New Android Malware FvncBot and SeedSnatcher Enhance Data Theft Capabilities, Target Banking Users
Published on: 2025-12-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
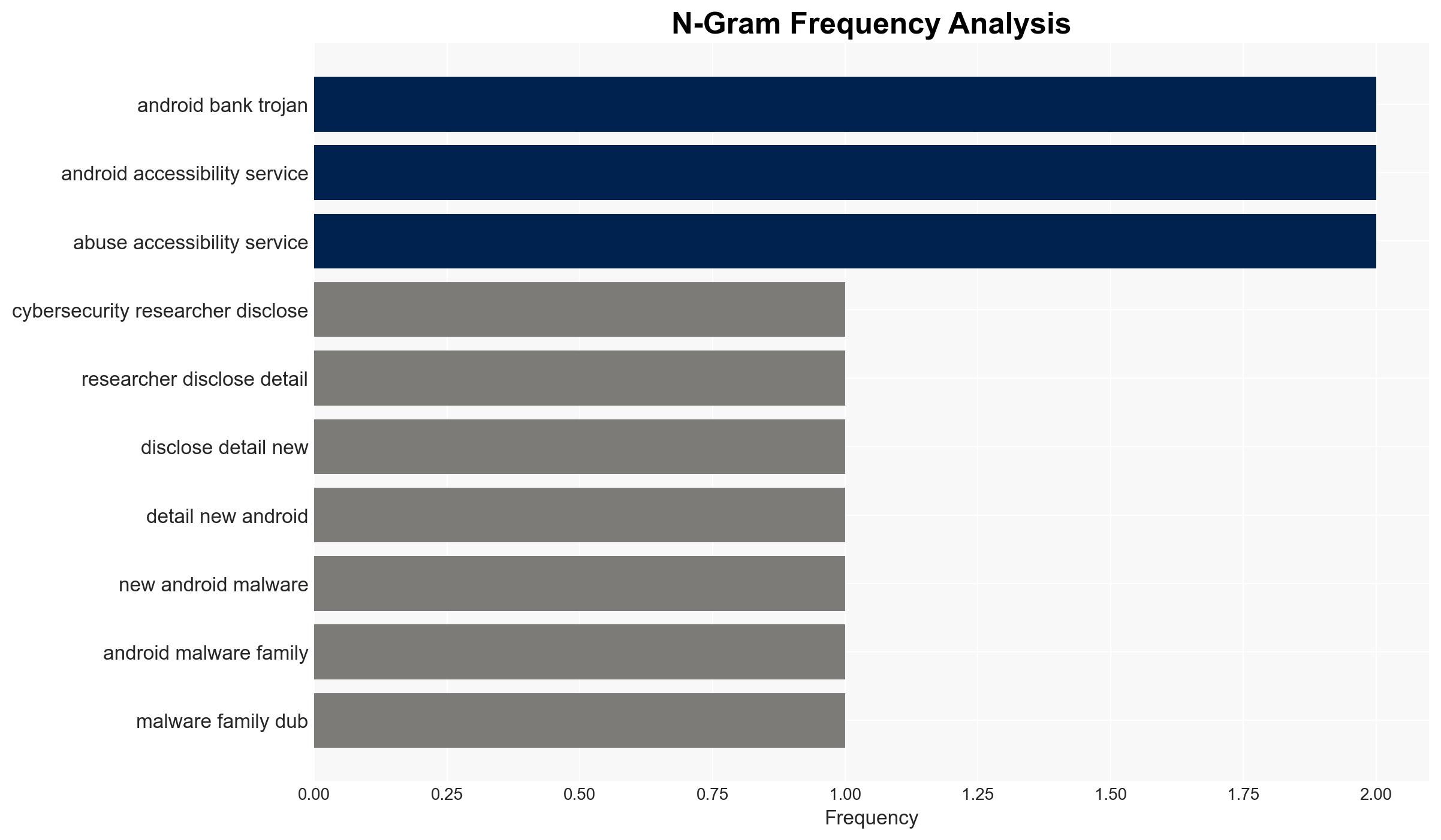
Intelligence Report: Android Malware FvncBot SeedSnatcher and ClayRat Gain Stronger Data Theft Features
1. BLUF (Bottom Line Up Front)
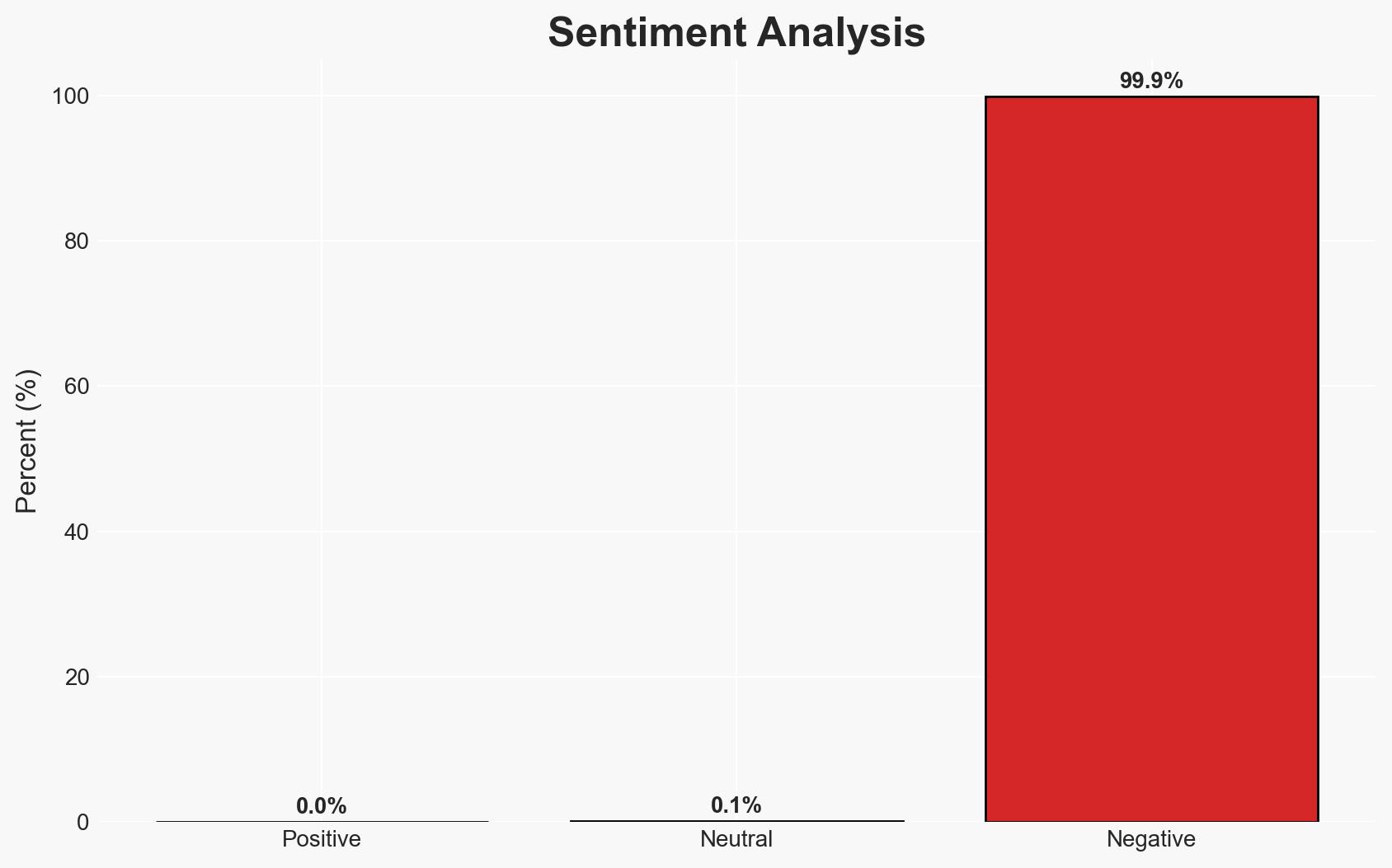
The emergence of new Android malware families, FvncBot and SeedSnatcher, alongside an upgraded version of ClayRat, signifies an evolving threat landscape targeting mobile banking users, particularly in Poland. The malware’s sophisticated features, such as keylogging and screen streaming, pose significant risks to user data security. This assessment is made with moderate confidence due to the early stage of development and limited geographical targeting.
2. Competing Hypotheses
- Hypothesis A: FvncBot and SeedSnatcher are primarily targeting Polish banking users as part of a localized cybercrime operation. This is supported by the malware’s build identifier call_pl and its specific targeting of mBank users. However, the early stage of development suggests potential for broader targeting.
- Hypothesis B: The malware represents a test phase for a larger-scale operation that could expand beyond Poland. The use of advanced features and crypting services indicates potential for wider application. Contradicting this is the current focus on a specific region and banking institution.
- Assessment: Hypothesis A is currently better supported due to the specific targeting indicators and early development stage. Key indicators that could shift this judgment include expansion of targeting to other regions or institutions and further development of the malware’s capabilities.
3. Key Assumptions and Red Flags
- Assumptions: The malware is primarily targeting Polish users; the threat actors are motivated by financial gain; the malware is in an early stage of development.
- Information Gaps: Lack of detailed information on the operators behind the malware; potential future targets beyond Poland; the full scope of the malware’s capabilities.
- Bias & Deception Risks: Potential bias in focusing on Poland due to current evidence; risk of underestimating the malware’s potential reach and sophistication.
4. Implications and Strategic Risks
The development of these malware families could lead to increased financial fraud incidents and erosion of trust in mobile banking security. Over time, these threats may evolve to target broader geographies and industries.
- Political / Geopolitical: Limited immediate implications, but potential for increased tensions if linked to state-sponsored actors.
- Security / Counter-Terrorism: Heightened alert for financial institutions and mobile users; potential for adaptation by other threat actors.
- Cyber / Information Space: Increased sophistication in malware techniques; potential for broader cyber espionage activities.
- Economic / Social: Potential economic impact on affected users and institutions; erosion of consumer confidence in digital banking.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Android malware activity; inform Polish financial institutions of the threat; increase public awareness on mobile security practices.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced malware detection and response capabilities.
- Scenario Outlook:
- Best: Containment of the threat within Poland with no further development.
- Worst: Expansion of the malware’s capabilities and geographical reach, leading to widespread financial fraud.
- Most-Likely: Gradual evolution of the malware with limited expansion beyond initial targets.
6. Key Individuals and Entities
- Intel 471, CYFIRMA, Zimperium (cybersecurity firms involved in the research)
- Golden Crypt (crypting service provider)
- mBank (targeted financial institution)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, mobile banking, malware, financial fraud, Poland, Android, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us