Nike Faces Major Data Breach as World Leaks Ransomware Group Exposes 14TB of Internal Files
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: World Leaks Ransomware Group Claims 14TB Nike Data Breach
1. BLUF (Bottom Line Up Front)
The World Leaks ransomware group has claimed responsibility for a significant data breach at Nike, exposing 14TB of sensitive internal data. This breach, primarily affecting Nike’s operational and strategic environments, poses substantial commercial and supply chain risks. The most likely hypothesis is that the breach resulted from unpatched vulnerabilities within Nike’s supply chain. Overall confidence in this assessment is moderate due to incomplete information on the breach’s origin and scope.
2. Competing Hypotheses
- Hypothesis A: The breach resulted from unpatched vulnerabilities in Nike’s supply chain systems. Supporting evidence includes rumors of such vulnerabilities and the nature of the compromised data, which includes supply chain information. However, the specific vulnerabilities exploited have not been confirmed, creating uncertainty.
- Hypothesis B: The breach was facilitated by insider threats or credential compromise. This hypothesis is less supported due to the lack of direct evidence pointing to insider involvement or credential misuse, though it remains a plausible alternative given the depth of the compromise.
- Assessment: Hypothesis A is currently better supported due to the alignment of the compromised data types with supply chain vulnerabilities. Key indicators that could shift this judgment include new evidence of insider involvement or confirmation of specific exploited vulnerabilities.
3. Key Assumptions and Red Flags
- Assumptions: Nike’s cybersecurity measures were insufficient to prevent the breach; the World Leaks group has accurately reported the data volume and types compromised; the breach primarily affects internal data without PII exposure.
- Information Gaps: Specific vulnerabilities exploited, the exact method of data exfiltration, and potential insider involvement remain unclear.
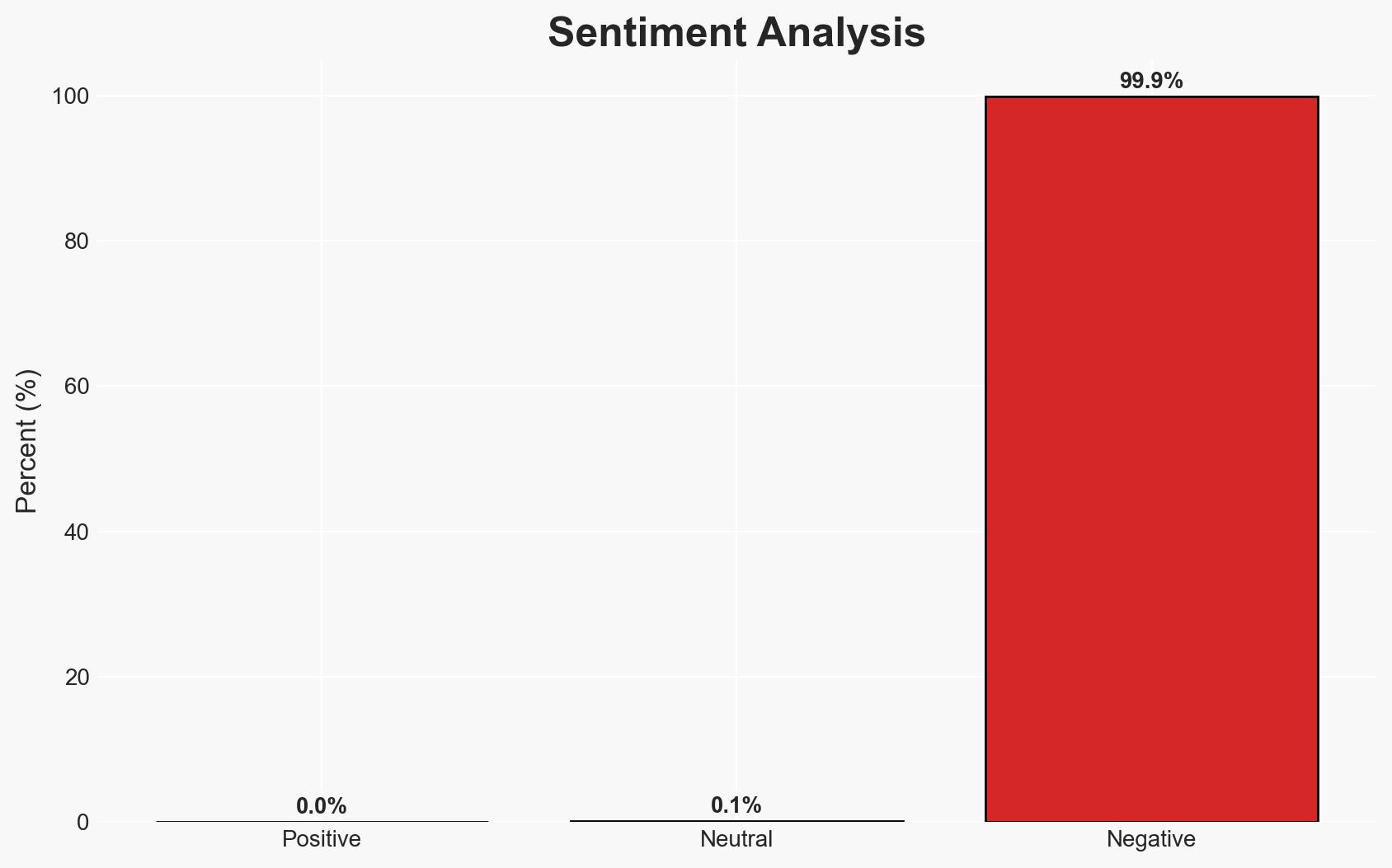
- Bias & Deception Risks: Potential bias in threat intelligence sources like Justabreach; World Leaks may exaggerate the breach’s impact for extortion purposes.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of Nike’s cybersecurity practices and influence broader industry standards. The breach may also encourage similar attacks on other high-profile companies.
- Political / Geopolitical: Potential for increased regulatory pressure on multinational corporations to enhance cybersecurity measures.
- Security / Counter-Terrorism: Heightened risk of supply chain disruptions and potential exploitation by state or non-state actors.
- Cyber / Information Space: Increased risk of data exploitation by competitors and counterfeiters; potential for further breaches if vulnerabilities remain unaddressed.
- Economic / Social: Possible financial losses for Nike and its partners; reputational damage impacting consumer trust and market position.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of supply chain systems; enhance monitoring for further breaches; engage with cybersecurity experts to patch vulnerabilities.
- Medium-Term Posture (1–12 months): Develop resilience measures, including enhanced cybersecurity training for employees and partners; establish stronger partnerships with cybersecurity firms.
- Scenario Outlook:
- Best Case: Rapid containment and patching of vulnerabilities, minimizing commercial impact.
- Worst Case: Further exploitation of compromised data leading to significant financial and reputational damage.
- Most-Likely: Gradual recovery with increased security measures and minor disruptions to operations.
6. Key Individuals and Entities
- World Leaks ransomware group
- Nike Inc.
- Justabreach (threat intelligence group)
- Halcyon (anti-ransomware specialist)
- Pete Luban, Field CISO at AttackIQ
7. Thematic Tags
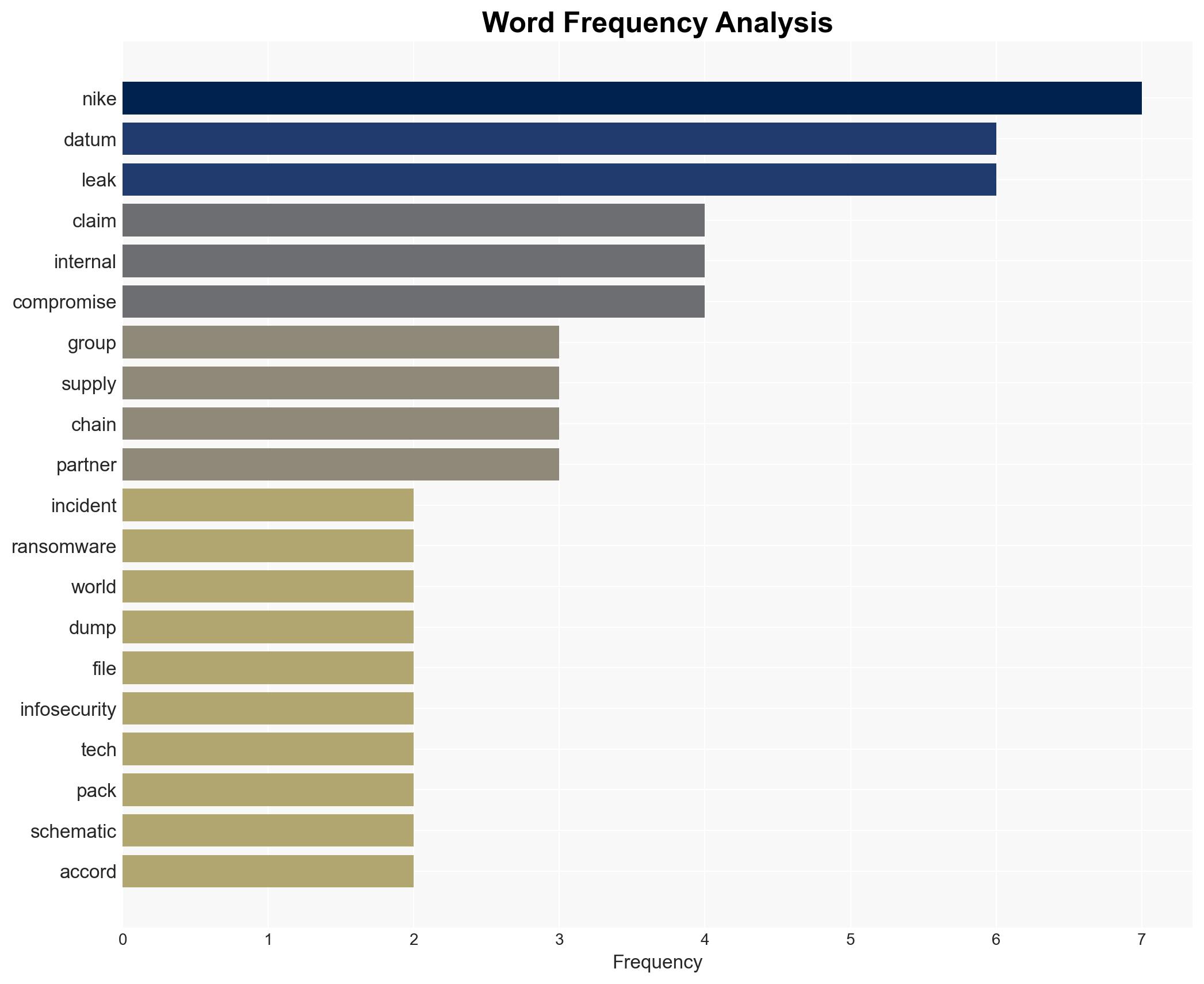
cybersecurity, ransomware, supply chain risk, data breach, corporate espionage, information security, extortion
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us