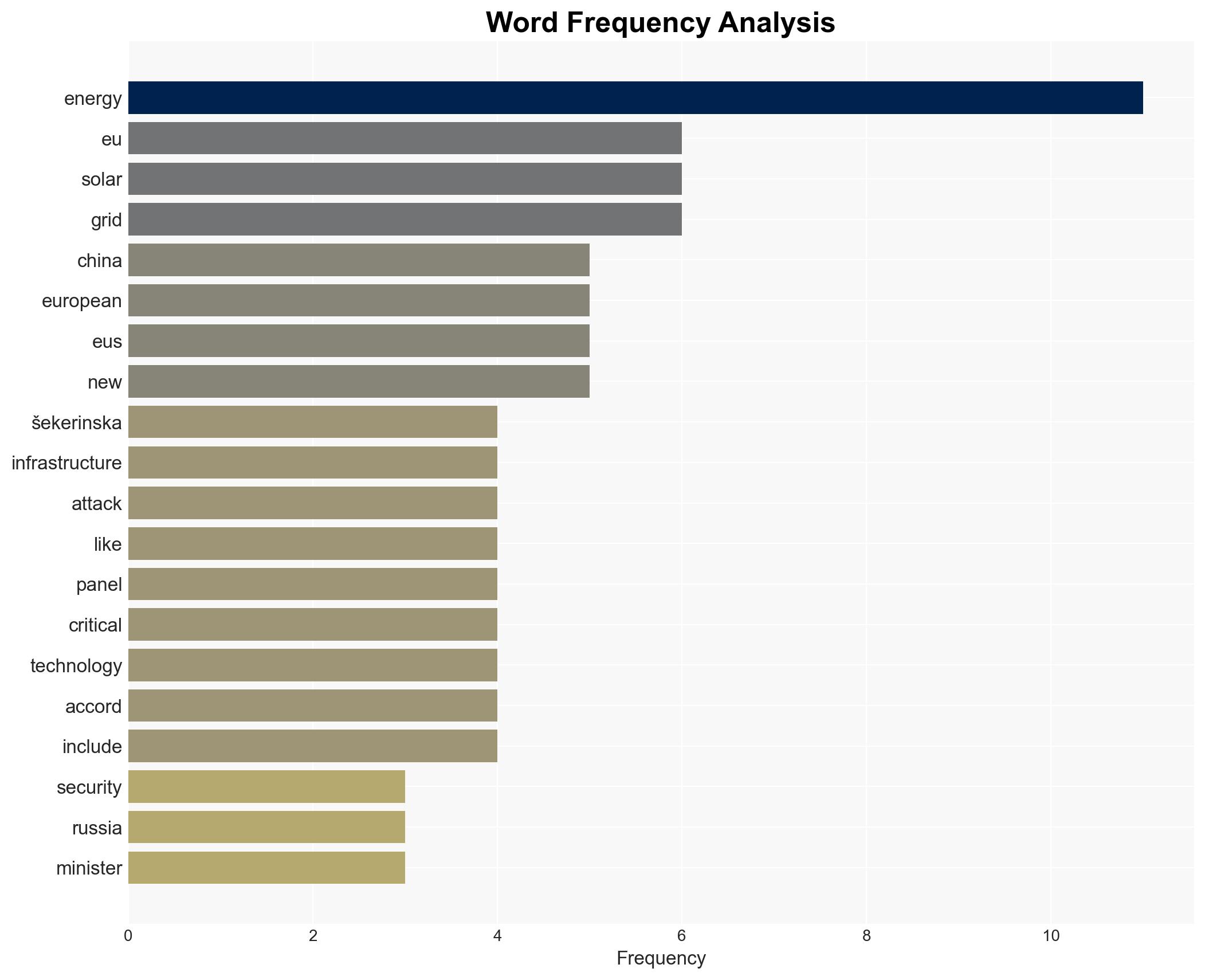
China’s dominance in supplying renewable energy technologies to Europe poses a significant risk to the EU’s energy security, comparable to threats from Russia. This dependency creates vulnerabilities in both physical and digital infrastructure. The most likely hypothesis is that China’s influence could be leveraged for strategic advantage, affecting European resilience. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
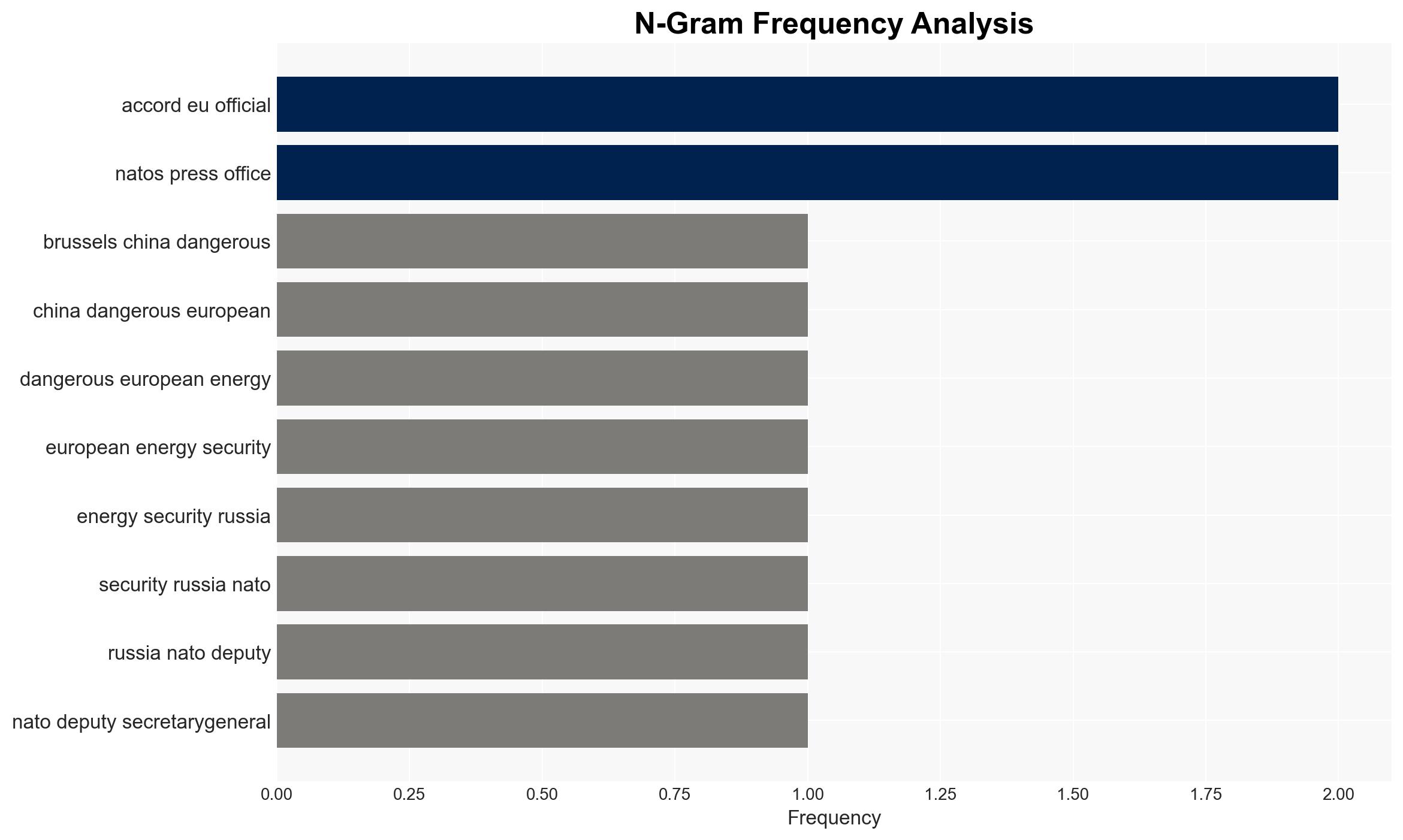
- Hypothesis A: China is leveraging its dominance in renewable energy technologies to exert strategic influence over Europe, potentially compromising energy security. This is supported by the EU’s heavy reliance on Chinese imports for solar panels and wind turbines. However, the extent of China’s intent to exploit this dependency remains uncertain.
- Hypothesis B: China’s involvement in Europe’s renewable energy sector is primarily economic, driven by market opportunities rather than strategic intent. While this hypothesis considers China’s economic motivations, it does not fully address the security implications of such dependencies.
- Assessment: Hypothesis A is currently better supported due to the strategic vulnerabilities identified by NATO and EU officials. Indicators such as increased scrutiny of Chinese tech companies and efforts to de-risk supply chains could shift this judgment if they reveal benign intentions.
3. Key Assumptions and Red Flags
- Assumptions: European energy infrastructure is vulnerable to external manipulation; China’s export dominance translates to strategic leverage; EU efforts to diversify supply chains will be effective.
- Information Gaps: Specific Chinese government policies regarding the use of energy technology exports for strategic purposes; detailed impact assessments of potential supply chain disruptions.
- Bias & Deception Risks: Potential bias in NATO and EU assessments due to geopolitical tensions; risk of underestimating China’s economic motivations over strategic ones.
4. Implications and Strategic Risks
The development could lead to increased geopolitical tensions as Europe seeks to reduce dependency on Chinese technology. This may catalyze policy shifts towards greater energy independence and diversification.
- Political / Geopolitical: Potential for strained EU-China relations and increased alignment with the US on energy security policies.
- Security / Counter-Terrorism: Heightened risk of cyber-attacks on energy infrastructure as geopolitical tensions rise.
- Cyber / Information Space: Increased focus on cybersecurity measures to protect critical infrastructure from state-sponsored threats.
- Economic / Social: Potential economic disruptions as Europe transitions away from Chinese suppliers, impacting renewable energy projects and costs.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Chinese technology imports; conduct vulnerability assessments of critical energy infrastructure.
- Medium-Term Posture (1–12 months): Develop partnerships with alternative suppliers; invest in domestic renewable energy technology production capabilities.
- Scenario Outlook: Best: Successful diversification reduces dependencies. Worst: Escalating tensions lead to supply chain disruptions. Most-Likely: Gradual reduction in dependency with increased security measures.
6. Key Individuals and Entities
- Radmila Šekerinska, NATO Deputy Secretary-General
- European Commission
- Huawei
- Amazon’s cloud division
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, energy security, China-EU relations, renewable energy, supply chain vulnerabilities, NATO, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us