New Malware Campaign Exploits User Behavior to Distribute DarkGate via Deceptive ClickFix Technique
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
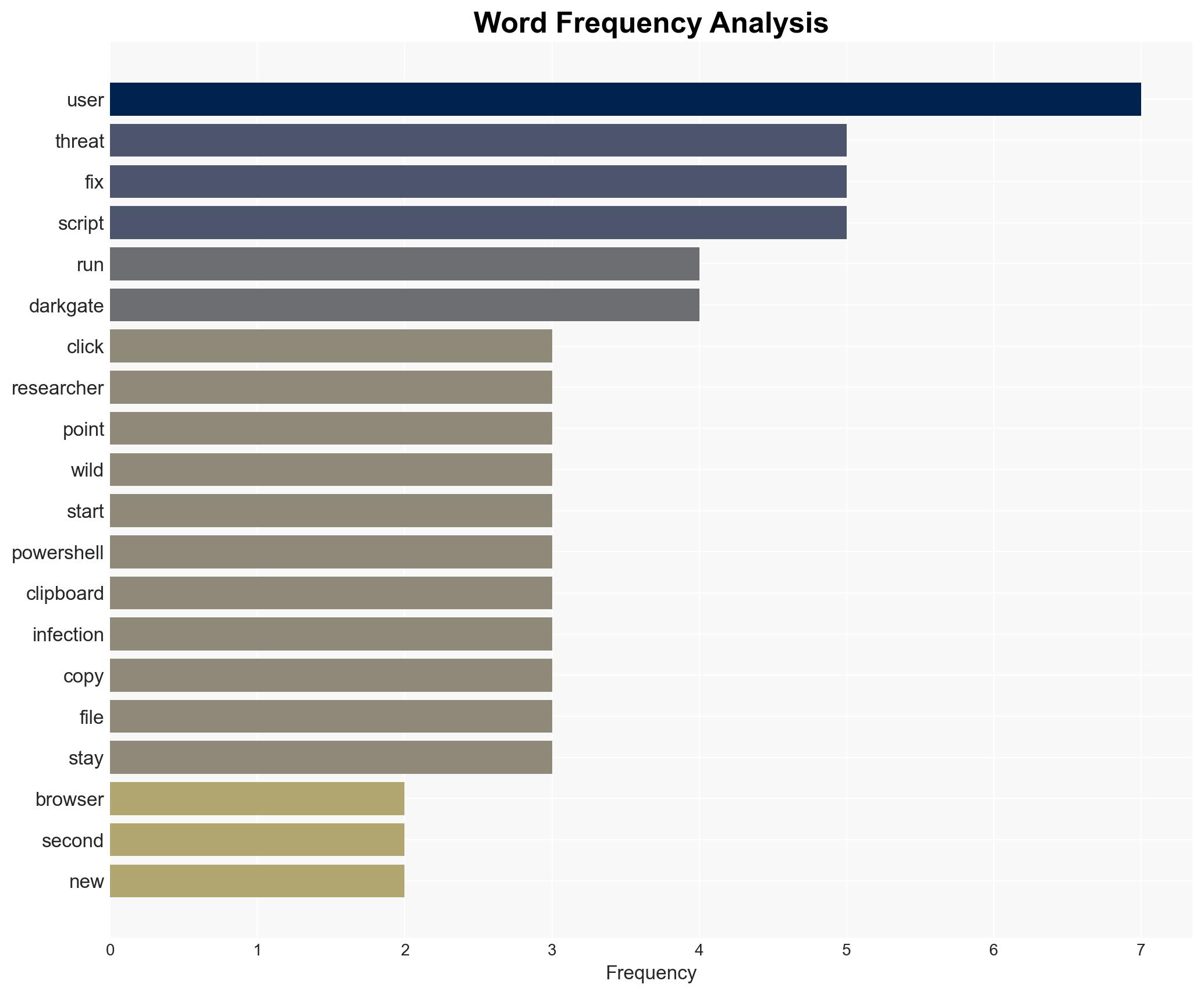
Intelligence Report: New ClickFix Attack Uses Fake Browser Fix to Install DarkGate Malware
1. BLUF (Bottom Line Up Front)
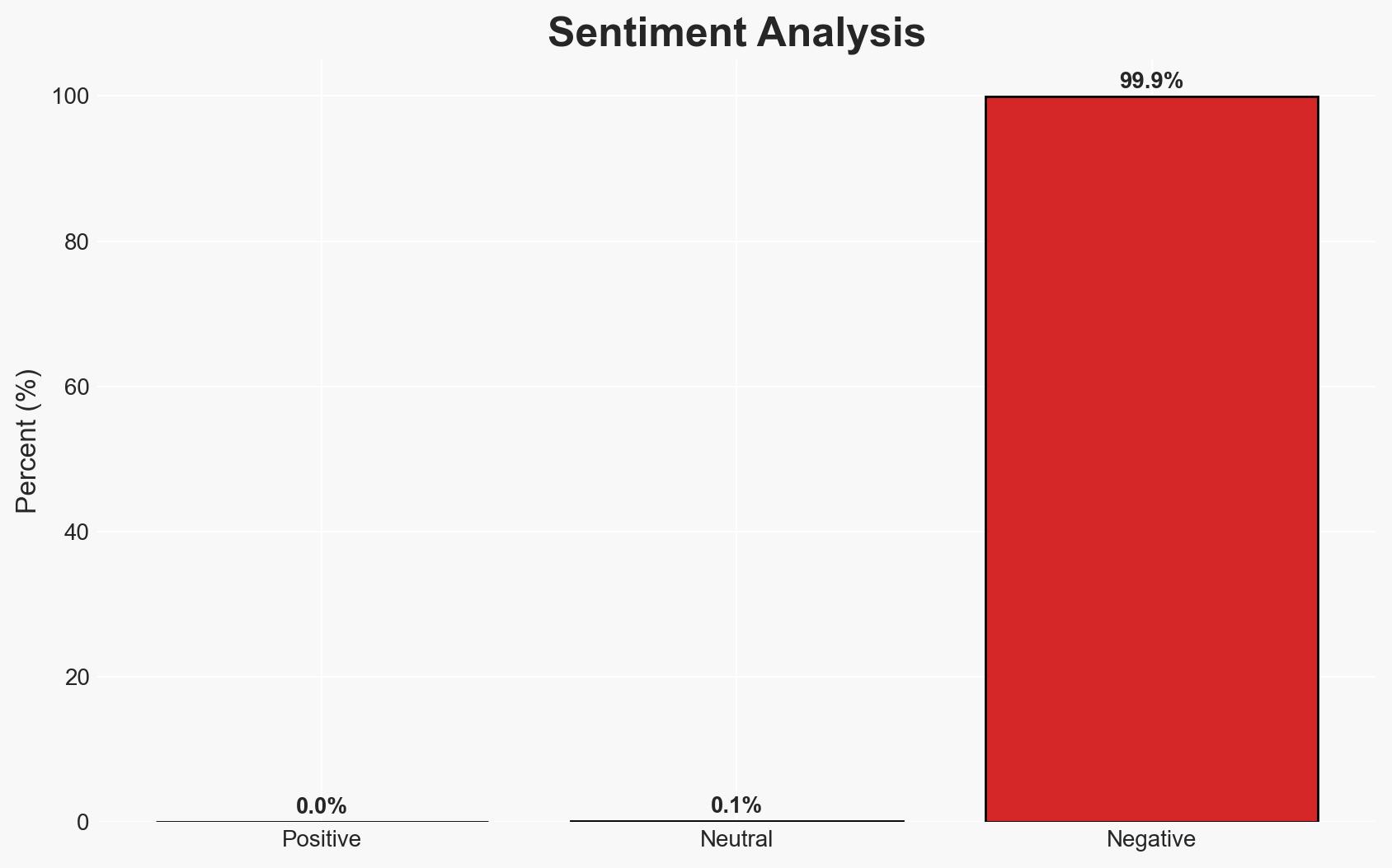
The ClickFix attack leverages social engineering to install the DarkGate malware by exploiting user habits of clicking through browser updates. This campaign primarily affects individual users and organizations with lax cybersecurity awareness. The most likely hypothesis is that this attack is part of a broader trend of sophisticated social engineering tactics. Overall confidence in this assessment is moderate due to limited information on the attackers’ identity and broader objectives.
2. Competing Hypotheses
- Hypothesis A: The ClickFix attack is primarily a financially motivated operation targeting a wide range of users to harvest sensitive information for monetary gain. This is supported by the malware’s capability to exfiltrate user data. However, the lack of specific targeting information introduces uncertainty.
- Hypothesis B: The attack is a state-sponsored operation aimed at gathering intelligence from specific targets under the guise of a broad campaign. This is less supported due to the generic nature of the attack vector and lack of evidence linking it to state actors.
- Assessment: Hypothesis A is currently better supported due to the attack’s broad targeting and the financial incentives typically associated with data exfiltration. Indicators such as specific targeting patterns or geopolitical tensions could shift this judgment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: Users will continue to engage in risky behavior by clicking through updates without scrutiny; traditional antivirus software will remain ineffective against initial infection stages; attackers seek financial gain through data exfiltration.
- Information Gaps: Lack of detailed attribution to specific threat actors; limited understanding of the full scope and scale of the campaign; insufficient data on the geographical distribution of affected users.
- Bias & Deception Risks: Potential confirmation bias in attributing the attack to financially motivated actors without considering alternative motives; deception risk from attackers using false flags to obscure true intent.
4. Implications and Strategic Risks
This development could lead to increased sophistication in social engineering attacks, potentially influencing broader cybersecurity practices and policies. The persistent nature of the malware poses ongoing risks to data integrity and privacy.
- Political / Geopolitical: Potential for increased tensions if state-sponsored involvement is confirmed, leading to diplomatic repercussions.
- Security / Counter-Terrorism: Heightened threat environment as similar tactics could be adopted by terrorist groups for disruptive purposes.
- Cyber / Information Space: Escalation in the arms race between malware developers and cybersecurity defenses, necessitating advanced detection and response capabilities.
- Economic / Social: Potential economic impact from data breaches and loss of consumer trust in digital platforms, affecting market stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase awareness campaigns on social engineering risks; enhance monitoring of suspicious activities related to PowerShell commands.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for intelligence sharing; invest in advanced threat detection technologies.
- Scenario Outlook: Best-case: Improved cybersecurity awareness reduces attack success; Worst-case: Attackers refine tactics leading to widespread breaches; Most-likely: Continued sporadic attacks with gradual improvements in detection and response.
6. Key Individuals and Entities
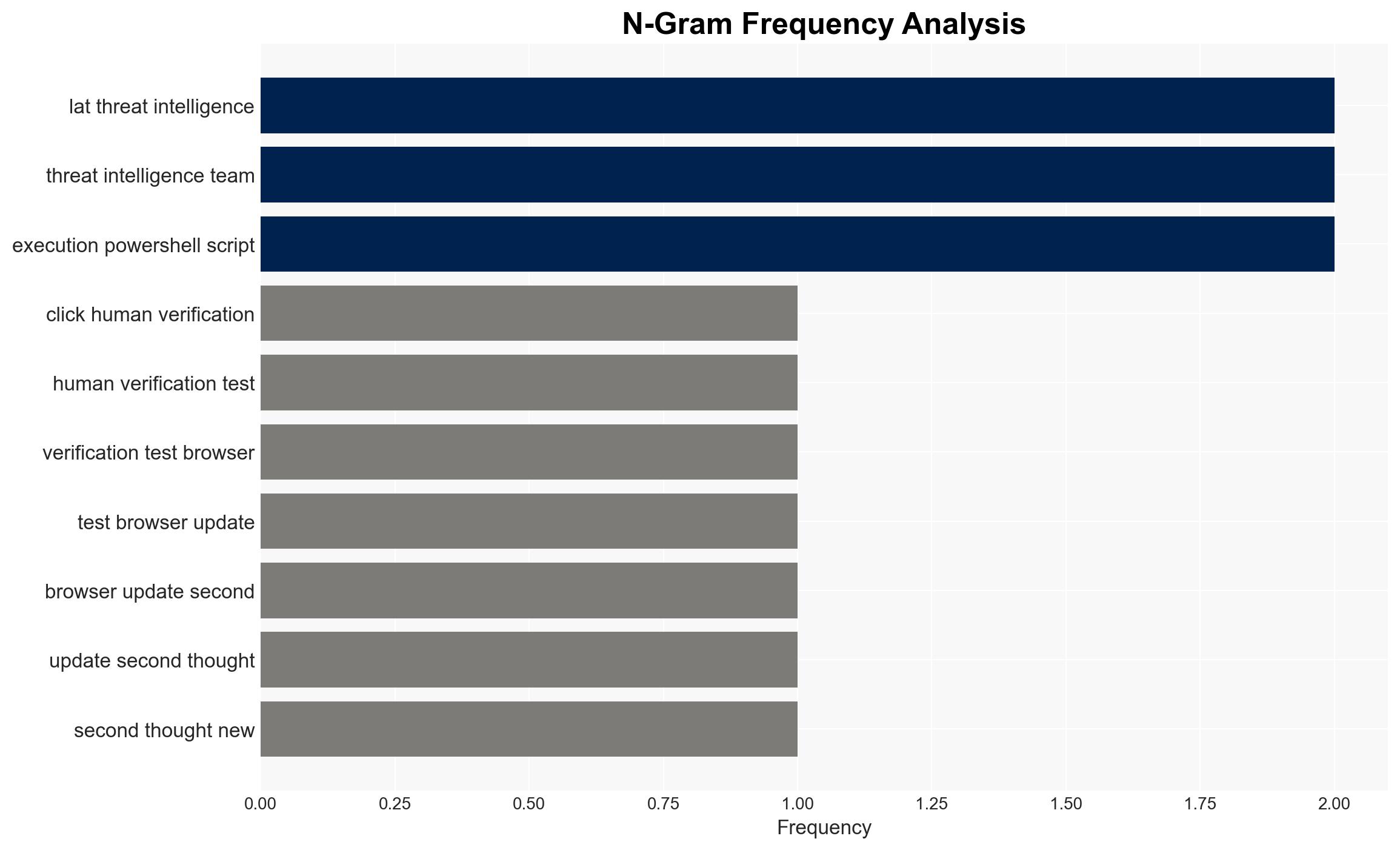
- Point Wild’s Lat61 Threat Intelligence Team
- Onkar Sonawane, Threat Analyst
- Dr. Zulfikar Ramzan, CTO of Point Wild
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, social engineering, malware, data exfiltration, threat intelligence, cyber defense, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us