North Korean hackers are using advanced AI tools to help them get hired at Western firms – TechRadar
Published on: 2025-04-25
Intelligence Report: North Korean Hackers Utilizing Advanced AI Tools for Employment in Western Firms
1. BLUF (Bottom Line Up Front)
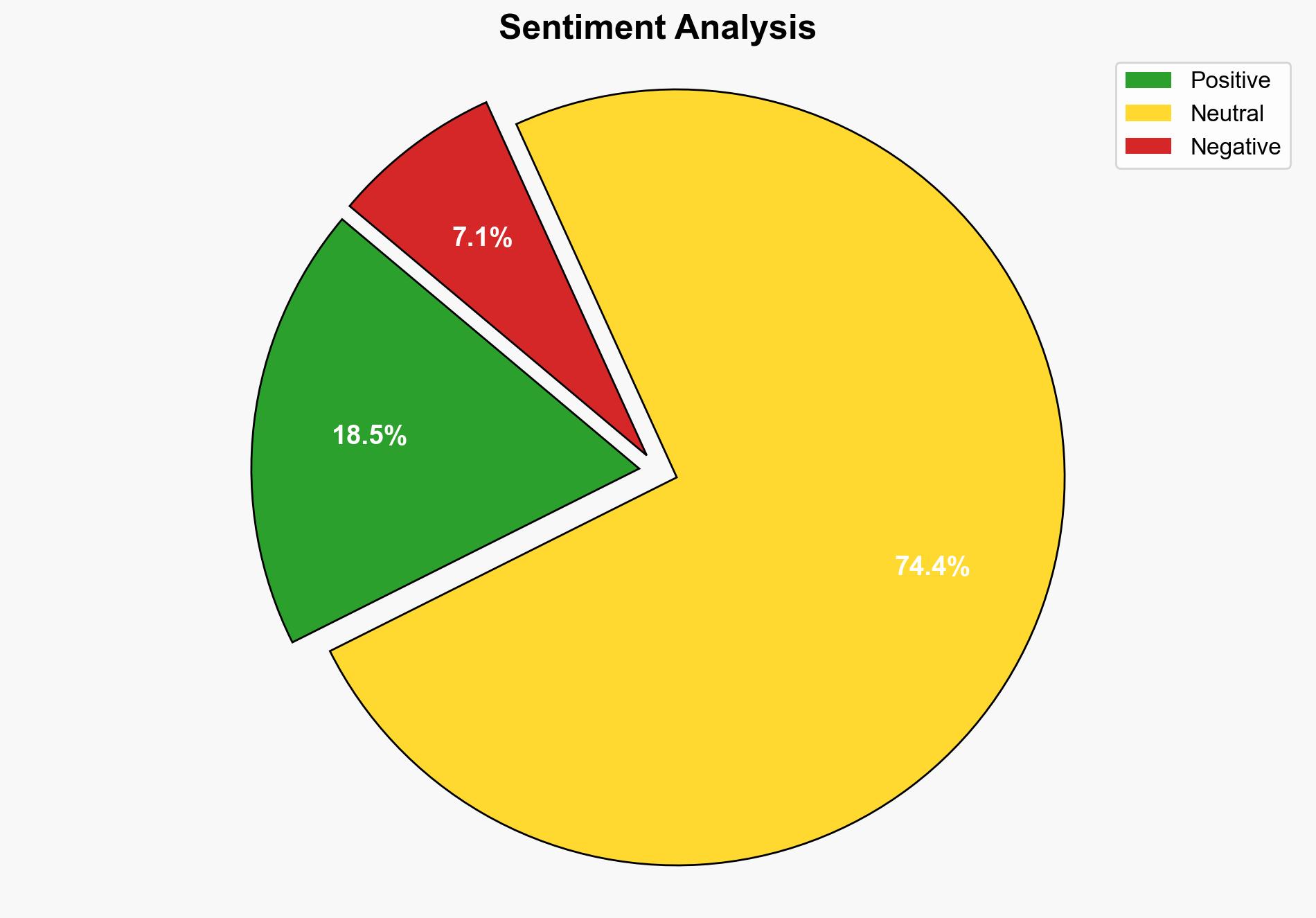
Recent findings indicate that North Korean hackers are leveraging advanced AI tools to secure employment in Western firms, particularly in sectors handling sensitive data such as defense and aerospace. This tactic involves creating convincing personas and conducting sophisticated job application processes. The strategic use of AI in these campaigns poses significant cybersecurity threats to targeted industries, necessitating enhanced vigilance and countermeasures.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The primary hypothesis is that North Korean state-sponsored actors are using AI to infiltrate Western firms for intelligence gathering and economic gain. Alternative hypotheses, such as independent cybercriminals or non-state actors, were considered but found less consistent with the evidence of state-level sophistication and objectives.
SWOT Analysis
Strengths: Advanced AI capabilities, state support, and sophisticated operational planning.
Weaknesses: Potential exposure through digital footprints and operational errors.
Opportunities: Exploiting vulnerabilities in remote work hiring processes.
Threats: Increased international scrutiny and potential countermeasures by targeted firms.
Indicators Development
Key indicators include the use of generative AI in job applications, unusual patterns in recruitment processes, and the presence of North Korean digital signatures in cyber activities.
3. Implications and Strategic Risks
The integration of AI in cyber operations by North Korean actors represents a significant escalation in cyber warfare tactics. This development could lead to increased intellectual property theft, economic espionage, and potential disruptions in critical infrastructure. The cross-domain risks include political tensions and economic destabilization.
4. Recommendations and Outlook
- Enhance cybersecurity protocols in recruitment processes, including AI-driven applicant screening and verification.
- Implement continuous monitoring for unusual activities within sensitive sectors.
- Best Case: Strengthened defenses deter further infiltration attempts.
- Worst Case: Successful infiltration leads to significant data breaches and economic losses.
- Most Likely: Ongoing attempts with varying degrees of success, prompting continuous adaptation of security measures.
5. Key Individuals and Entities
No specific individuals identified. Entities involved include North Korean state-sponsored hacking groups and targeted Western firms in sensitive industries.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)