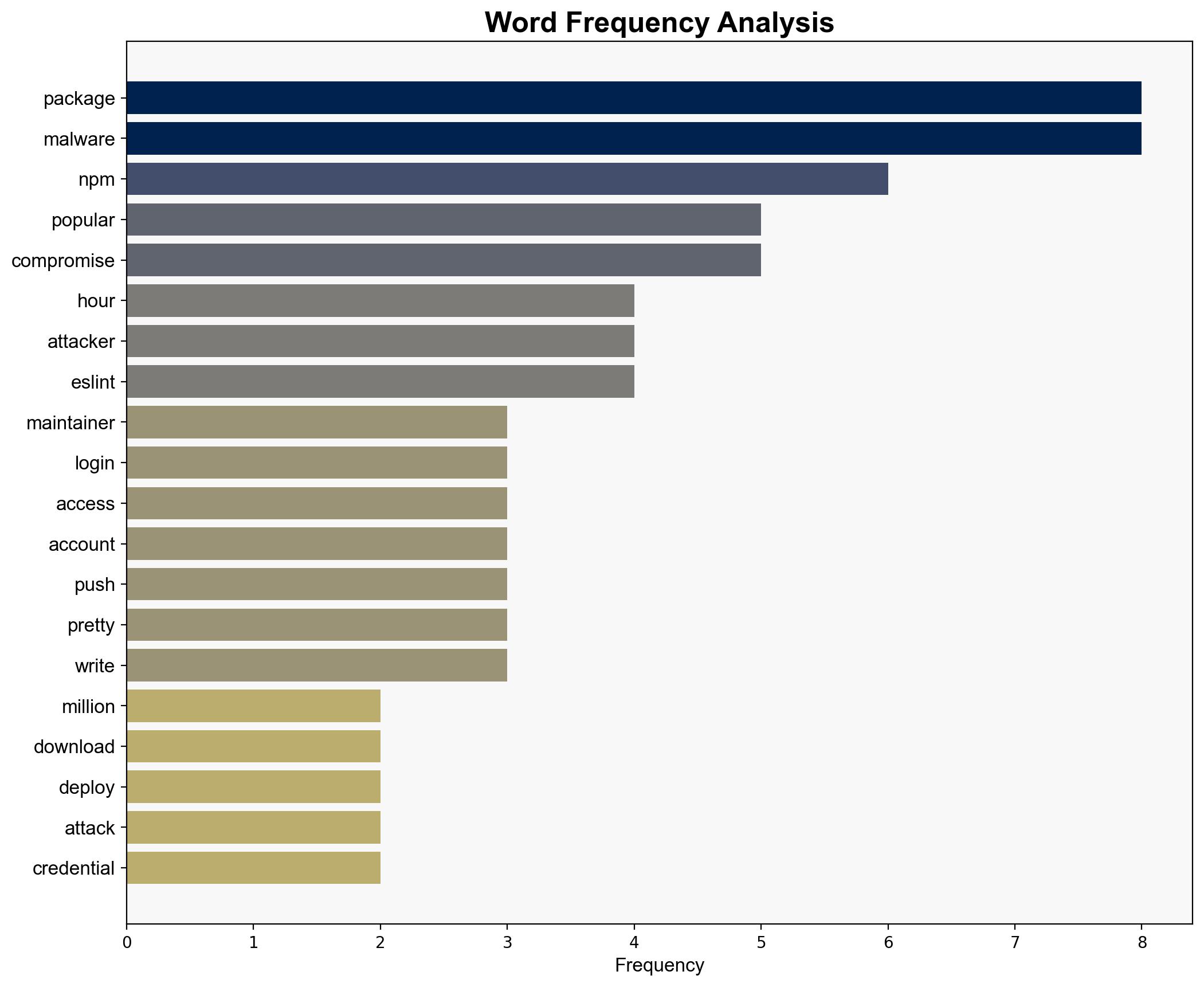
Npm package with millions of downloads is at risk from malware hijacking – TechRadar
Published on: 2025-07-24
Intelligence Report: Npm package with millions of downloads is at risk from malware hijacking – TechRadar
1. BLUF (Bottom Line Up Front)
The npm package ecosystem is vulnerable to supply chain attacks, as demonstrated by the recent compromise of a popular package. The most supported hypothesis is that the attack was a targeted effort exploiting weak security practices among maintainers. Confidence level: Moderate. Recommended action: Enhance security protocols and awareness among npm maintainers to prevent credential phishing and unauthorized access.
2. Competing Hypotheses
Hypothesis 1: The attack was a targeted effort by cybercriminals exploiting known vulnerabilities in npm’s security practices, specifically targeting maintainers through phishing to gain access and deploy malware.
Hypothesis 2: The compromise was an opportunistic attack, not specifically targeting npm but rather exploiting a general vulnerability in open-source software ecosystems, with the attackers taking advantage of any available entry point.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the specific targeting of a maintainer through a phishing attack, suggesting a deliberate and informed approach.
3. Key Assumptions and Red Flags
Assumptions:
– Maintainers are the primary vulnerability point due to inadequate security measures.
– Attackers have the capability to exploit phishing attacks effectively.
Red Flags:
– Lack of detailed information on how the phishing email bypassed security measures.
– No evidence of similar attacks on other npm packages, which could indicate a broader vulnerability.
4. Implications and Strategic Risks
The attack highlights the fragility of the software supply chain, with potential cascading effects on any system using the compromised package. The economic impact could be significant if similar attacks proliferate, affecting businesses relying on npm packages. Geopolitically, such vulnerabilities could be exploited by state actors to disrupt critical infrastructure. Psychologically, trust in open-source software could diminish, leading to increased scrutiny and potential regulatory actions.
5. Recommendations and Outlook
- Implement multi-factor authentication for npm maintainers to prevent unauthorized access.
- Conduct regular security training for developers to recognize and avoid phishing attempts.
- Scenario Projections:
- Best Case: Rapid adoption of enhanced security measures reduces future vulnerabilities.
- Worst Case: A widespread attack on npm packages causes significant disruption and loss.
- Most Likely: Incremental improvements in security practices reduce but do not eliminate risks.
6. Key Individuals and Entities
– Jounqin: Maintainer of the compromised package.
– John Harband: Reported as a compromised maintainer.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus