NHS recruitment firm had major security bugs which could have exposed entire systems – TechRadar
Published on: 2025-06-13
Intelligence Report: NHS Recruitment Firm Security Vulnerabilities – TechRadar
1. BLUF (Bottom Line Up Front)
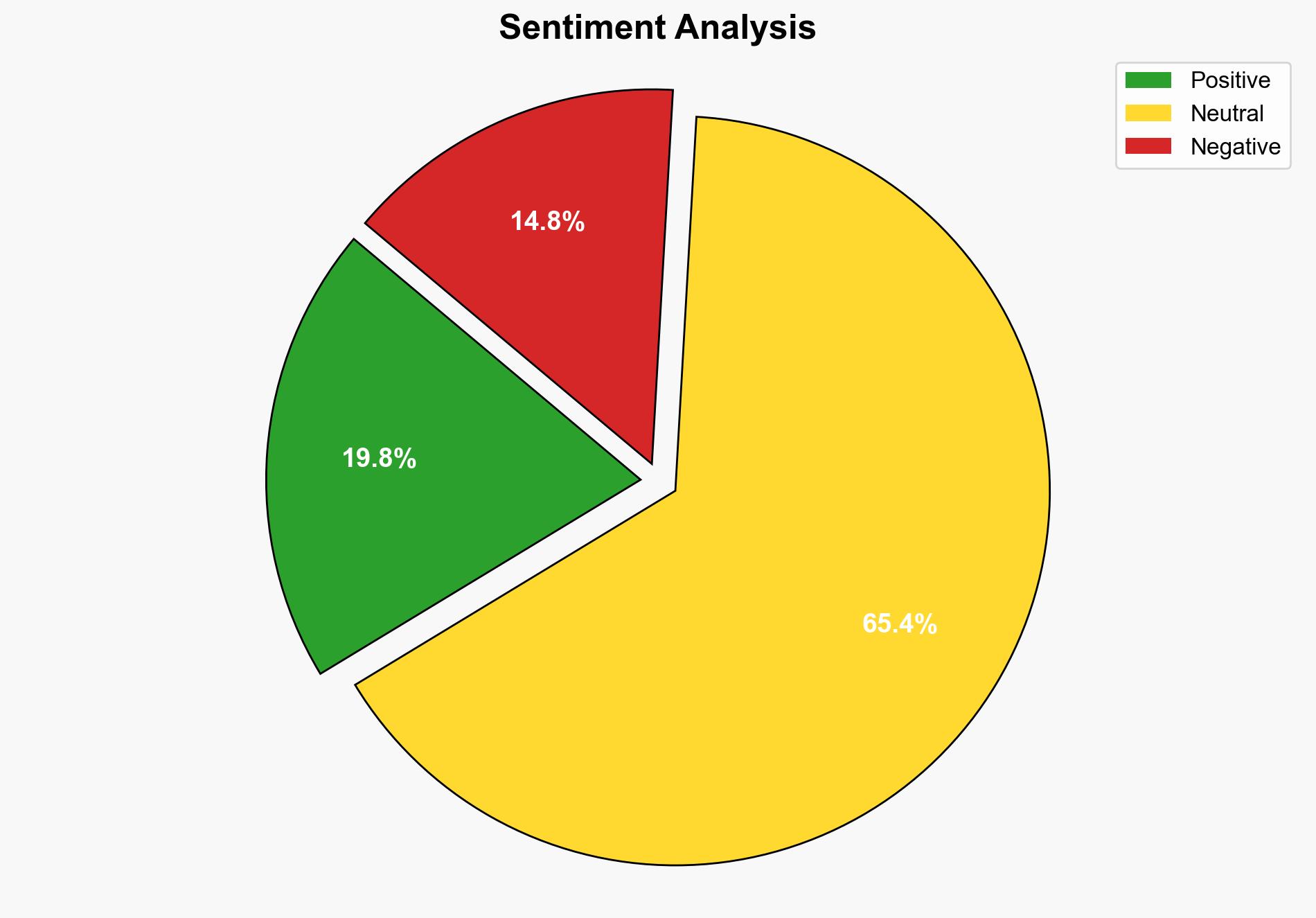
A significant security breach at an NHS recruitment firm exposed critical vulnerabilities, potentially compromising NHS systems. The breach involved unauthorized access to sensitive data, including Active Directory files. Immediate action is required to enhance cybersecurity measures, particularly through the implementation of multi-factor authentication (MFA) and advanced endpoint detection solutions.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated scenarios suggest that attackers exploited weak authentication protocols to gain initial access, emphasizing the need for robust identity verification processes.
Indicators Development
Key indicators include unauthorized access attempts, unusual network activity, and data exfiltration patterns, which should be monitored continuously.
Bayesian Scenario Modeling
Probabilistic models predict a high likelihood of similar attacks if current vulnerabilities remain unaddressed, with potential for significant operational disruption.
Network Influence Mapping
Analysis of network interactions highlights critical nodes and pathways that could be targeted in future attacks, necessitating enhanced security protocols.
3. Implications and Strategic Risks
The breach underscores systemic vulnerabilities within NHS-associated networks, posing risks to national healthcare infrastructure. Failure to address these could lead to widespread service disruptions and data breaches, impacting public trust and safety.
4. Recommendations and Outlook
- Implement multi-factor authentication (MFA) across all systems to prevent unauthorized access.
- Deploy advanced endpoint detection and response solutions to identify and mitigate threats in real-time.
- Conduct regular security audits and penetration testing to identify and rectify vulnerabilities.
- Scenario-based projections suggest that, in the best case, enhanced security measures will deter future attacks. In the worst case, failure to act could result in repeated breaches and significant data loss.
5. Key Individuals and Entities
Deloitte, Scatter Spider
6. Thematic Tags
national security threats, cybersecurity, healthcare infrastructure, data protection