Nigerian Army rescues 31 kidnapped individuals and detains 17 suspects in recent operations across multiple s…
Published on: 2026-01-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Army rescues 31 kidnap victims arrests 17 suspects
1. BLUF (Bottom Line Up Front)
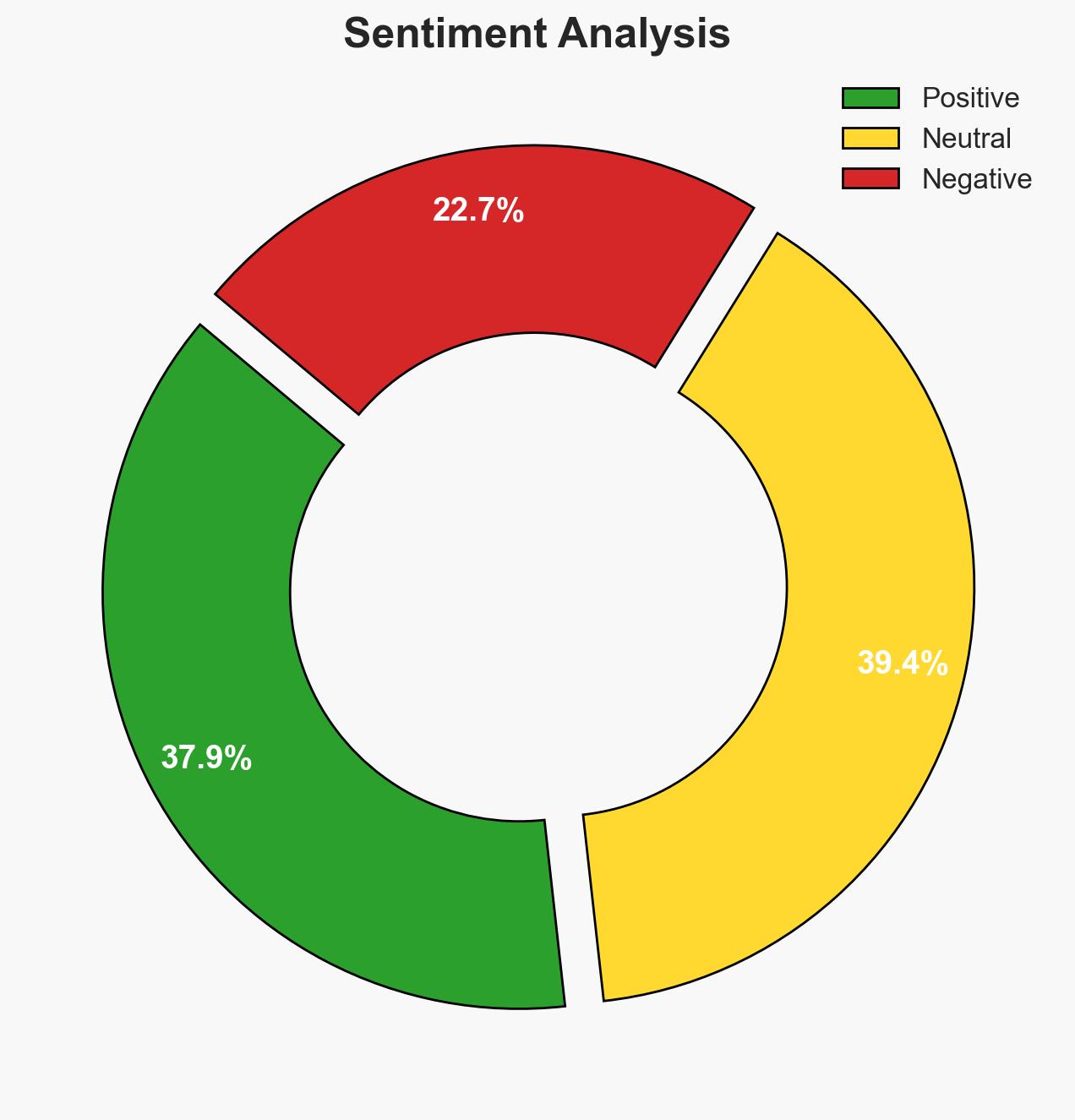
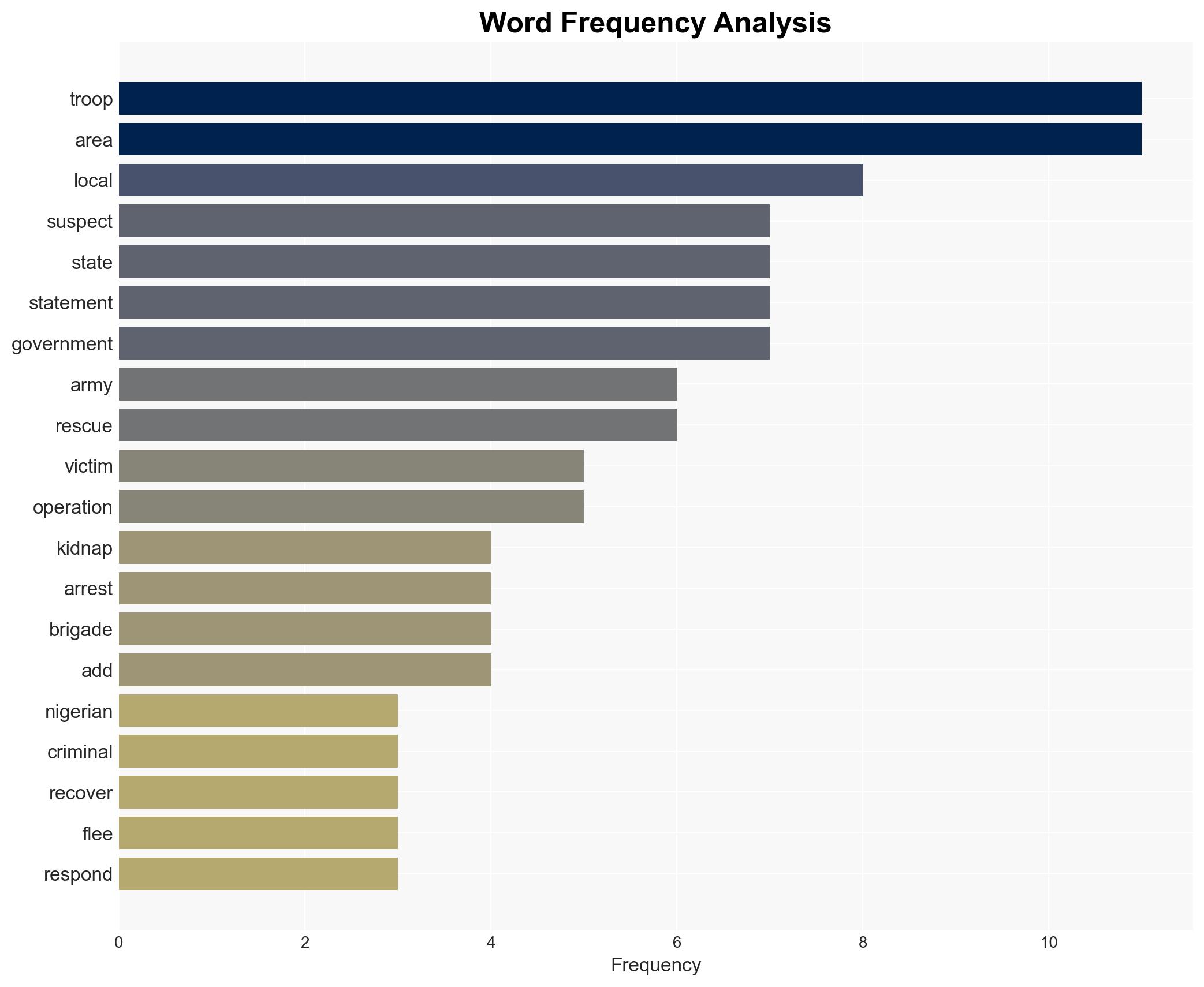
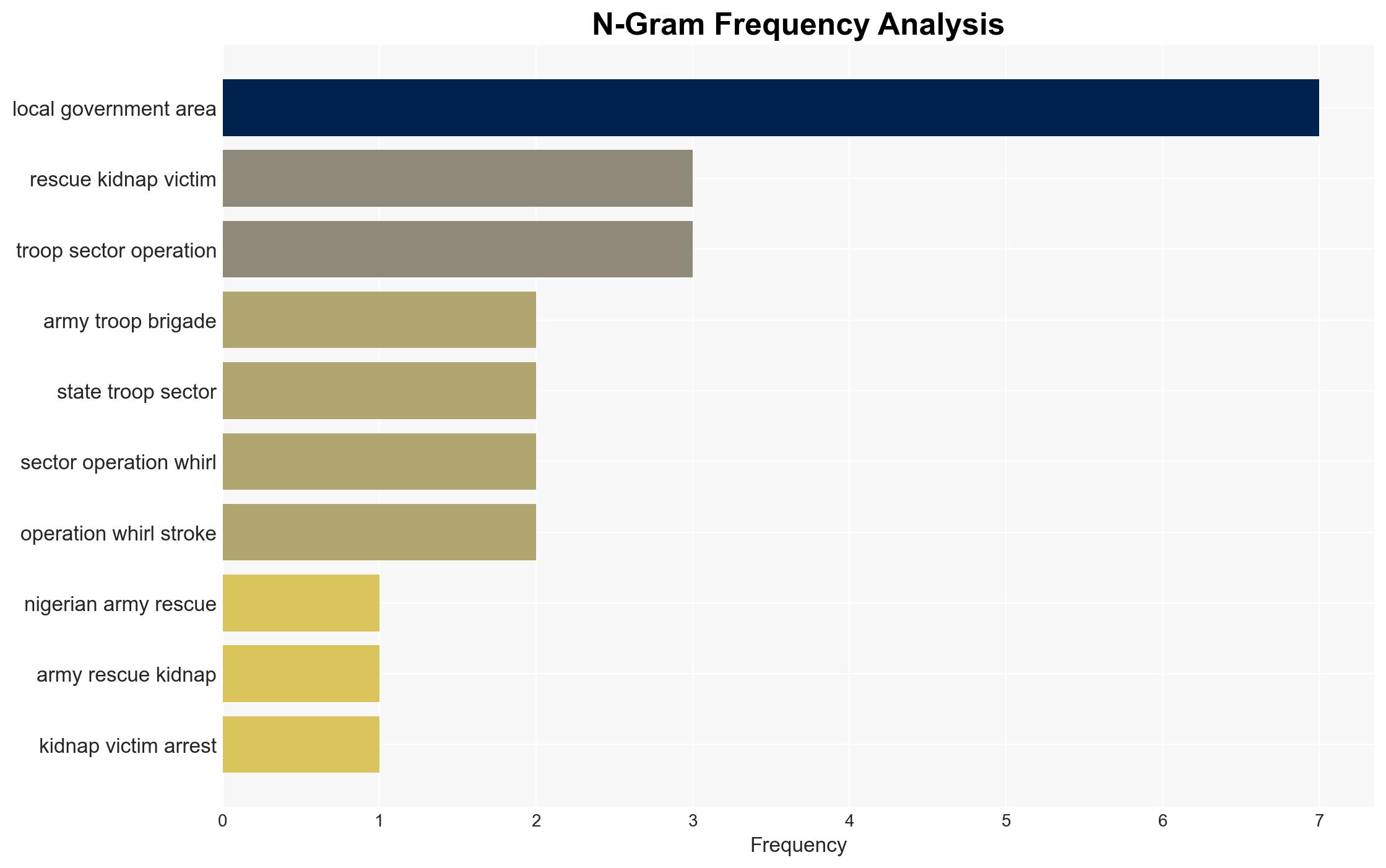
The Nigerian Army’s recent operations have led to the rescue of 31 kidnap victims and the arrest of 17 suspects across multiple states, indicating a significant disruption of criminal activities in the region. The operations highlight the effectiveness of coordinated military and intelligence efforts, though challenges remain in fully dismantling these networks. Overall confidence in this assessment is moderate, given the limited scope of available data.
2. Competing Hypotheses
- Hypothesis A: The Nigerian Army’s operations reflect a strategic and effective response to rising criminal activities, supported by intelligence and local collaboration. Evidence includes successful rescues and arrests, but uncertainties remain regarding the long-term sustainability of these efforts.
- Hypothesis B: The operations are primarily reactive and may not significantly impact the broader criminal networks. While immediate results are evident, the lack of detailed information on dismantling organizational structures contradicts long-term effectiveness.
- Assessment: Hypothesis A is currently better supported due to the immediate tactical successes and collaboration with local entities. However, indicators such as sustained criminal activity or resurgence could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The Nigerian Army has adequate resources for sustained operations; local collaboration will continue; intelligence is accurate and actionable.
- Information Gaps: Details on the organizational structure of the criminal networks; long-term strategic plans of the Nigerian Army; the extent of local community support.
- Bias & Deception Risks: Potential over-reliance on military sources; lack of independent verification; possible exaggeration of successes for morale or propaganda purposes.
4. Implications and Strategic Risks
The operations could lead to a temporary reduction in criminal activities, but without addressing root causes, such activities may resurge. Continued military presence may strain resources and affect civilian-military relations.
- Political / Geopolitical: Successful operations may bolster government legitimacy but could also provoke retaliatory actions by criminal groups.
- Security / Counter-Terrorism: Short-term improvements in security are likely, but long-term stability requires dismantling criminal networks.
- Cyber / Information Space: Limited direct impact, though misinformation or propaganda could be leveraged by criminal elements to undermine military efforts.
- Economic / Social: Improved security may enhance economic activities, but social cohesion could be affected if operations lead to civilian casualties or property damage.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence-sharing mechanisms; increase community engagement to gather local support and information.
- Medium-Term Posture (1–12 months): Develop comprehensive strategies to dismantle criminal networks; invest in capacity building for local law enforcement.
- Scenario Outlook: Best: Sustained reduction in criminal activities with improved local security. Worst: Resurgence of criminal activities due to inadequate follow-up. Most-Likely: Continued tactical successes with intermittent challenges.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
national security threats, counter-terrorism, military operations, kidnapping, criminal networks, intelligence collaboration, regional security, law enforcement
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us