New malware exploits trusted Windows drivers to get around security systems – here’s how to stay safe – TechRadar
Published on: 2025-09-02
Intelligence Report: New malware exploits trusted Windows drivers to get around security systems – here’s how to stay safe – TechRadar
1. BLUF (Bottom Line Up Front)
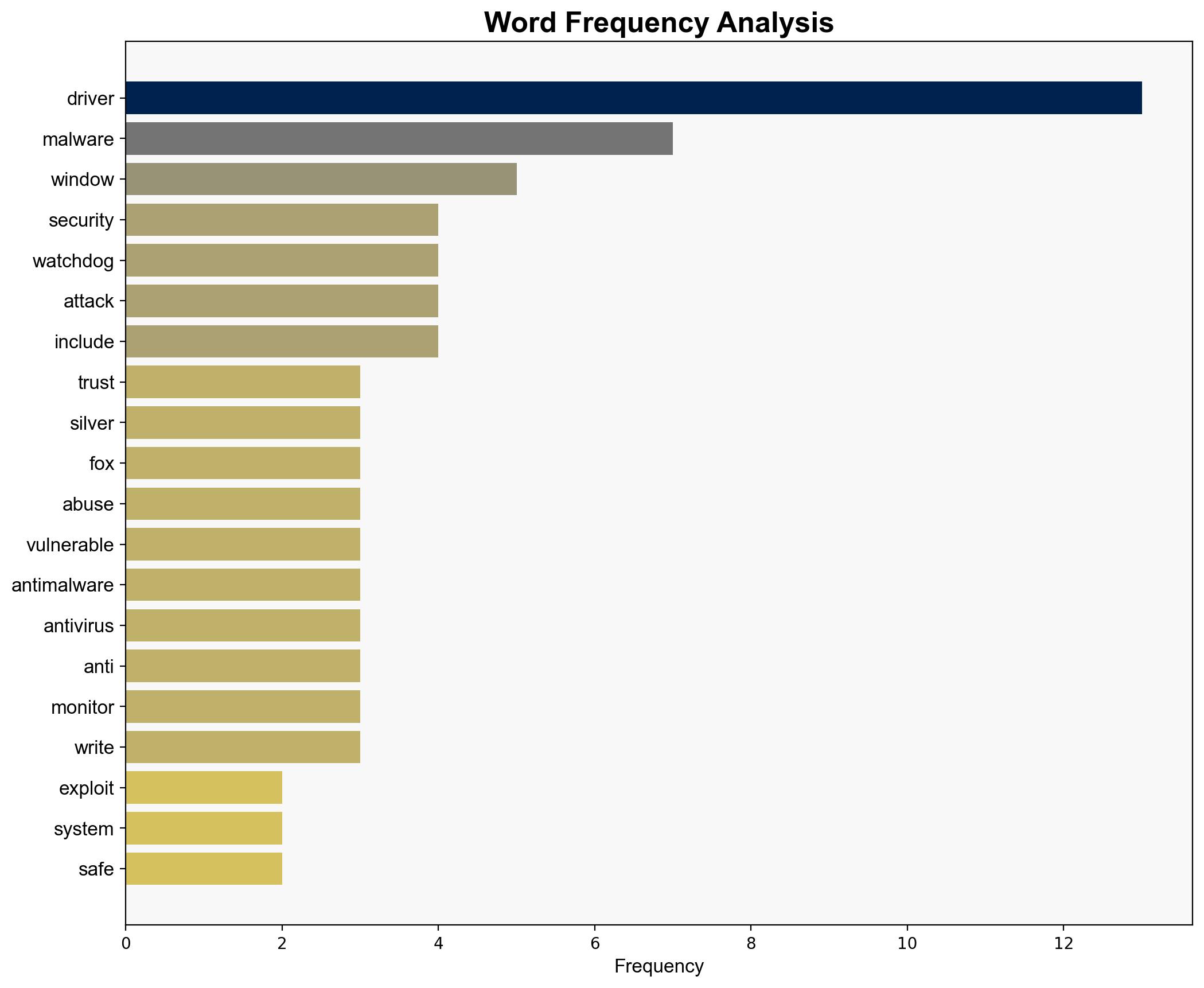
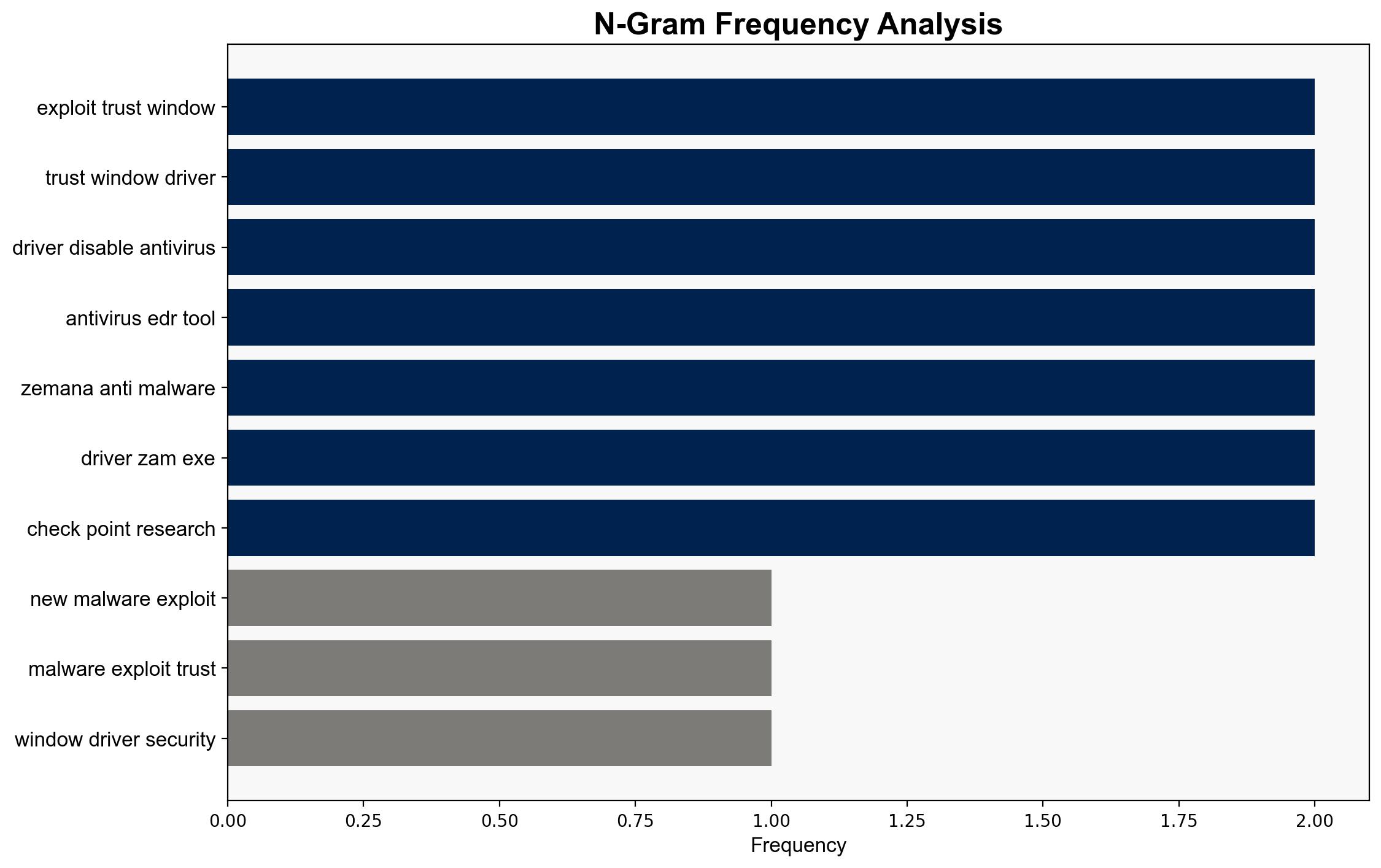
The exploitation of trusted Windows drivers by the Silver Fox group to bypass security systems poses a significant cybersecurity threat. The most supported hypothesis is that the Chinese threat group is leveraging these vulnerabilities for cyber espionage, targeting entities in East Asia. Recommended actions include updating blocklists, enhancing monitoring for suspicious activities, and deploying advanced threat detection systems. Confidence level: Moderate.
2. Competing Hypotheses
1. **Hypothesis 1**: The Silver Fox group is using the vulnerabilities in Windows drivers primarily for cyber espionage purposes, focusing on data exfiltration and intelligence gathering in East Asia.
2. **Hypothesis 2**: The exploitation of these vulnerabilities is part of a broader campaign aimed at disrupting critical infrastructure and causing widespread damage beyond espionage.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported by the evidence, particularly given the focus on data exfiltration and the historical context of similar activities by Chinese threat actors.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the Silver Fox group is state-sponsored, given the sophistication and targets of the attacks. It is also assumed that the vulnerabilities are being exploited primarily for espionage rather than sabotage.
– **Red Flags**: The lack of detailed attribution to specific individuals within the group and the potential for other threat actors to mimic these tactics.
– **Blind Spots**: Limited information on the full scope of the infrastructure targeted and the potential for collateral damage in non-targeted regions.
4. Implications and Strategic Risks
The exploitation of trusted drivers could lead to increased vulnerabilities across various sectors, including government, finance, and critical infrastructure. This could escalate into broader geopolitical tensions, especially if attribution to a state actor is confirmed. The psychological impact on public trust in digital security systems could also be significant.
5. Recommendations and Outlook
- **Mitigation**: Update and enforce driver blocklists, implement YARA rules for detection, and enhance network monitoring for suspicious activities.
- **Best Case Scenario**: Rapid patching and mitigation efforts prevent further exploitation, and international cooperation leads to a reduction in such attacks.
- **Worst Case Scenario**: The vulnerabilities are exploited on a larger scale, leading to significant data breaches and infrastructure disruptions.
- **Most Likely Scenario**: Continued targeted attacks in East Asia with gradual spread to other regions, prompting increased cybersecurity measures globally.
6. Key Individuals and Entities
– Silver Fox group (Chinese threat group)
– Check Point Research (CPR)
– Microsoft (involved in driver blocklist updates)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus