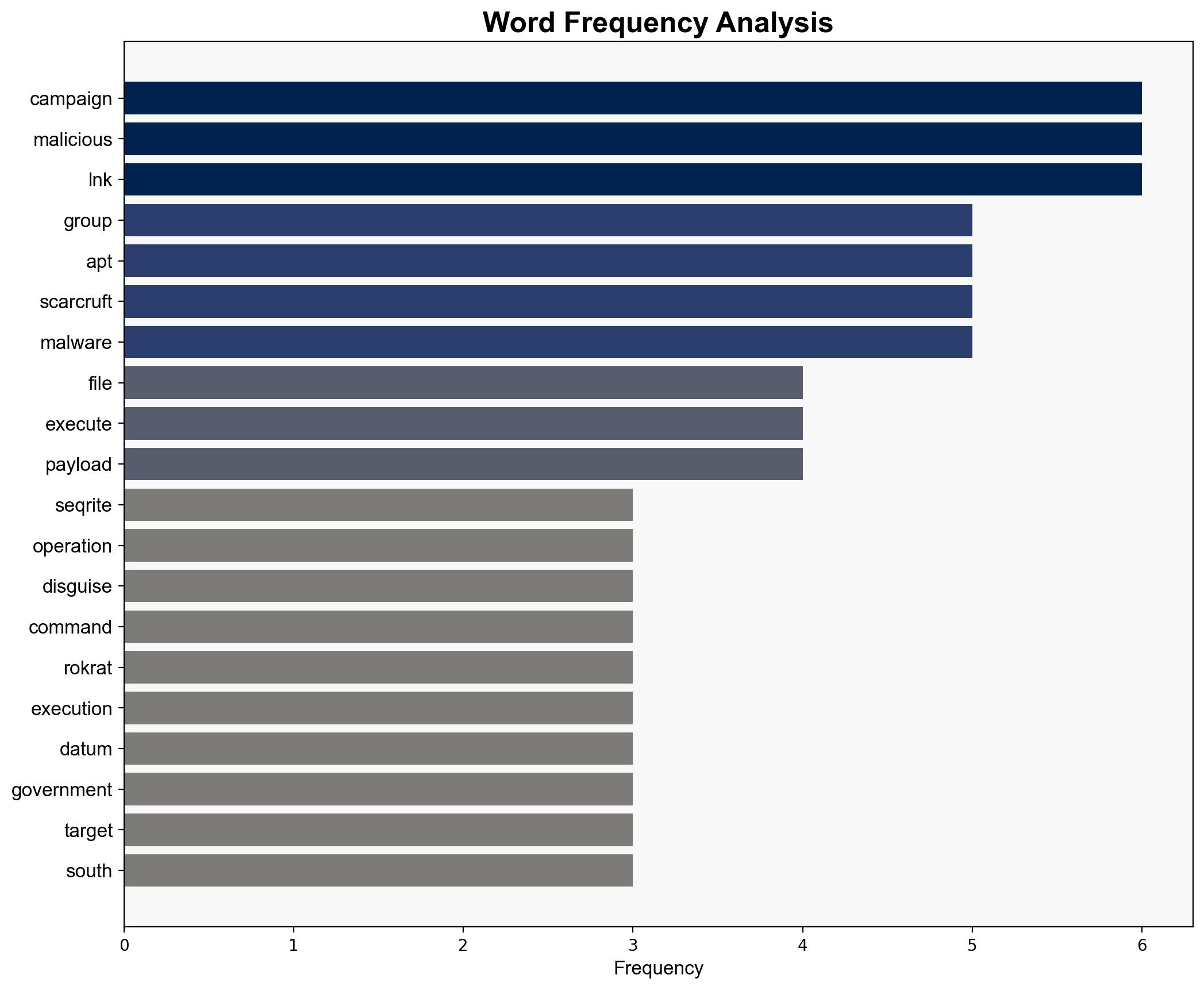
North Koreas APT37 deploys RokRAT in new phishing campaign against academics – Securityaffairs.com
Published on: 2025-09-01
Intelligence Report: North Koreas APT37 deploys RokRAT in new phishing campaign against academics – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that North Korea’s APT37 is executing a sophisticated cyber-espionage campaign targeting South Korean academics and government officials to gather intelligence and maintain long-term espionage capabilities. Confidence level: High. Recommended action: Enhance cybersecurity measures and international collaboration to counteract APT37’s activities.
2. Competing Hypotheses
1. **Hypothesis A**: APT37 is conducting a targeted cyber-espionage campaign against South Korean academics and government officials, primarily for intelligence gathering and long-term strategic advantage.
2. **Hypothesis B**: The campaign is a broader North Korean effort to disrupt South Korean institutions, with espionage as a secondary objective, aiming to destabilize regional security.
Using ACH 2.0, Hypothesis A is better supported due to the specific targeting of academics and government officials, the use of sophisticated malware like RokRAT, and the historical context of North Korean cyber operations focusing on intelligence gathering.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that APT37 has the capability and intent to conduct such operations. The intelligence presumes that the identified malware is solely attributed to North Korean actors.
– **Red Flags**: The reliance on cybersecurity firm reports may introduce bias. The possibility of false flag operations by other actors is not fully explored.
– **Blind Spots**: Limited information on the full scope of targets and potential international involvement or response.
4. Implications and Strategic Risks
The campaign underscores the persistent cyber threat posed by North Korea, with potential risks including:
– Escalation of cyber tensions in the region.
– Compromise of sensitive academic and governmental data.
– Increased vulnerability of South Korean institutions to future attacks.
The campaign could also influence regional geopolitical stability and international cybersecurity policies.
5. Recommendations and Outlook
- Enhance cybersecurity defenses, focusing on phishing detection and response capabilities.
- Strengthen international collaboration for intelligence sharing and coordinated responses.
- Scenario Projections:
- Best: Successful mitigation of the campaign with minimal data loss.
- Worst: Significant data breaches leading to geopolitical tensions.
- Most Likely: Continued cyber-espionage activities with moderate impact on South Korean institutions.
6. Key Individuals and Entities
– Kim Yo-jong (mentioned in the context of rejecting reconciliation efforts).
– APT37 (Ricochet Chollima, ScarCruft, Reaper Group).
– Seqrite Labs (cybersecurity firm reporting on the campaign).
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus