New initiative aims to strengthen India’s homegrown cyber resilience
Published on: 2025-11-25
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
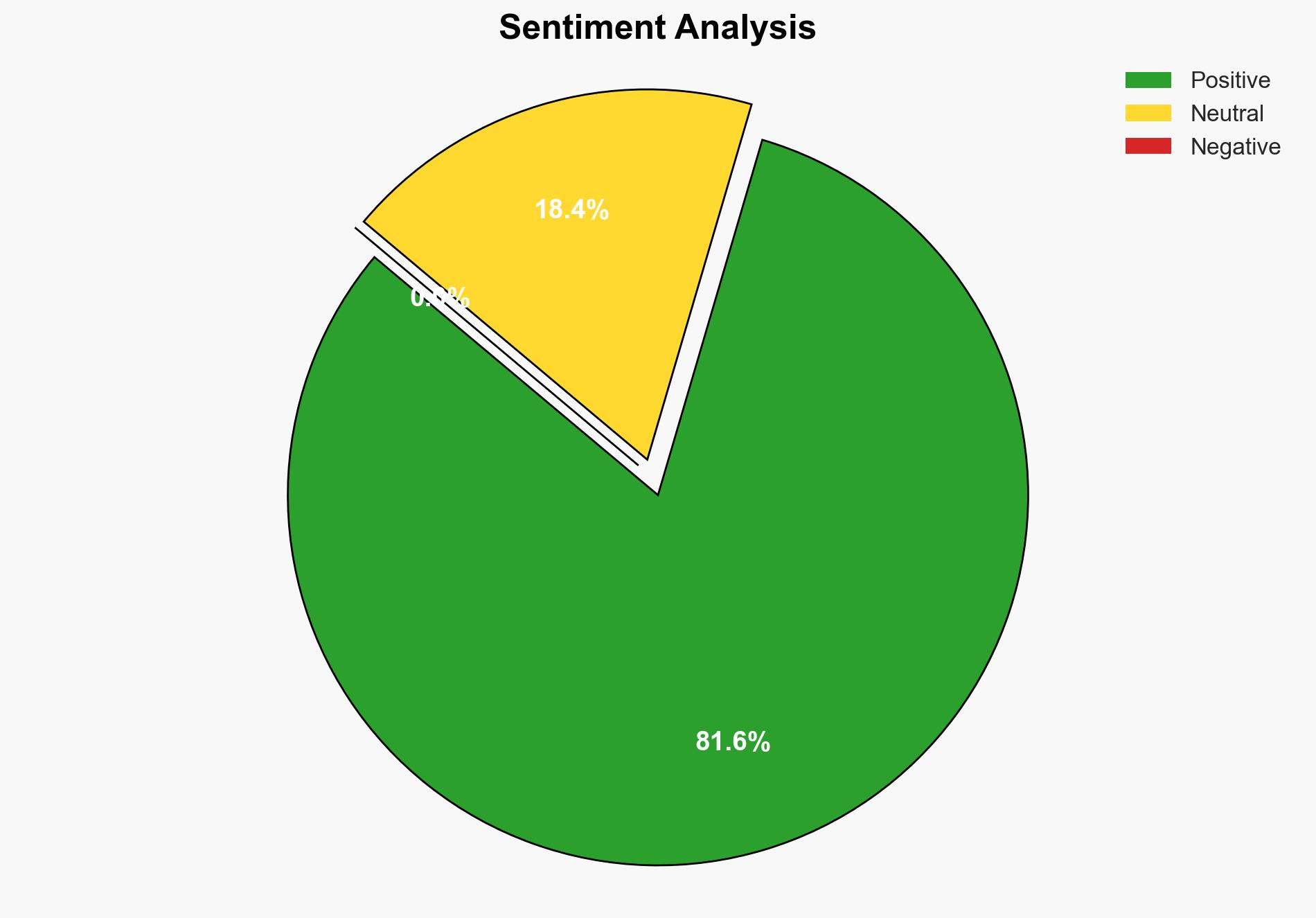
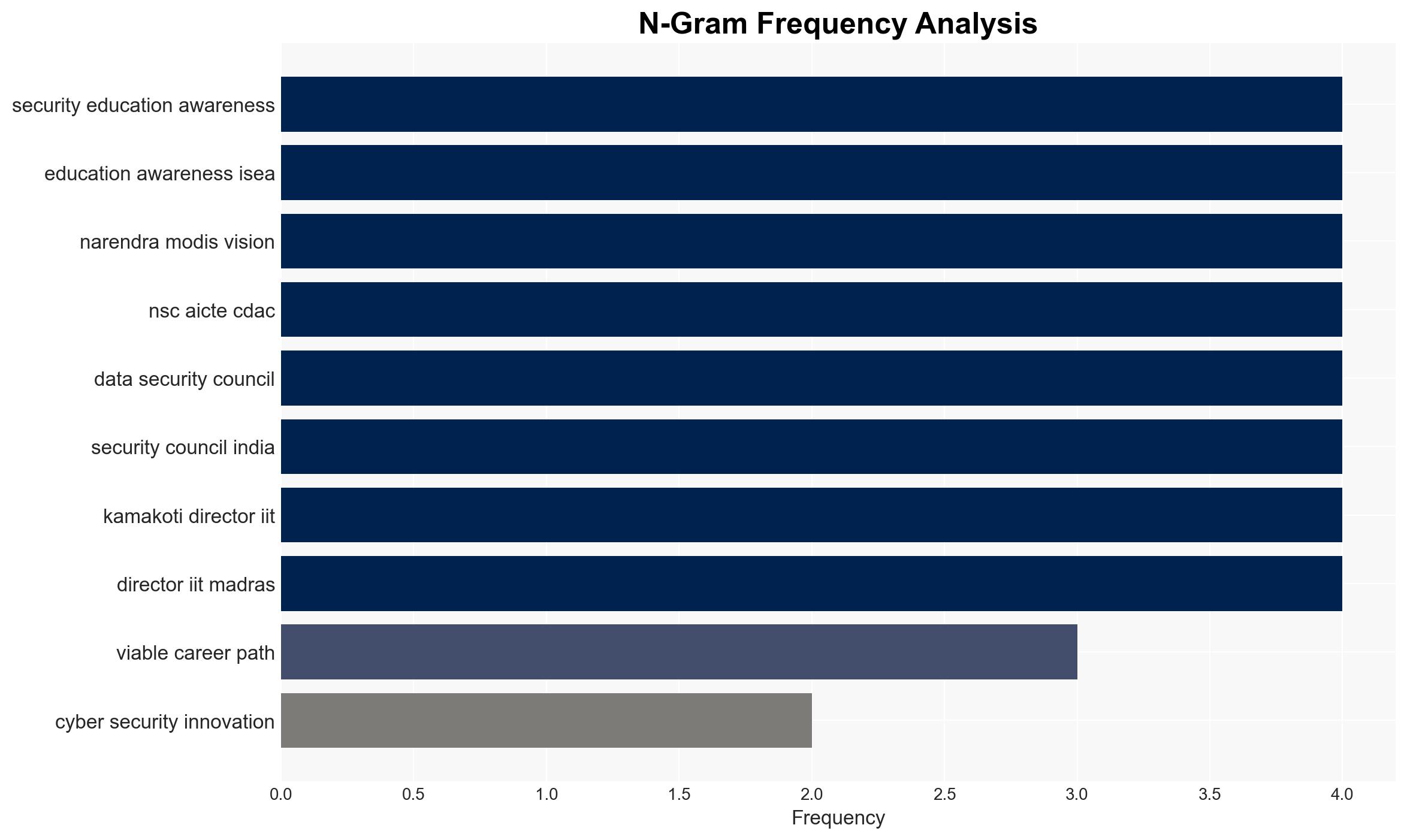
The initiative to strengthen India’s homegrown cyber resilience through the Cyber Security Innovation Challenge (CSIC) is a strategic move to bolster national cybersecurity capabilities. With a medium to high confidence level, the most supported hypothesis is that this initiative will enhance India’s cybersecurity infrastructure by fostering innovation and collaboration among academia, industry, and government. Recommended actions include continued investment in cybersecurity education and public-private partnerships to ensure the initiative’s success.
2. Competing Hypotheses
Hypothesis 1: The CSIC will significantly enhance India’s cybersecurity resilience by developing a skilled workforce and innovative solutions tailored to national needs.
Hypothesis 2: The CSIC will face challenges in implementation due to bureaucratic hurdles and lack of sustained industry engagement, limiting its impact on national cybersecurity resilience.
Hypothesis 1 is more likely due to the structured approach of the initiative, including collaboration with key stakeholders and a focus on practical, real-world solutions. However, the success of this hypothesis depends on effective execution and sustained engagement from all parties involved.
3. Key Assumptions and Red Flags
Assumptions: The initiative assumes that there will be sufficient interest and participation from students and researchers, and that industry partners will actively engage in the development of solutions.
Red Flags: Potential bureaucratic delays, lack of funding, or insufficient industry collaboration could impede progress. Additionally, if the initiative fails to align with rapidly evolving cyber threats, its effectiveness may be compromised.
4. Implications and Strategic Risks
The initiative could lead to a stronger cybersecurity posture for India, reducing vulnerabilities to cyber attacks and enhancing national security. However, failure to effectively implement the program could result in wasted resources and missed opportunities to address critical cybersecurity gaps. Politically, a successful initiative could bolster India’s position as a leader in cybersecurity innovation, while failure could undermine confidence in government-led initiatives.
5. Recommendations and Outlook
- Ensure continuous funding and resource allocation to support the initiative’s goals.
- Facilitate regular communication and collaboration between academia, industry, and government to maintain momentum and address challenges promptly.
- Monitor and adapt the program to align with emerging cyber threats and technological advancements.
- Best-case scenario: The initiative leads to the development of cutting-edge cybersecurity solutions and a robust talent pipeline, significantly enhancing India’s cyber resilience.
- Worst-case scenario: The initiative fails to produce tangible results due to lack of coordination and support, leaving India vulnerable to cyber threats.
- Most-likely scenario: The initiative achieves moderate success, with some innovative solutions and increased awareness, but requires ongoing adjustments to fully realize its potential.
6. Key Individuals and Entities
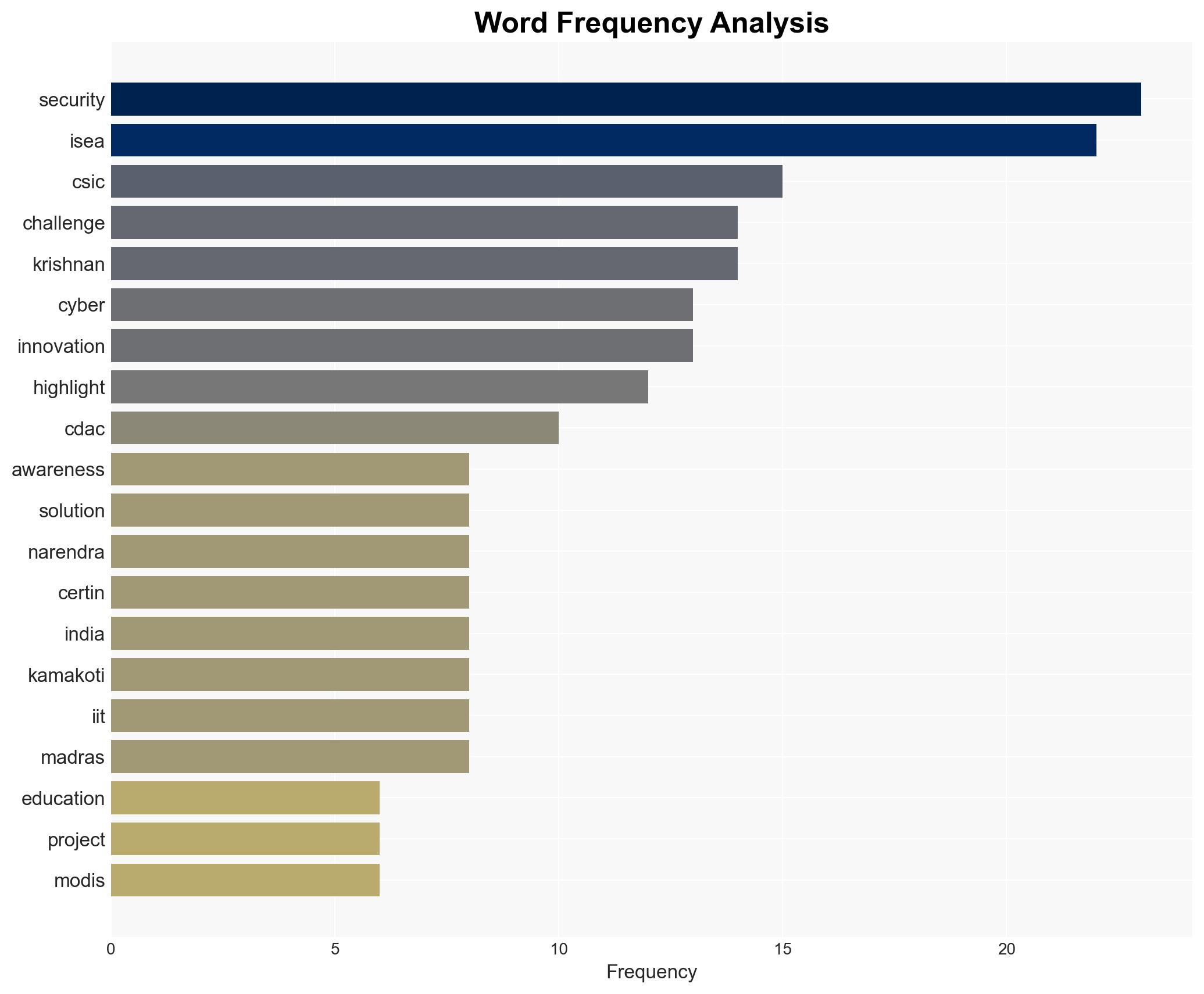
Krishnan (Secretary), Vinayak Godse (CEO, Data Security Council of India), Professor Kamakoti (Director, IIT Madras), Dr. Sanjay Bahl (Director General, CERT-In).
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us