Odido Reports Data Breach Affecting 6.2 Million Customers, Compromising Personal Information
Published on: 2026-02-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Odido confirms massive breach 62 Million customers impacted
1. BLUF (Bottom Line Up Front)
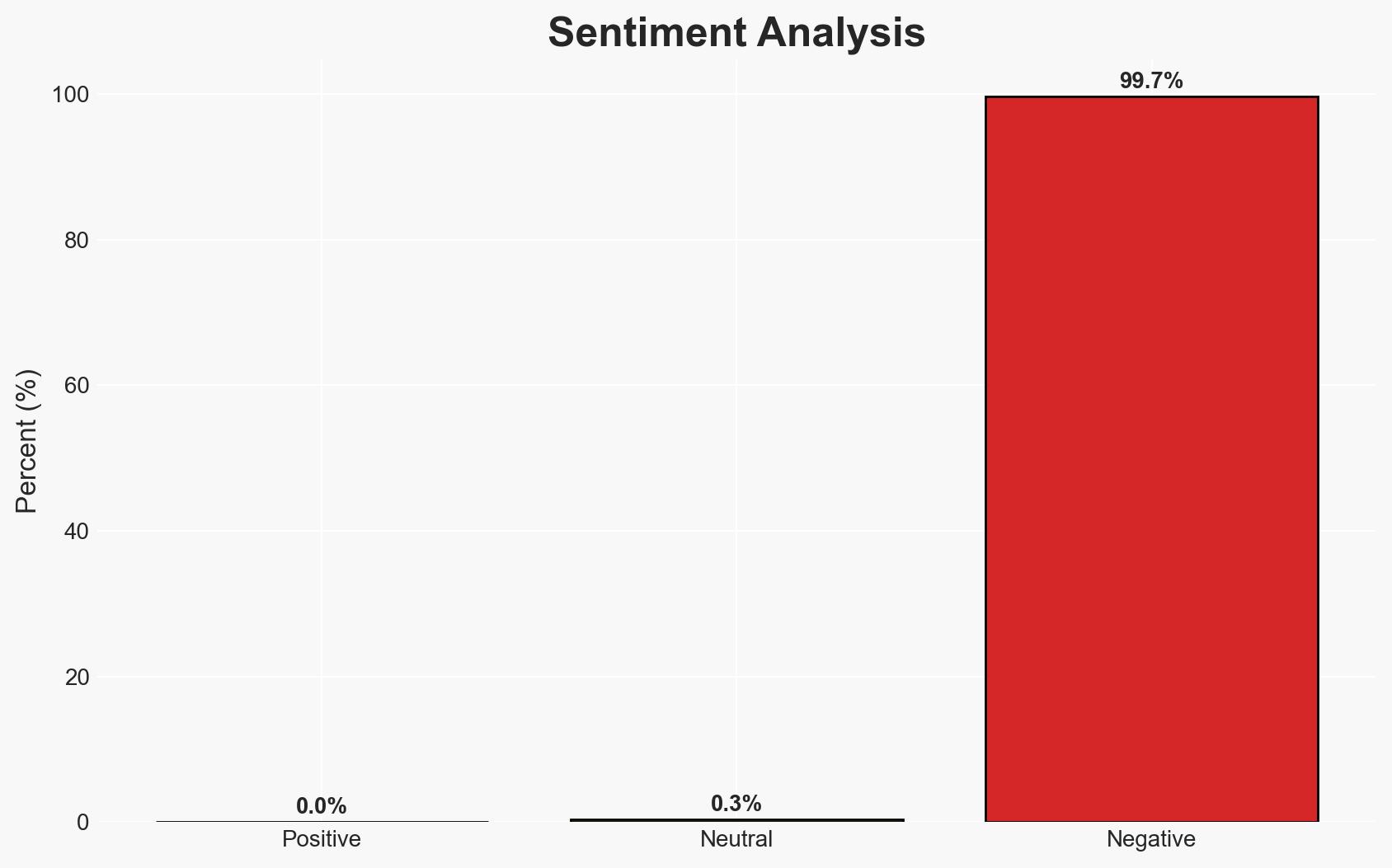
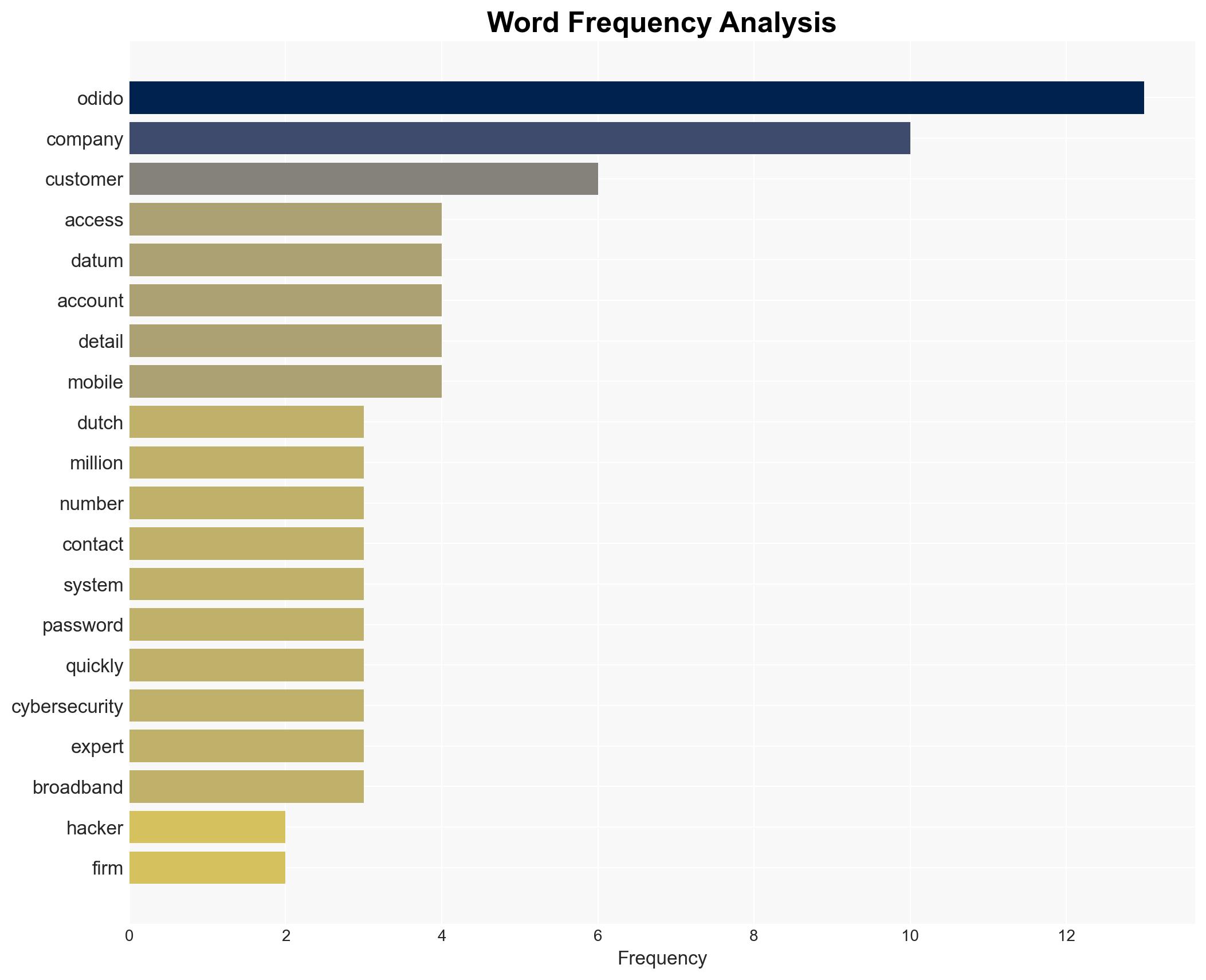
Odido, a major Dutch telecom firm, experienced a significant data breach affecting 6.2 million accounts, exposing sensitive customer information. The breach did not compromise passwords or billing data, but personal identifiers were accessed. The most likely hypothesis is that the breach resulted from a targeted cyberattack exploiting vulnerabilities in customer contact systems. Confidence in this assessment is moderate due to limited technical details.
2. Competing Hypotheses
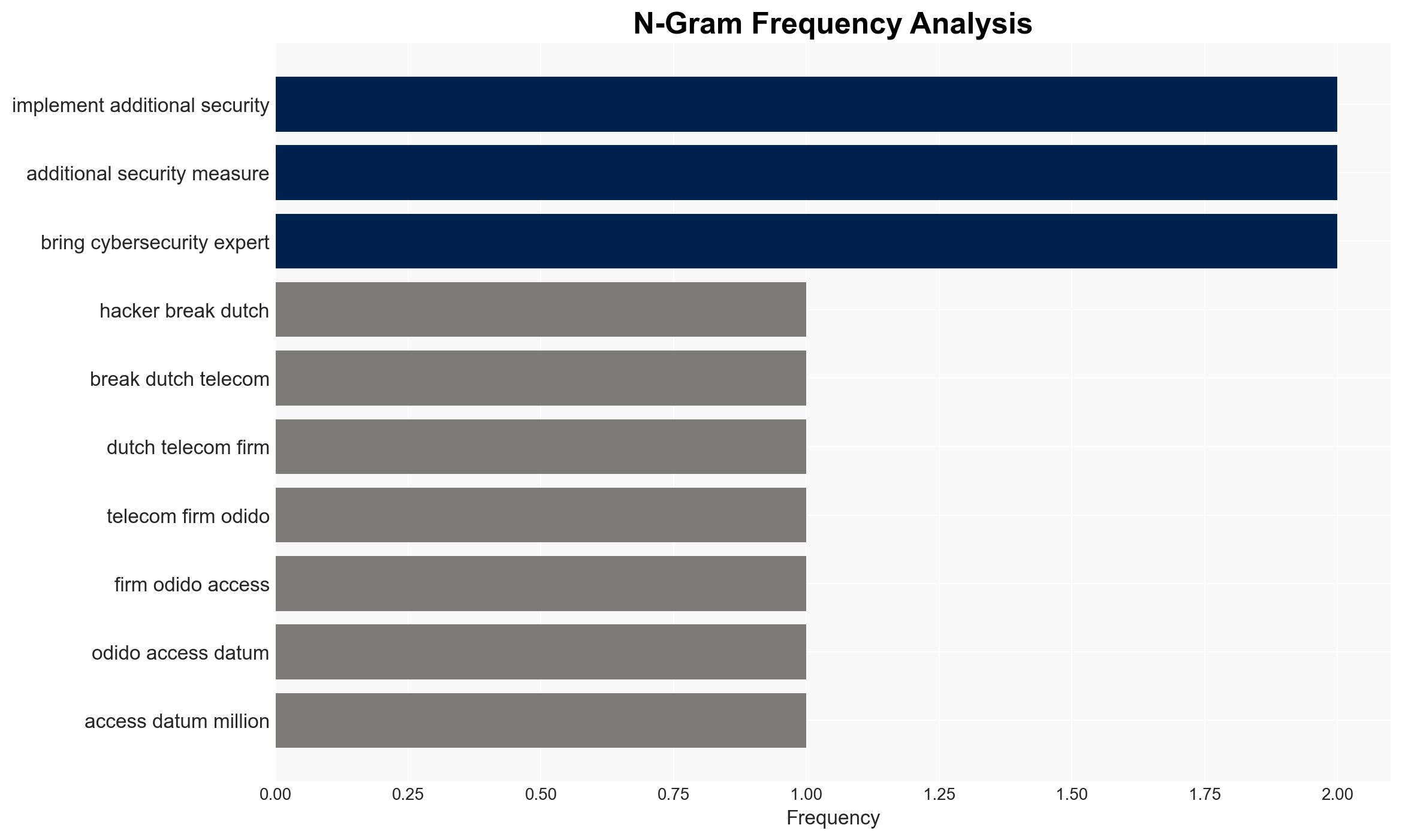
- Hypothesis A: The breach was a targeted cyberattack exploiting specific vulnerabilities in Odido’s customer contact systems. This is supported by the nature of the data accessed and the rapid response to terminate unauthorized access. However, technical details of the breach are lacking, creating uncertainty about the attack vector.
- Hypothesis B: The breach was an opportunistic attack by cybercriminals exploiting general security weaknesses. This is less supported due to the specificity of the data accessed and the targeted nature of the attack, which suggests prior knowledge or reconnaissance.
- Assessment: Hypothesis A is currently better supported due to the targeted nature of the data accessed and the quick containment efforts. Indicators such as the discovery of specific vulnerabilities or insider involvement could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The breach was limited to the customer contact system; Odido’s response measures are effective; external cybersecurity experts have accurately assessed the threat.
- Information Gaps: Detailed technical information about the attack vector and methods used; identity and motives of the attackers; effectiveness of the new security measures.
- Bias & Deception Risks: Potential bias in Odido’s public statements to minimize reputational damage; lack of independent verification of breach details; possible manipulation by attackers to obscure their methods.
4. Implications and Strategic Risks
The breach could lead to increased scrutiny of Odido’s cybersecurity practices and impact customer trust. It may also encourage similar attacks on other telecom operators.
- Political / Geopolitical: Potential regulatory scrutiny and pressure from the Dutch government to enhance cybersecurity standards across the telecom sector.
- Security / Counter-Terrorism: Increased risk of identity theft and fraud, potentially funding criminal or terrorist activities.
- Cyber / Information Space: Enhanced cyber threat landscape with potential for further attacks exploiting similar vulnerabilities.
- Economic / Social: Possible financial losses for Odido and affected customers, leading to decreased consumer confidence and market share.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit; enhance monitoring for suspicious activities; communicate transparently with affected customers.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms; invest in advanced threat detection systems; develop a robust incident response plan.
- Scenario Outlook:
- Best: Successful mitigation with no further breaches; restored customer trust.
- Worst: Additional breaches occur; significant financial and reputational damage.
- Most-Likely: Gradual recovery with increased regulatory oversight and improved security measures.
6. Key Individuals and Entities
- Odido
- Ben (Odido subsidiary)
- Apax Partners
- Warburg Pincus
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, telecommunications, identity theft, regulatory compliance, customer data protection, cyber threat landscape
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us