North Koreas ScarCruft Targets Academics With RokRAT Malware – HackRead
Published on: 2025-09-01
Intelligence Report: North Koreas ScarCruft Targets Academics With RokRAT Malware – HackRead
1. BLUF (Bottom Line Up Front)
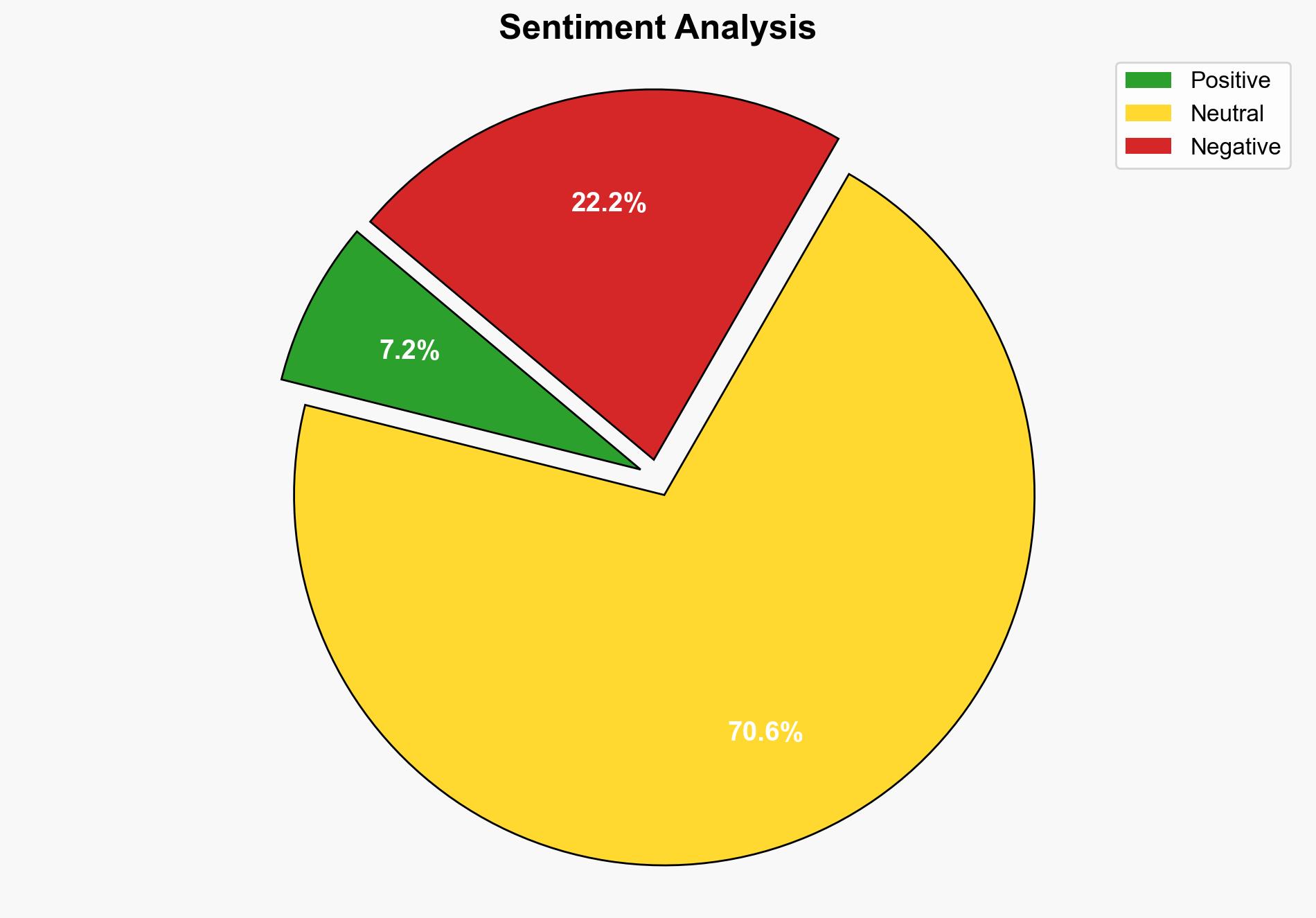
The most supported hypothesis is that North Korea’s ScarCruft group is actively targeting South Korean academics and government officials with RokRAT malware as part of a broader cyber espionage campaign. This is likely a strategic move to gather intelligence and exert influence over South Korean policy and academia. Confidence in this assessment is moderate due to the evolving nature of cyber tactics and potential for misattribution. Recommended action includes enhancing cybersecurity defenses and increasing intelligence sharing among potential target sectors.
2. Competing Hypotheses
1. **Hypothesis A**: ScarCruft is primarily targeting South Korean academics and government officials with RokRAT malware to gather intelligence and influence South Korean policy decisions.
2. **Hypothesis B**: The campaign is a broader initiative by North Korea to destabilize regional security and gather intelligence from multiple countries, using South Korea as a primary but not exclusive target.
Using the Analysis of Competing Hypotheses (ACH) method, Hypothesis A is better supported due to the specific targeting of South Korean entities and the use of culturally relevant decoys, such as documents related to North Korean politics.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the ScarCruft group operates under the directive of North Korean state interests. The attribution of the cyber activities to North Korea relies on technical indicators and historical patterns.
– **Red Flags**: The potential for false flag operations or misattribution exists, as cyber activities can be obfuscated. The evolving tactics of ScarCruft suggest a need for continuous monitoring.
– **Blind Spots**: Limited visibility into the full scope of ScarCruft’s operations and potential connections with other threat actors.
4. Implications and Strategic Risks
The campaign poses significant risks to South Korean national security by potentially compromising sensitive information and influencing policy decisions. It may also strain diplomatic relations in the region and lead to increased tensions. The use of cloud services for data exfiltration highlights vulnerabilities in commonly used platforms, posing broader cybersecurity risks.
5. Recommendations and Outlook
- Enhance cybersecurity measures in academic and government institutions, focusing on phishing awareness and endpoint security.
- Increase intelligence sharing and collaboration between South Korea and allied nations to identify and mitigate threats.
- Scenario Projections:
- **Best Case**: Improved defenses lead to reduced effectiveness of ScarCruft’s campaigns.
- **Worst Case**: Successful data breaches result in significant policy manipulation or regional destabilization.
- **Most Likely**: Continued cyber espionage activities with periodic successes and failures.
6. Key Individuals and Entities
– Kim Yo-jong: Mentioned in decoy documents, indicating potential political motivations behind the campaign.
– ScarCruft: The primary threat actor group involved in the campaign.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus