Noname057 Hacking Group Claims Responsibility for Cyberattack Disrupting La Poste Services
Published on: 2025-12-26
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pro-Russian group Noname057 claims cyberattack on La Poste services
1. BLUF (Bottom Line Up Front)
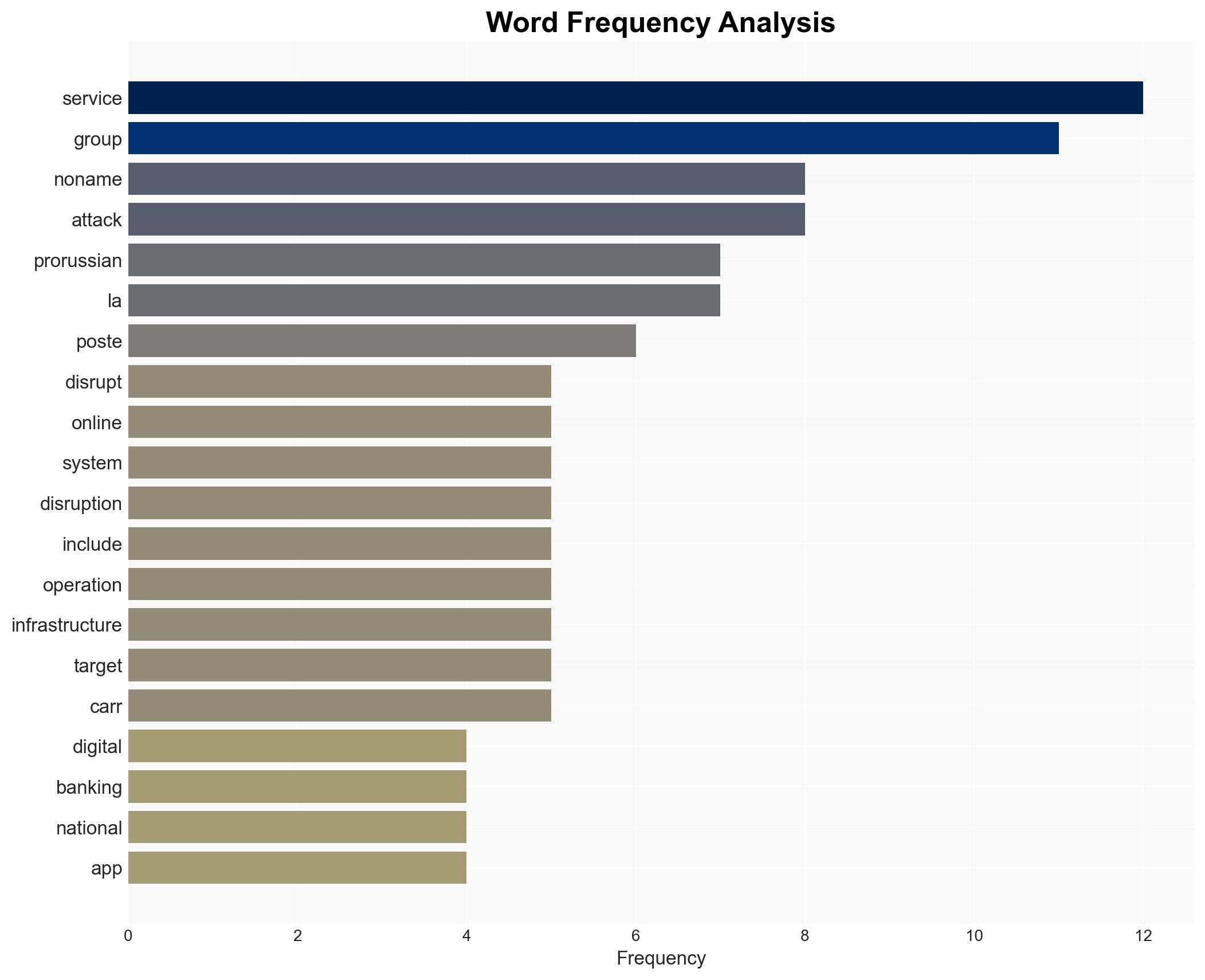
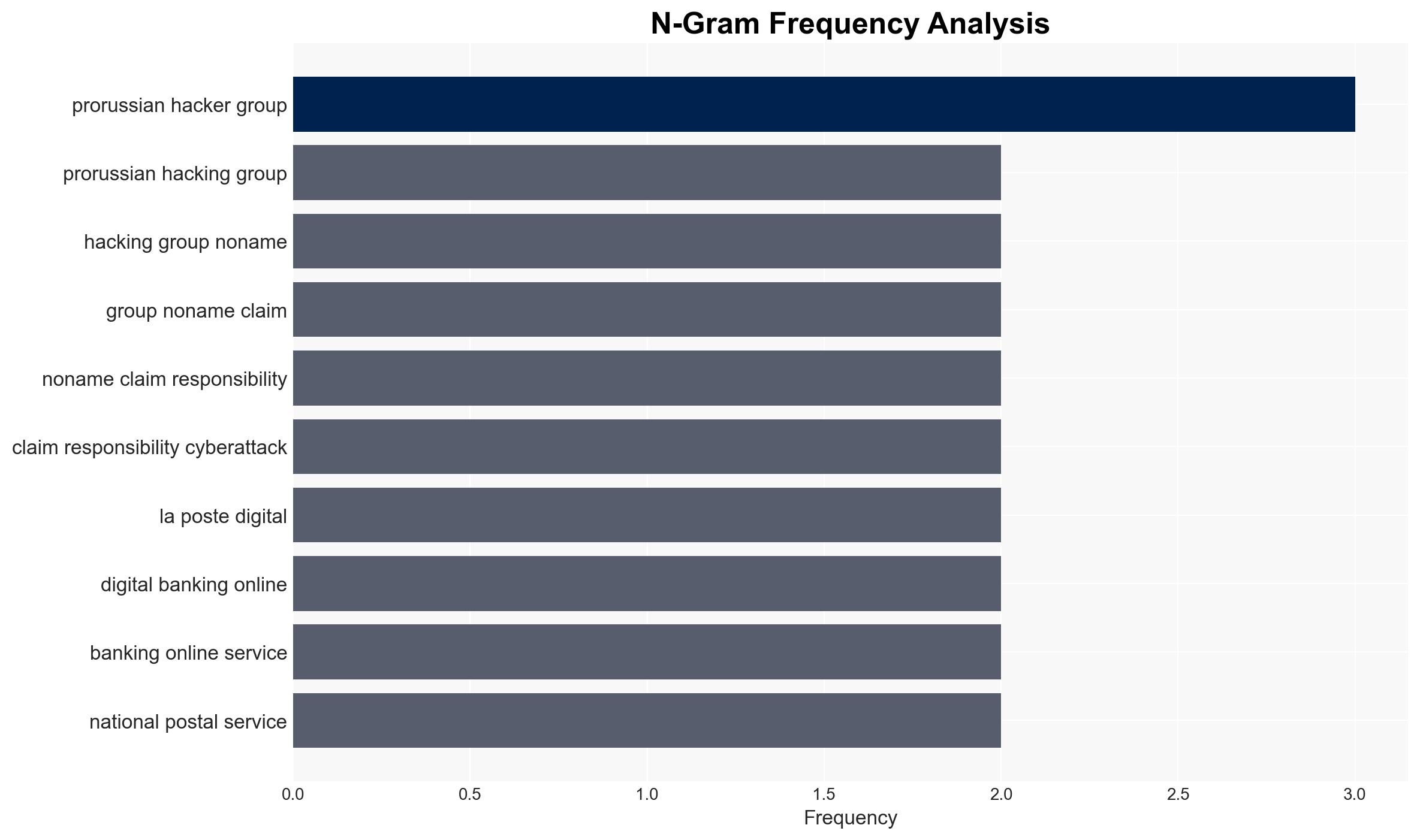
The pro-Russian hacking group Noname057 has claimed responsibility for a cyberattack on France’s La Poste, disrupting digital banking and online services. This incident highlights the group’s continued activity despite previous law enforcement actions. The most likely hypothesis is that this attack is part of a broader campaign against NATO-supporting countries. Overall confidence in this assessment is moderate, given the group’s known capabilities and recent activities.
2. Competing Hypotheses
- Hypothesis A: Noname057 conducted the attack as part of a coordinated campaign targeting countries supporting Ukraine. This is supported by the group’s history of targeting NATO members and the timing of the attack during a high-traffic period. However, there is uncertainty regarding the group’s current operational capacity post-Operation Eastwood.
- Hypothesis B: The attack was opportunistic, leveraging vulnerabilities in La Poste’s systems without a broader strategic objective. This is contradicted by the group’s previous patterns of ideologically motivated attacks and the coordinated nature of the disruption.
- Assessment: Hypothesis A is currently better supported due to the alignment with Noname057’s known objectives and recent activities. Indicators that could shift this judgment include evidence of unrelated opportunistic cybercriminal activity or new intelligence on the group’s operational changes post-disruption.
3. Key Assumptions and Red Flags
- Assumptions: Noname057 retains some operational capacity despite recent disruptions; the attack aligns with the group’s ideological motivations; La Poste’s systems were vulnerable to DDoS attacks.
- Information Gaps: Detailed technical analysis of the attack vectors used; current organizational structure and capabilities of Noname057 post-Operation Eastwood.
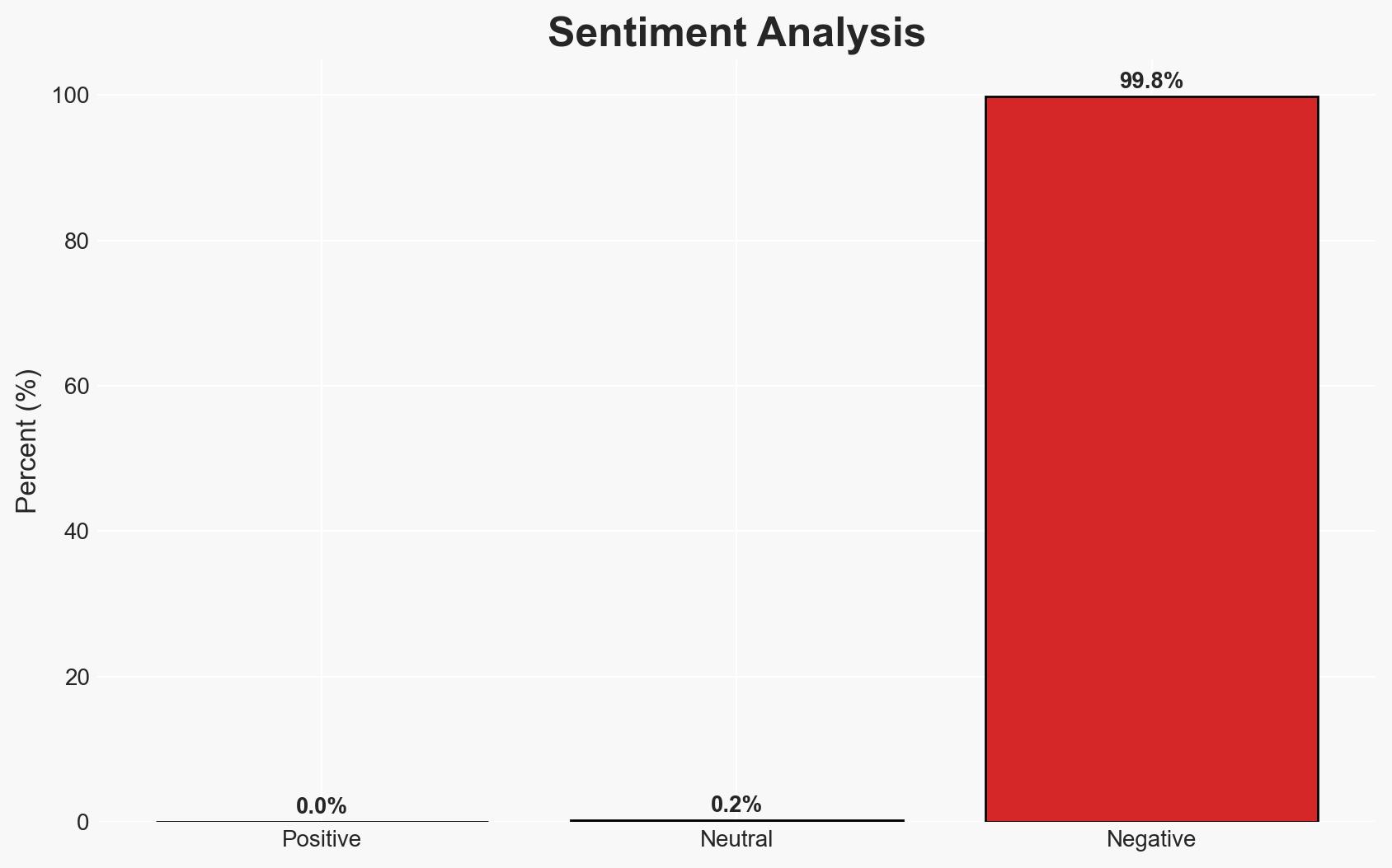
- Bias & Deception Risks: Potential over-reliance on publicly claimed responsibility by Noname057; confirmation bias towards attributing attacks to known actors without sufficient evidence.
4. Implications and Strategic Risks
This cyberattack could signal a resurgence in Noname057’s activities, potentially leading to increased targeting of European infrastructure. The incident underscores vulnerabilities in critical national services and may provoke further geopolitical tensions.
- Political / Geopolitical: Potential escalation in cyber hostilities between Russia-aligned groups and NATO countries, impacting diplomatic relations.
- Security / Counter-Terrorism: Increased threat environment for critical infrastructure, necessitating heightened security measures.
- Cyber / Information Space: Potential for copycat attacks and increased cyber operations targeting public trust in national institutions.
- Economic / Social: Disruptions to financial services could affect consumer confidence and economic stability, particularly if prolonged.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cyber threats to critical infrastructure, conduct vulnerability assessments, and engage in public communication to manage consumer expectations.
- Medium-Term Posture (1–12 months): Strengthen international cyber defense partnerships, invest in resilience measures for critical services, and develop rapid response capabilities.
- Scenario Outlook:
- Best: Successful mitigation and no further attacks, leading to improved cyber defenses.
- Worst: Escalation of attacks causing widespread disruption and economic impact.
- Most-Likely: Continued sporadic attacks with limited impact, prompting gradual improvements in cyber resilience.
6. Key Individuals and Entities
- Noname057 (Pro-Russian hacking group)
- La Poste (French national postal service)
- DGSI (French intelligence agency)
- Operation Eastwood (Law enforcement operation)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, pro-Russian hacking, critical infrastructure, NATO, cyber defense, digital banking, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us