NSA Joins CISA and Others to Release Guidance on Mitigating Malicious Activity from Bulletproof Hosting Provider Infrastructure – Globalsecurity.org
Published on: 2025-11-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
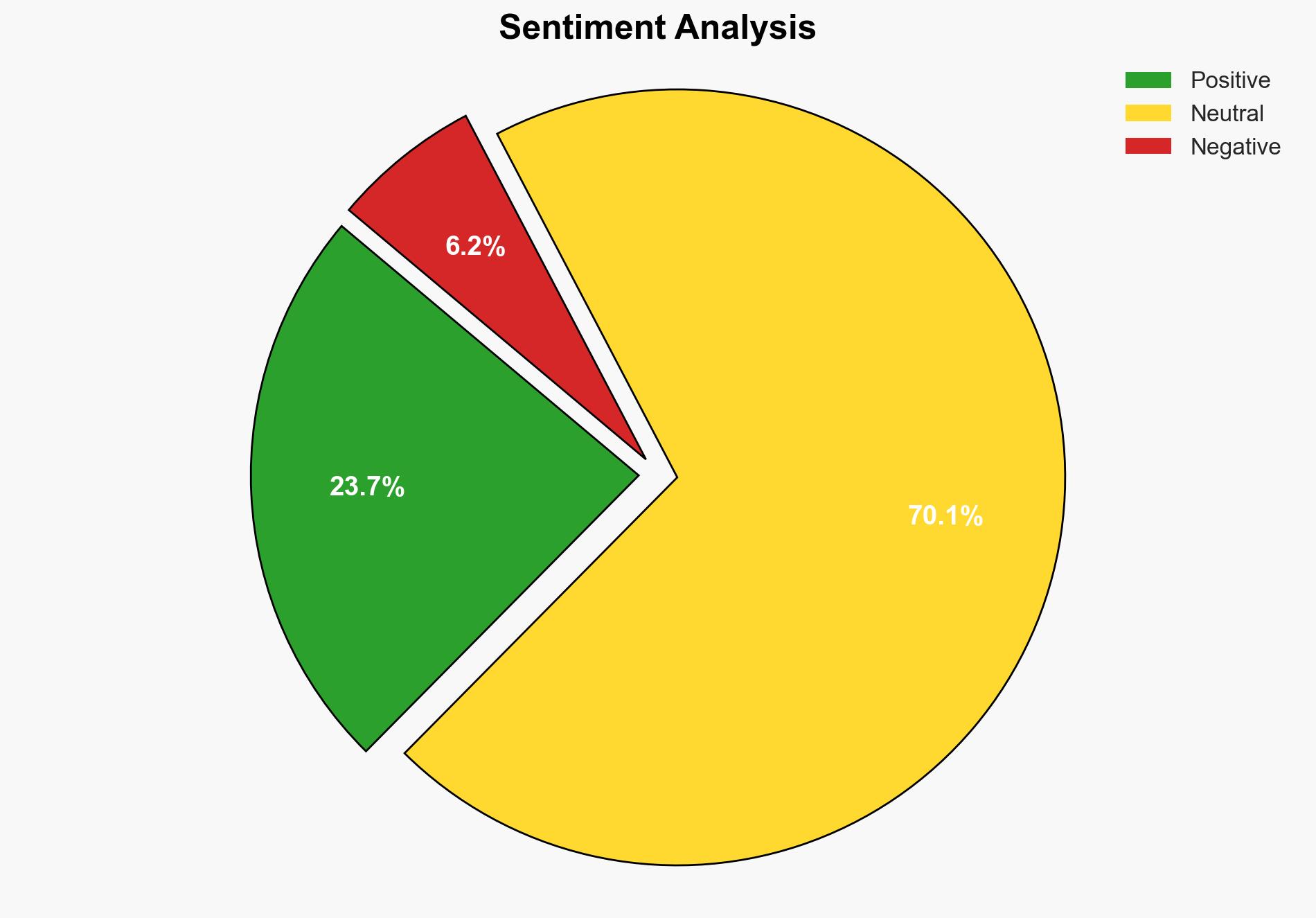
The strategic judgment indicates a high confidence level that the guidance released by NSA and CISA is a proactive measure to mitigate the increasing threat posed by Bulletproof Hosting Providers (BPH) to critical infrastructure and high-value targets. The most supported hypothesis is that this guidance aims to disrupt cybercriminal activities by reducing the utility of BPH infrastructure. Recommended actions include the adoption of the outlined mitigation strategies by ISPs and network defenders to block malicious traffic while minimizing impacts on legitimate infrastructure.
2. Competing Hypotheses
Hypothesis 1: The NSA and CISA guidance is primarily a defensive measure to protect critical infrastructure from cybercriminal activities facilitated by BPH providers.
Hypothesis 2: The guidance serves as a deterrent to BPH providers and cybercriminals, signaling increased international cooperation and readiness to impose legal and operational consequences.
The first hypothesis is more likely as it aligns with the immediate need to protect critical infrastructure and high-value targets, evidenced by the involvement of multiple international cybersecurity agencies. The second hypothesis, while plausible, is secondary as the guidance focuses on practical mitigation strategies rather than direct deterrence.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that BPH providers knowingly facilitate cybercriminal activities and that ISPs and network defenders have the capability and willingness to implement the recommended strategies.
Red Flags: Potential bias in assuming all BPH providers are complicit; lack of clarity on enforcement mechanisms for ISPs; potential for legitimate services to be inadvertently affected.
Deception Indicators: None identified in the guidance release, but the possibility of BPH providers adapting to circumvent new defenses should be monitored.
4. Implications and Strategic Risks
The guidance could lead to a reduction in cybercriminal activities targeting critical infrastructure, but also risks pushing these activities to more covert or sophisticated methods. There is a potential for geopolitical tensions if BPH providers are linked to state actors. Economically, ISPs may incur costs to implement new defenses, which could be passed on to consumers. Informationally, increased public awareness of BPH threats may lead to heightened vigilance but also potential panic if mismanaged.
5. Recommendations and Outlook
- ISPs and network defenders should promptly adopt the recommended mitigation strategies.
- Engage in international collaboration to monitor and adapt to evolving BPH tactics.
- Develop public communication strategies to manage perceptions and prevent misinformation.
- Best-case scenario: Successful disruption of BPH-facilitated activities, leading to a significant decrease in cyber threats.
- Worst-case scenario: BPH providers adapt quickly, leading to more sophisticated and harder-to-detect threats.
- Most-likely scenario: Initial disruption followed by a period of adaptation by both defenders and attackers, requiring ongoing vigilance and strategy updates.
6. Key Individuals and Entities
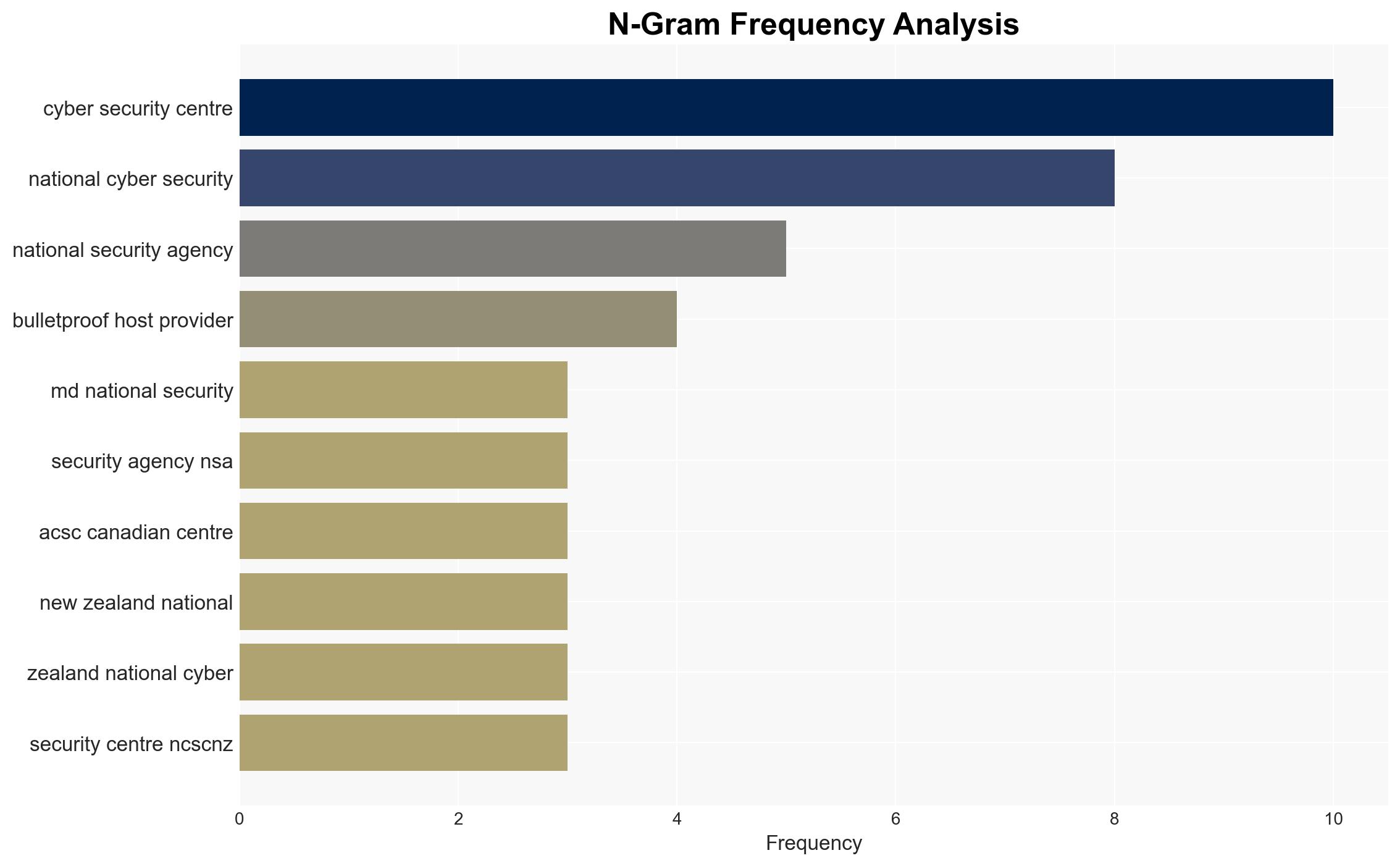
National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), Department of Defense Cyber Crime Center, Federal Bureau of Investigation, Australian Signals Directorate’s Australian Cyber Security Centre, Canadian Centre for Cyber Security, Netherlands National Cyber Security Centre, New Zealand National Cyber Security Centre, United Kingdom National Cyber Security Centre.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us