New Zealand health minister initiates investigation into ManageMyHealth data breach affecting hundreds of tho…
Published on: 2026-01-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: New Zealand orders review into ManageMyHealth cyberattack
1. BLUF (Bottom Line Up Front)
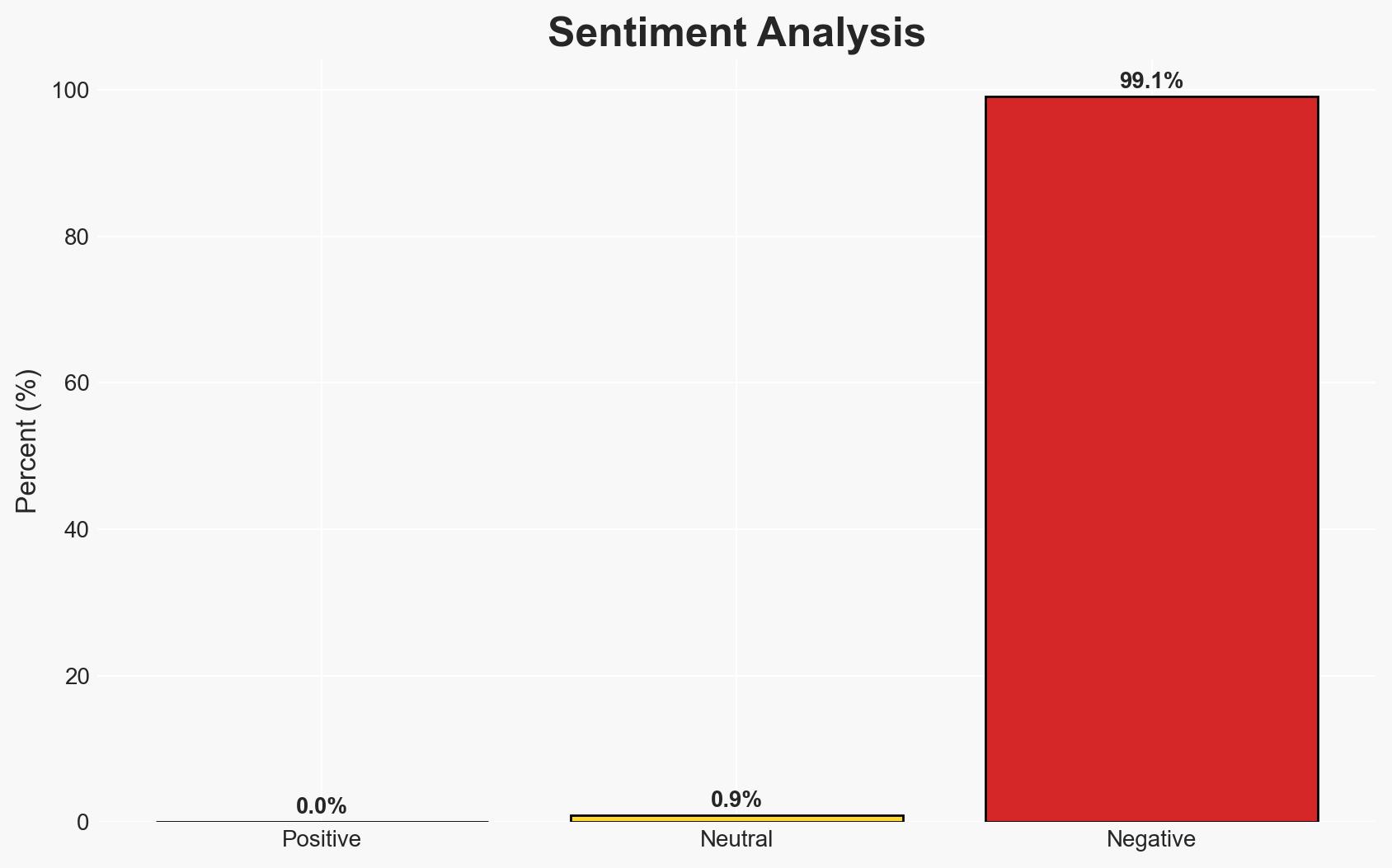
The cyberattack on ManageMyHealth has compromised sensitive health data of over 100,000 New Zealanders, with potential broader impacts on national data security practices. The most likely hypothesis is that the attack was financially motivated, evidenced by the ransom demand. The incident underscores vulnerabilities in private sector data protection. Overall confidence in this assessment is moderate due to limited information on the attack’s specifics and the perpetrator’s capabilities.
2. Competing Hypotheses
- Hypothesis A: The attack was financially motivated, as indicated by the ransom demand and threat to release data. This is supported by the behavior of the alleged perpetrator, Kazu, who used a cybercrime forum to announce the ransom and threatened data exposure. Key uncertainties include the true identity and capabilities of Kazu.
- Hypothesis B: The attack was politically or ideologically motivated, aiming to undermine trust in New Zealand’s healthcare data systems. This is less supported due to the lack of political demands or statements accompanying the attack.
- Assessment: Hypothesis A is currently better supported due to the explicit ransom demand and lack of political messaging. Indicators that could shift this judgment include evidence of state sponsorship or political statements from the attacker.
3. Key Assumptions and Red Flags
- Assumptions: The attacker is acting independently and not as part of a larger group; the ransom demand is genuine and not a diversion; New Zealand’s cybersecurity infrastructure is comparable to other Western nations.
- Information Gaps: Full extent of data compromised; technical details of the breach; identity and motives of the attacker.
- Bias & Deception Risks: Potential bias in reporting from ManageMyHealth to minimize reputational damage; possible deception by the attacker regarding their identity and intentions.
4. Implications and Strategic Risks
This incident could lead to increased scrutiny of private sector data security practices and potentially stricter regulatory measures in New Zealand. It may also influence public trust in digital health services.
- Political / Geopolitical: Potential for increased regulatory oversight and international collaboration on cybersecurity standards.
- Security / Counter-Terrorism: Heightened alertness to cyber threats targeting critical infrastructure.
- Cyber / Information Space: Possible increase in cyber defense investments and public-private partnerships in cybersecurity.
- Economic / Social: Potential economic impact on ManageMyHealth and similar companies; public concern over privacy and data security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cyber threats, engage with international cybersecurity partners, and support ManageMyHealth in incident response.
- Medium-Term Posture (1–12 months): Develop comprehensive data protection regulations, invest in cybersecurity infrastructure, and conduct public awareness campaigns on data security.
- Scenario Outlook:
- Best: Successful containment of the breach and no further data exposure; improved cybersecurity measures.
- Worst: Data is released, leading to widespread identity theft and loss of trust in digital health services.
- Most-Likely: Partial data exposure with increased regulatory scrutiny and gradual improvement in data security practices.
6. Key Individuals and Entities
- Simeon Brown – New Zealand Health Minister
- ManageMyHealth – Private company handling health data
- Kazu – Alleged perpetrator of the cyberattack
- Cody Cooper – IT consultant who investigated the data
7. Thematic Tags
cybersecurity, data breach, healthcare, ransom, New Zealand, private sector, regulatory response
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us