New Guidance from CISA and Global Partners on Safeguarding AI in Critical Infrastructure Systems
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA and International Partners Issue Guidance for Secure AI in Infrastructure
1. BLUF (Bottom Line Up Front)
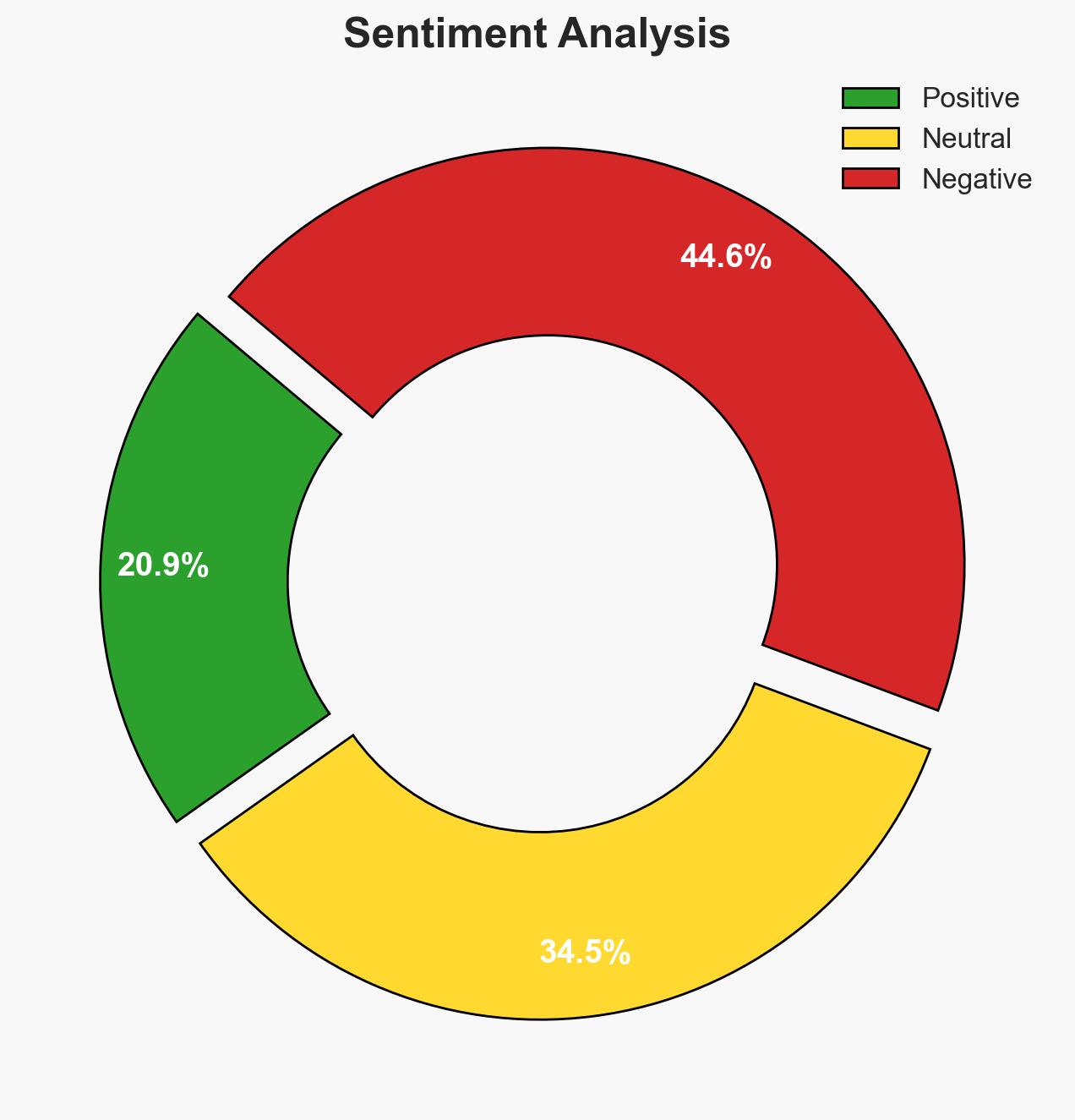
The new guidance issued by CISA and international partners aims to secure AI integration into critical infrastructure, emphasizing both opportunities and risks. The most likely hypothesis is that this guidance will enhance security practices among operators, but challenges remain in implementation and compliance. This affects critical infrastructure operators globally. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The guidance will lead to improved security and operational efficiency in AI-integrated OT systems. Supporting evidence includes the comprehensive nature of the guidance and its international collaboration. However, uncertainties include the varying levels of readiness and resources among operators to implement these recommendations.
- Hypothesis B: The guidance will have limited impact due to challenges in implementation, such as integration with legacy systems and regulatory compliance. Contradicting evidence includes the proactive measures outlined in the guidance, although the complexity of existing systems presents significant hurdles.
- Assessment: Hypothesis A is currently better supported due to the structured approach and international backing of the guidance. Indicators that could shift this judgment include reports of successful implementation or significant breaches despite adherence to the guidance.
3. Key Assumptions and Red Flags
- Assumptions: Operators have the capability to understand and implement the guidance; AI integration will continue to be a priority for infrastructure operators; international cooperation will persist in cybersecurity efforts.
- Information Gaps: Specific details on how operators plan to implement the guidance and their current levels of compliance with existing cybersecurity frameworks.
- Bias & Deception Risks: Potential bias in the guidance favoring certain technologies or vendors; risk of underreporting challenges by operators to maintain reputational integrity.
4. Implications and Strategic Risks
The guidance could lead to a more secure integration of AI in critical infrastructure, but its success depends on effective implementation and compliance. Over time, this could influence global cybersecurity standards and practices.
- Political / Geopolitical: Strengthened international cybersecurity collaboration could lead to increased geopolitical stability and trust among allied nations.
- Security / Counter-Terrorism: Enhanced security measures could reduce vulnerabilities in critical infrastructure, potentially deterring cyber-terrorism threats.
- Cyber / Information Space: The guidance may set a precedent for future cybersecurity policies, influencing global cyber norms and practices.
- Economic / Social: Improved security could bolster economic stability by protecting critical infrastructure, though initial implementation costs may strain resources.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Operators should conduct a gap analysis against the guidance and begin training personnel on secure AI practices.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity agencies for ongoing support and compliance checks; invest in upgrading legacy systems to accommodate AI integration.
- Scenario Outlook:
- Best: Full compliance leads to enhanced security and operational efficiency.
- Worst: Implementation failures result in increased vulnerabilities and cyber incidents.
- Most-Likely: Gradual improvement in security posture with ongoing challenges in legacy system integration.
6. Key Individuals and Entities
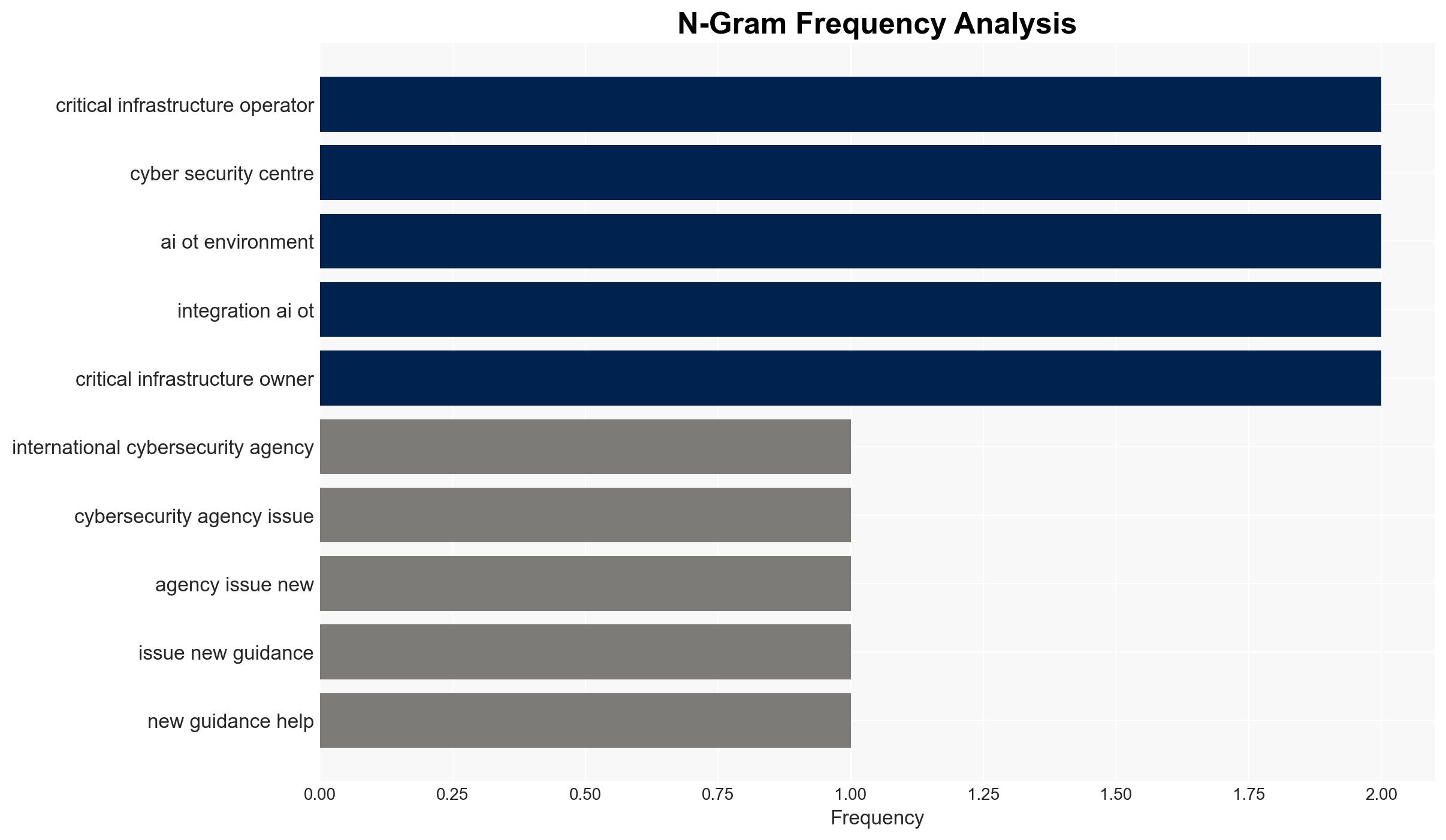
- US Cybersecurity and Infrastructure Security Agency (CISA)
- Australian Signals Directorate’s Australian Cyber Security Centre
- UK’s National Cyber Security Centre (NCSC)
- Critical infrastructure operators (not clearly identifiable from open sources in this snippet)
7. Thematic Tags
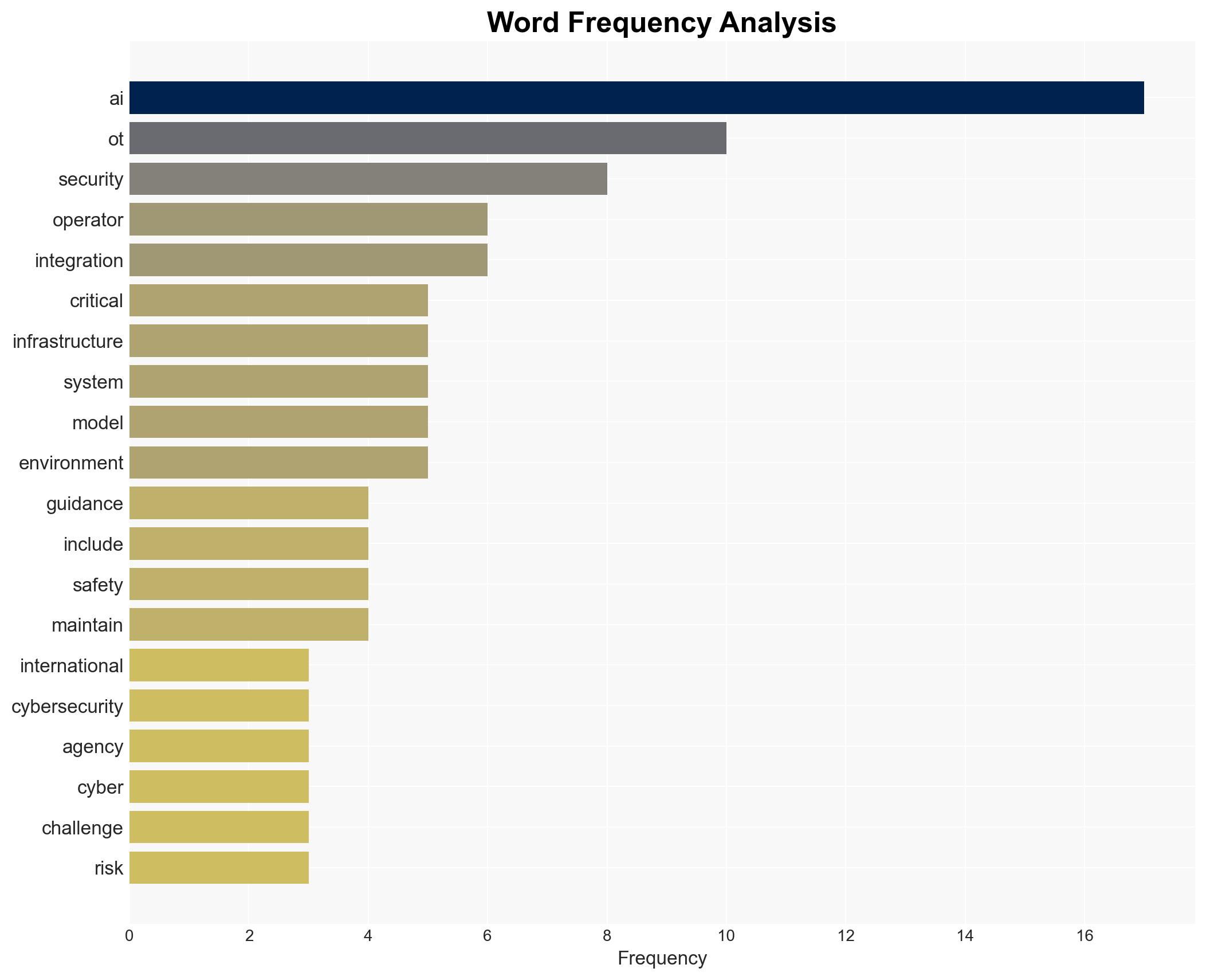
Cybersecurity, critical infrastructure, AI integration, operational technology, international collaboration, regulatory compliance, cyber risk management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us