North Korea’s Cybercrime Surge: $2 Billion in Crypto Theft Represents 60% of Global Total in 2025
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: North Korea’s crypto thieving went into overdrive in 2025 with one firm estimating it’s responsible for roughly 60 of the 34 billion stolen in total
1. BLUF (Bottom Line Up Front)
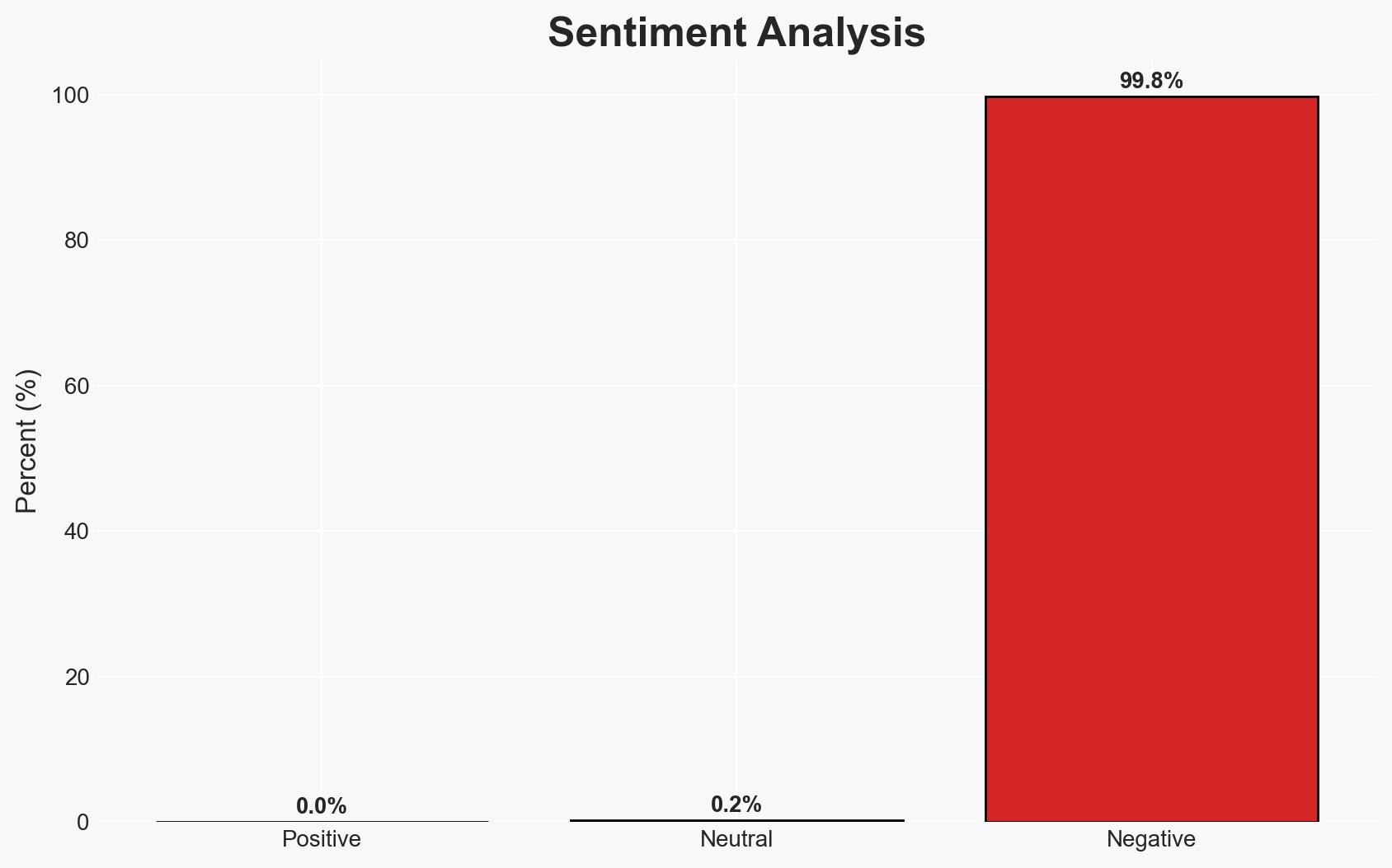
North Korea’s cyber operations have intensified, with the regime responsible for nearly 60% of global cryptocurrency theft in 2025, amounting to approximately $2 billion. The scale and sophistication of these operations, including the Bybit attack, suggest a strategic focus on cryptocurrency theft as a revenue source. This assessment is made with moderate confidence, given the reliance on third-party data and potential for deception in attribution.
2. Competing Hypotheses
- Hypothesis A: North Korea has significantly increased its cyber capabilities and focus on cryptocurrency theft as a primary revenue stream. This is supported by the high value of thefts and the sophisticated laundering techniques observed. However, the exact scale and attribution remain uncertain due to potential underreporting and attribution challenges.
- Hypothesis B: The reported figures may be exaggerated due to biases in data collection and analysis, or North Korea’s involvement may be overstated as part of broader geopolitical narratives. This hypothesis is less supported due to consistent reporting from multiple sources and the detailed nature of the attacks.
- Assessment: Hypothesis A is currently better supported due to the convergence of multiple credible reports and the detailed nature of the operations described. Key indicators that could shift this judgment include new intelligence on North Korea’s cyber capabilities or evidence of alternative actors being responsible for the attacks.
3. Key Assumptions and Red Flags
- Assumptions: North Korea prioritizes cryptocurrency theft for economic gain; the reported figures are accurate; the attribution to North Korea is correct; cryptocurrency theft will continue to be a focus for North Korea.
- Information Gaps: Detailed intelligence on North Korea’s cyber operations infrastructure; verification of the exact amounts stolen and laundered; insights into North Korea’s decision-making processes regarding cyber operations.
- Bias & Deception Risks: Potential bias in data from firms with vested interests in highlighting cyber threats; risk of deception in attributing attacks solely to North Korea without considering other state or non-state actors.
4. Implications and Strategic Risks
The escalation in North Korea’s cyber theft activities could lead to increased tensions and cyber countermeasures from affected nations. This development may also prompt a reevaluation of cryptocurrency security protocols globally.
- Political / Geopolitical: Potential for increased sanctions and diplomatic pressure on North Korea; risk of retaliatory cyber actions.
- Security / Counter-Terrorism: Heightened alert for cyber threats targeting financial systems; potential for spillover into other sectors.
- Cyber / Information Space: Increased focus on cybersecurity measures and blockchain analytics; potential for innovation in cyber defense strategies.
- Economic / Social: Impact on cryptocurrency markets and investor confidence; potential for regulatory changes in cryptocurrency exchanges.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cryptocurrency transactions; increase collaboration with international partners to trace and recover stolen assets.
- Medium-Term Posture (1–12 months): Develop and implement stronger cybersecurity frameworks; foster public-private partnerships to improve threat intelligence sharing.
- Scenario Outlook:
- Best: Improved international cooperation leads to a significant reduction in North Korean cyber theft activities.
- Worst: North Korea escalates cyber operations, targeting critical infrastructure beyond financial systems.
- Most-Likely: Continued focus on cryptocurrency theft with incremental improvements in global cybersecurity measures.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cryptocurrency theft, North Korea, cybercrime, economic sanctions, blockchain, international cooperation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us