Obsidian Security Launches Comprehensive Suite to Address Growing SaaS Integration Security Threats
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Obsidian Security targets rising tide of SaaS integration threats
1. BLUF (Bottom Line Up Front)
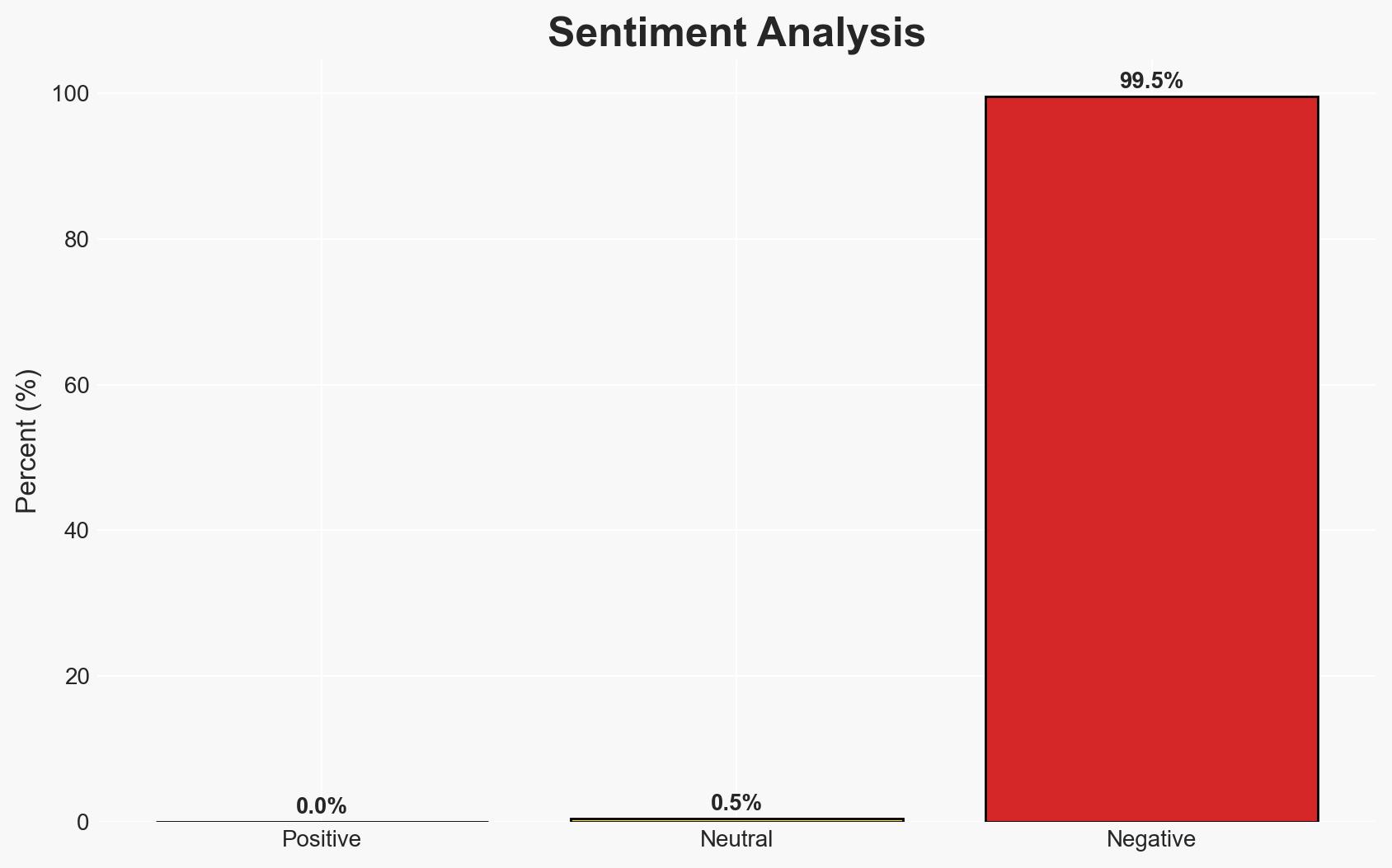
Obsidian Security has launched a suite of capabilities to address vulnerabilities in SaaS integration, a growing target for cyber threats. This development is critical for businesses reliant on interconnected SaaS environments, as it aims to mitigate risks associated with unauthorized integrations and AI agents. Moderate confidence in the assessment due to limited data on the efficacy of the new capabilities.
2. Competing Hypotheses
- Hypothesis A: Obsidian Security’s new capabilities will significantly reduce the risk of SaaS integration breaches by providing comprehensive visibility and real-time detection. This is supported by the company’s claims of using a knowledge graph and real-time anomaly detection. However, the effectiveness of these tools in diverse operational environments remains uncertain.
- Hypothesis B: Despite Obsidian’s new capabilities, SaaS integration threats will continue to escalate due to the rapid adoption of AI agents and the complexity of managing shadow integrations. This is supported by the ongoing increase in SaaS adoption and the inherent challenges in securing autonomous AI interactions.
- Assessment: Hypothesis B is currently better supported due to the broader trend of increasing SaaS and AI integration, which may outpace the security measures being implemented. Indicators such as the frequency of breaches and the adoption rate of Obsidian’s solutions could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: SaaS integration threats will continue to grow; Obsidian’s capabilities are unique and effective; businesses will adopt these solutions.
- Information Gaps: Detailed performance metrics of Obsidian’s new capabilities; broader industry adoption rates; specific threat actor tactics targeting SaaS integrations.
- Bias & Deception Risks: Potential over-reliance on vendor-provided data; confirmation bias in evaluating the effectiveness of new technologies; possible exaggeration of threat levels to drive product adoption.
4. Implications and Strategic Risks
The introduction of Obsidian’s capabilities could influence the cybersecurity landscape by setting new standards for SaaS integration security. However, the rapid evolution of AI and integration technologies could outpace these measures, leading to new vulnerabilities.
- Political / Geopolitical: Increased focus on cybersecurity could lead to regulatory changes affecting SaaS providers globally.
- Security / Counter-Terrorism: Enhanced security measures may reduce the operational capabilities of threat actors exploiting SaaS vulnerabilities.
- Cyber / Information Space: Potential shift in cyber threat tactics towards exploiting AI-driven integrations and shadow IT.
- Economic / Social: Improved security could bolster business confidence in SaaS adoption, but failure to secure integrations may lead to significant economic disruptions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor the adoption and performance of Obsidian’s solutions; assess the integration security posture of critical SaaS environments.
- Medium-Term Posture (1–12 months): Develop partnerships with SaaS providers to enhance integration security; invest in AI and machine learning capabilities for threat detection.
- Scenario Outlook: Best: Widespread adoption of effective security measures reduces integration threats. Worst: Rapid AI integration outpaces security, leading to major breaches. Most-Likely: Incremental improvements in security with ongoing challenges from evolving threats.
6. Key Individuals and Entities
- Khanh Tran, Chief Product Officer at Obsidian Security
- Hasan Imam, Chief Executive at Obsidian Security
- Obsidian Security Inc.
- Salesloft Inc.
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, SaaS integration, AI threats, cloud security, cyber risk management, shadow IT, OAuth vulnerabilities
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us