Noodlophile infostealer is hiding behind fake copyright and PI infringement notices – Help Net Security
Published on: 2025-08-18
Intelligence Report: Noodlophile infostealer is hiding behind fake copyright and PI infringement notices – Help Net Security
1. BLUF (Bottom Line Up Front)
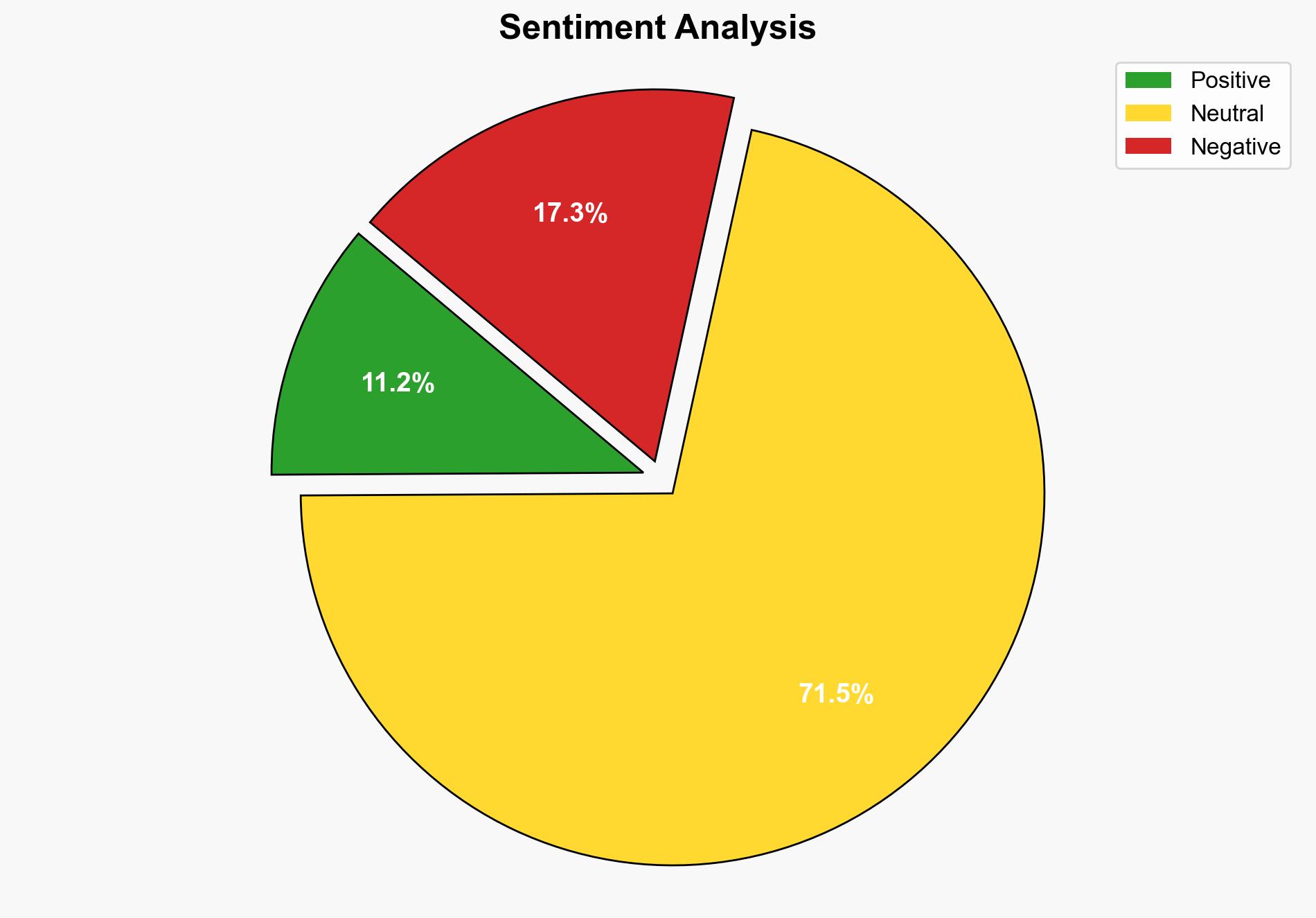
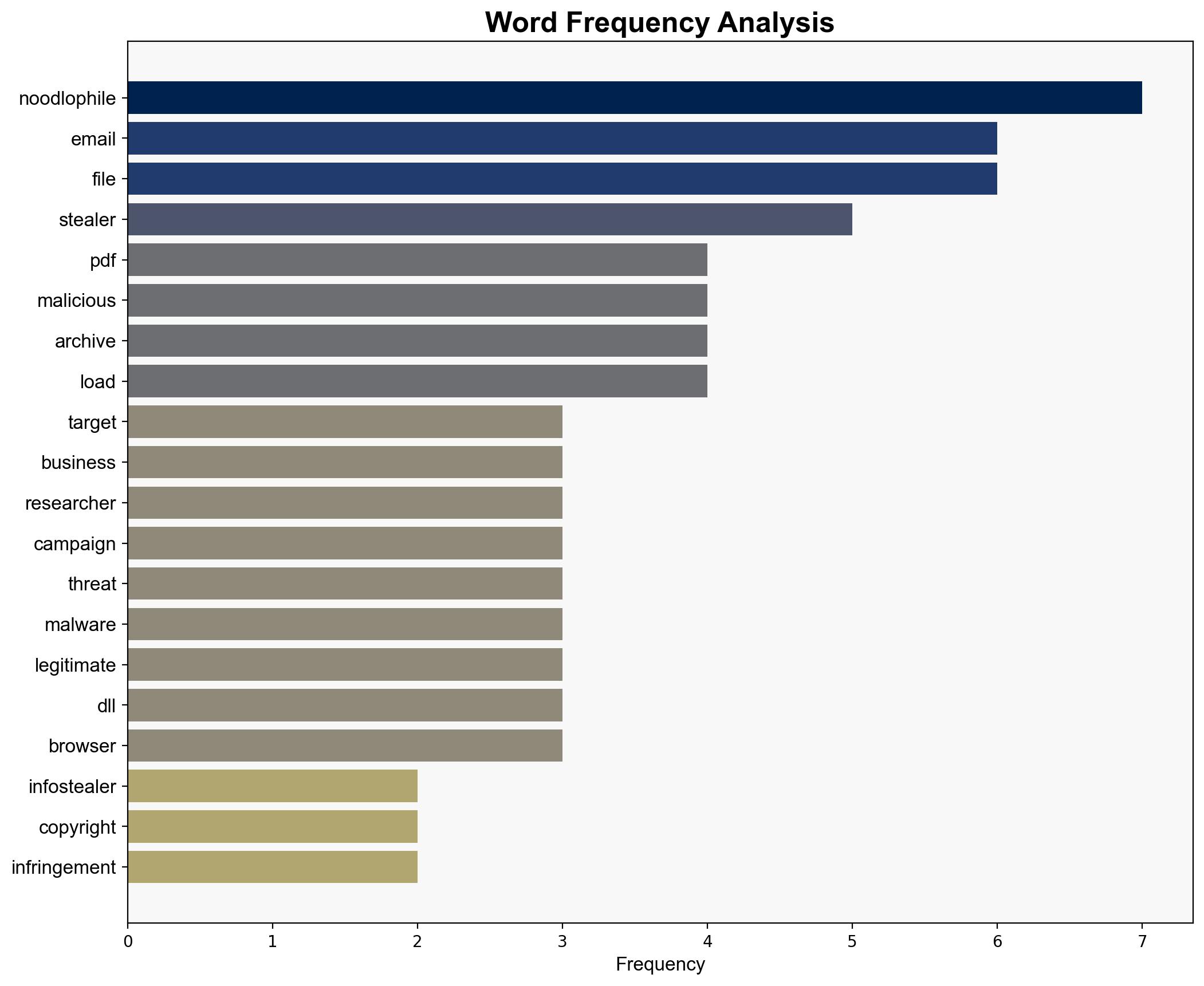
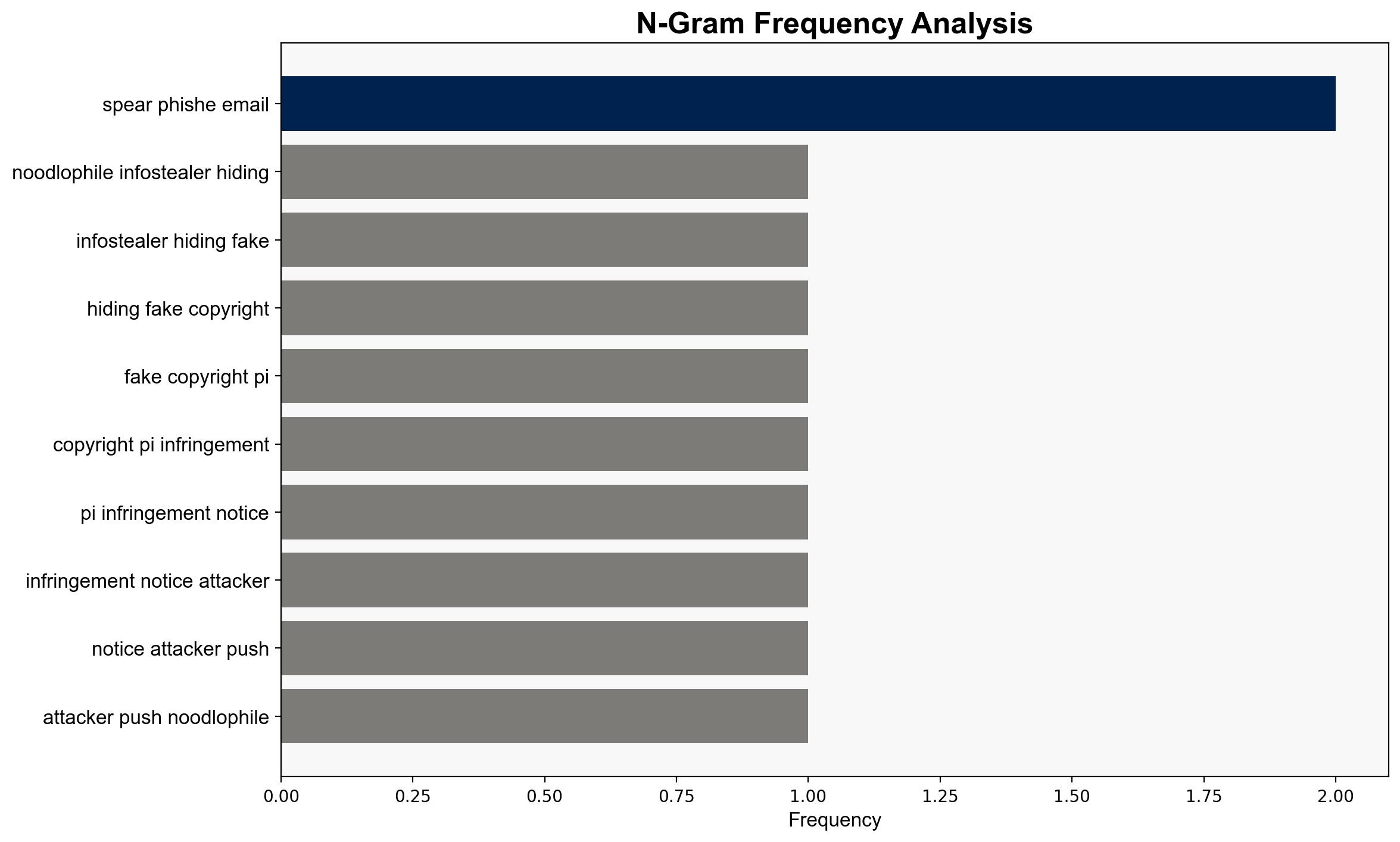
The Noodlophile infostealer campaign employs sophisticated phishing tactics, leveraging fake legal notices to deploy malware. The most supported hypothesis is that this campaign is a coordinated effort by a cybercriminal group targeting businesses across Europe, the Baltic countries, and the APAC region. Confidence level: Moderate. Recommended action: Enhance email filtering systems and user awareness training to recognize and mitigate phishing attempts.
2. Competing Hypotheses
1. **Hypothesis A**: The Noodlophile campaign is orchestrated by a well-organized cybercriminal group with the intent to steal sensitive business data for financial gain.
2. **Hypothesis B**: The campaign is a state-sponsored operation aimed at gathering intelligence and disrupting business operations in targeted regions.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the focus on financial data theft (e.g., login credentials, credit card information) and the use of generative AI tools to enhance phishing tactics, which aligns with typical cybercriminal objectives.
3. Key Assumptions and Red Flags
– **Assumptions**: The attackers are primarily motivated by financial gain (Hypothesis A) or intelligence gathering (Hypothesis B). The use of generative AI tools is assumed to be a deliberate choice to increase the campaign’s success rate.
– **Red Flags**: The use of legitimate-looking legal notices and AI-generated content could indicate a higher level of sophistication than typical cybercriminal operations, suggesting potential state involvement.
– **Blind Spots**: Limited information on the origin of the campaign and the identity of the attackers.
4. Implications and Strategic Risks
The campaign poses significant risks to business operations, potentially leading to data breaches, financial losses, and reputational damage. If state-sponsored, it could escalate geopolitical tensions and lead to retaliatory cyber actions. The evolving capabilities of the malware suggest a potential for increased sophistication and impact in future attacks.
5. Recommendations and Outlook
- Enhance email security measures and conduct regular phishing awareness training for employees.
- Implement advanced threat detection systems to identify and mitigate malware threats.
- Scenario-based projections:
- Best: Increased awareness and improved defenses lead to a significant reduction in successful phishing attacks.
- Worst: The campaign evolves with new capabilities, resulting in widespread data breaches and financial losses.
- Most Likely: Continued targeted attacks with moderate success, prompting ongoing vigilance and adaptation of security measures.
6. Key Individuals and Entities
No specific individuals are identified in the intelligence. The campaign is attributed to an anonymous group using sophisticated phishing tactics.
7. Thematic Tags
national security threats, cybersecurity, cybercrime, phishing, malware, regional focus