New Google AppSheet Phishing Scam Deliver Fake Trademark Notices – HackRead
Published on: 2025-09-11
Intelligence Report: New Google AppSheet Phishing Scam Deliver Fake Trademark Notices – HackRead
1. BLUF (Bottom Line Up Front)
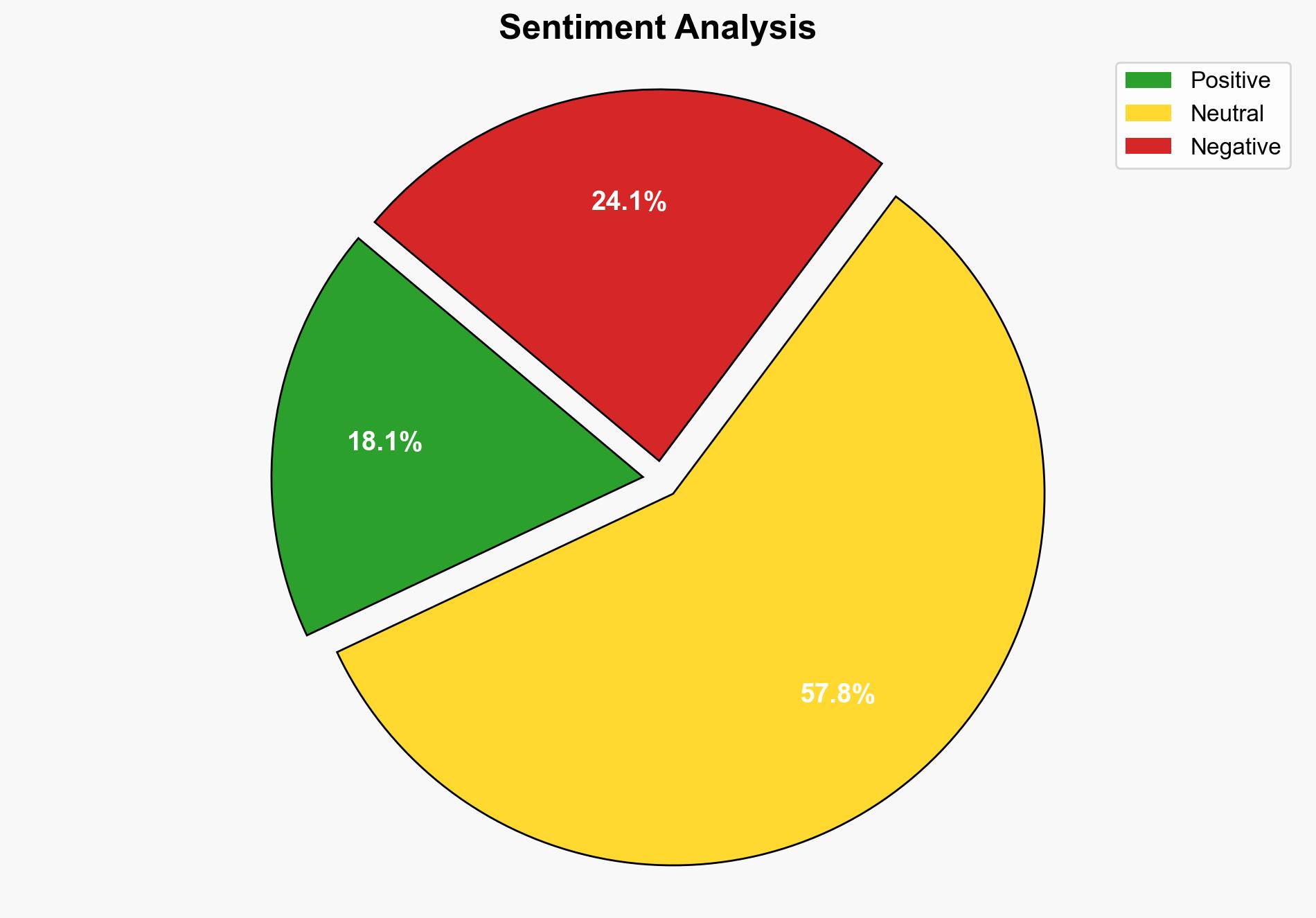
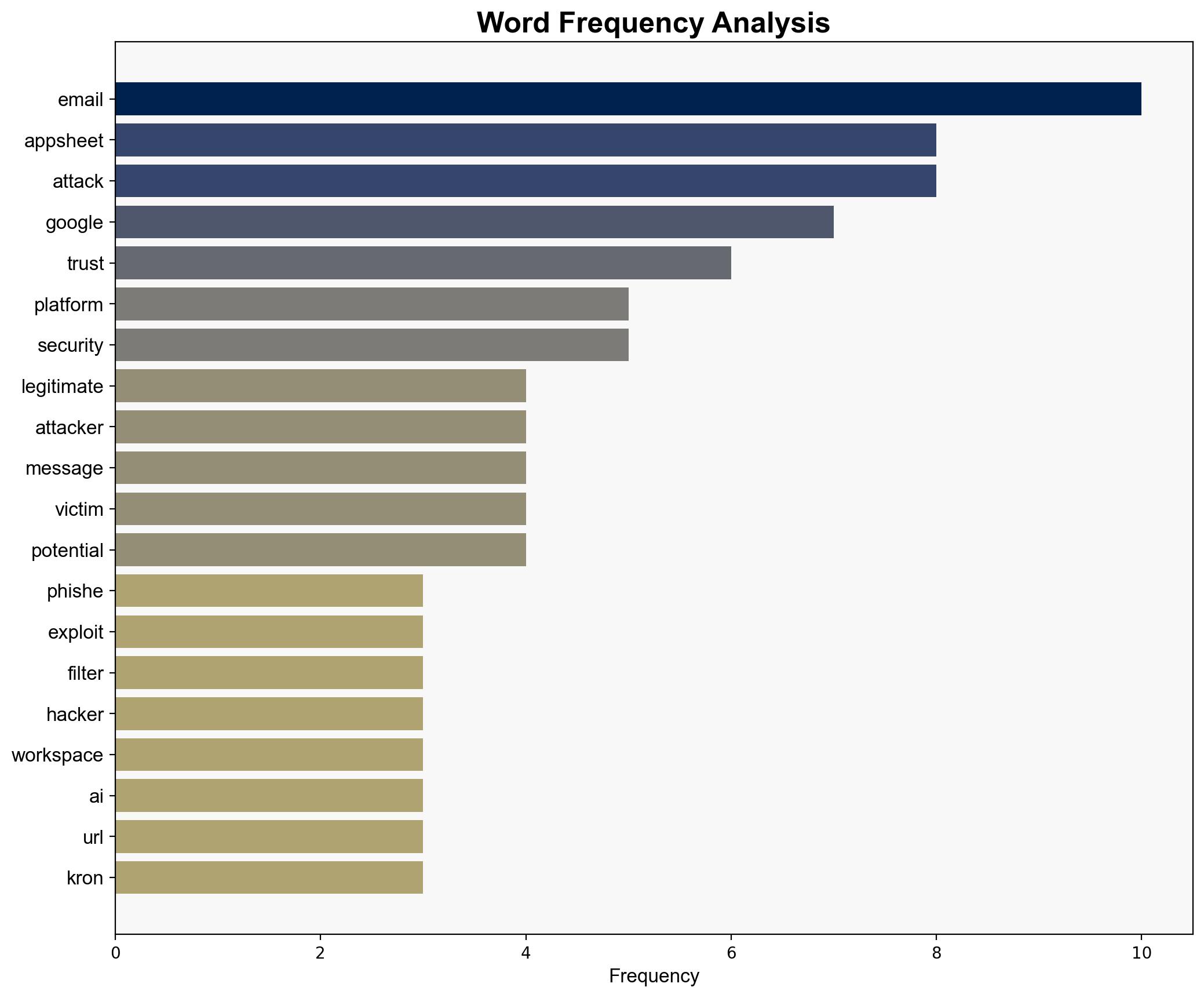
The phishing scam exploiting Google AppSheet represents a sophisticated method of bypassing traditional email security measures by leveraging trusted platforms. The most supported hypothesis is that attackers are increasingly using legitimate platforms to evade detection, highlighting a critical vulnerability in current cybersecurity frameworks. Confidence Level: High. Recommended action includes enhancing user awareness and developing advanced detection systems that analyze content contextually rather than relying solely on authentication protocols.
2. Competing Hypotheses
Hypothesis 1: Attackers are exploiting trusted platforms like Google AppSheet to bypass email filters, leveraging the inherent trust users place in these platforms to execute phishing scams effectively.
Hypothesis 2: The phishing campaign is part of a broader trend where attackers are targeting widely used platforms to exploit their user base, indicating a shift in phishing strategies towards more sophisticated social engineering tactics.
Using Analysis of Competing Hypotheses (ACH 2.0), Hypothesis 1 is better supported by the evidence. The use of legitimate platforms to evade detection aligns with observed patterns in the phishing campaign, as attackers exploit the trust and authenticity associated with Google AppSheet.
3. Key Assumptions and Red Flags
Assumptions include the belief that traditional email security measures are sufficient to detect phishing attempts. A red flag is the reliance on brand trust, which attackers exploit to bypass technical filters. The absence of data on the effectiveness of current user education programs is a blind spot.
4. Implications and Strategic Risks
The exploitation of trusted platforms poses a significant risk to cybersecurity, potentially leading to increased phishing success rates and broader adoption of similar tactics by other malicious actors. This could result in economic losses and damage to brand reputations. The psychological impact on users, who may become more distrustful of legitimate communications, is also a concern.
5. Recommendations and Outlook
- Enhance user education programs to include identification of sophisticated phishing tactics and suspicious URLs.
- Develop and implement advanced detection systems that analyze the context and content of messages, not just authentication protocols.
- Scenario Projections:
- Best Case: Improved detection and user education significantly reduce the effectiveness of such phishing scams.
- Worst Case: Attackers refine tactics further, leading to widespread breaches and loss of sensitive information.
- Most Likely: Continued evolution of phishing tactics with incremental improvements in detection and user awareness.
6. Key Individuals and Entities
Erich Kron, who provided expert commentary on the phishing tactics and the importance of user awareness.
7. Thematic Tags
national security threats, cybersecurity, social engineering, phishing, trusted platforms