One of the biggest security threats to Apple systems just got a major upgrade – here’s what we know – TechRadar
Published on: 2025-07-08
Intelligence Report: One of the biggest security threats to Apple systems just got a major upgrade – here’s what we know – TechRadar
1. BLUF (Bottom Line Up Front)
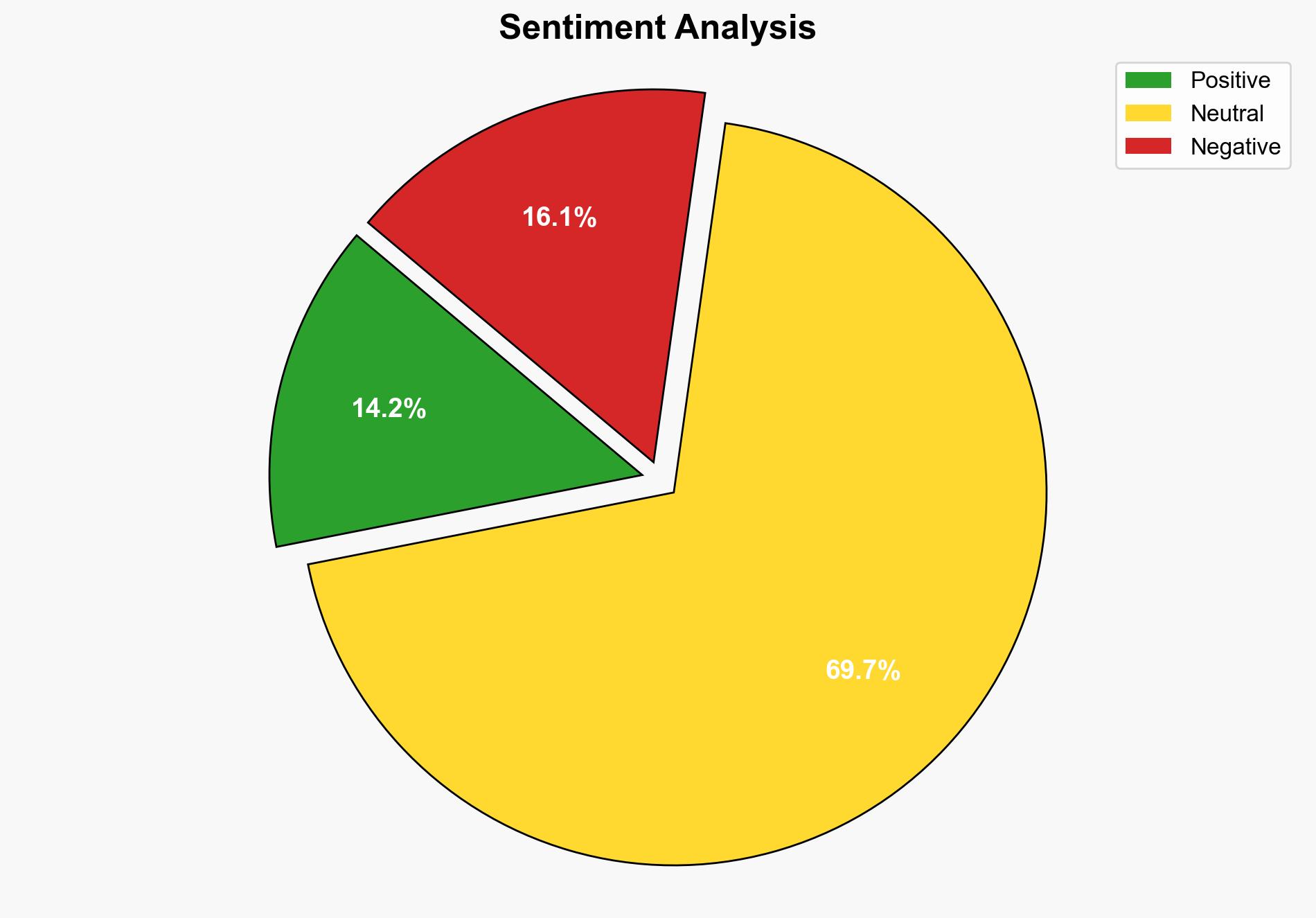
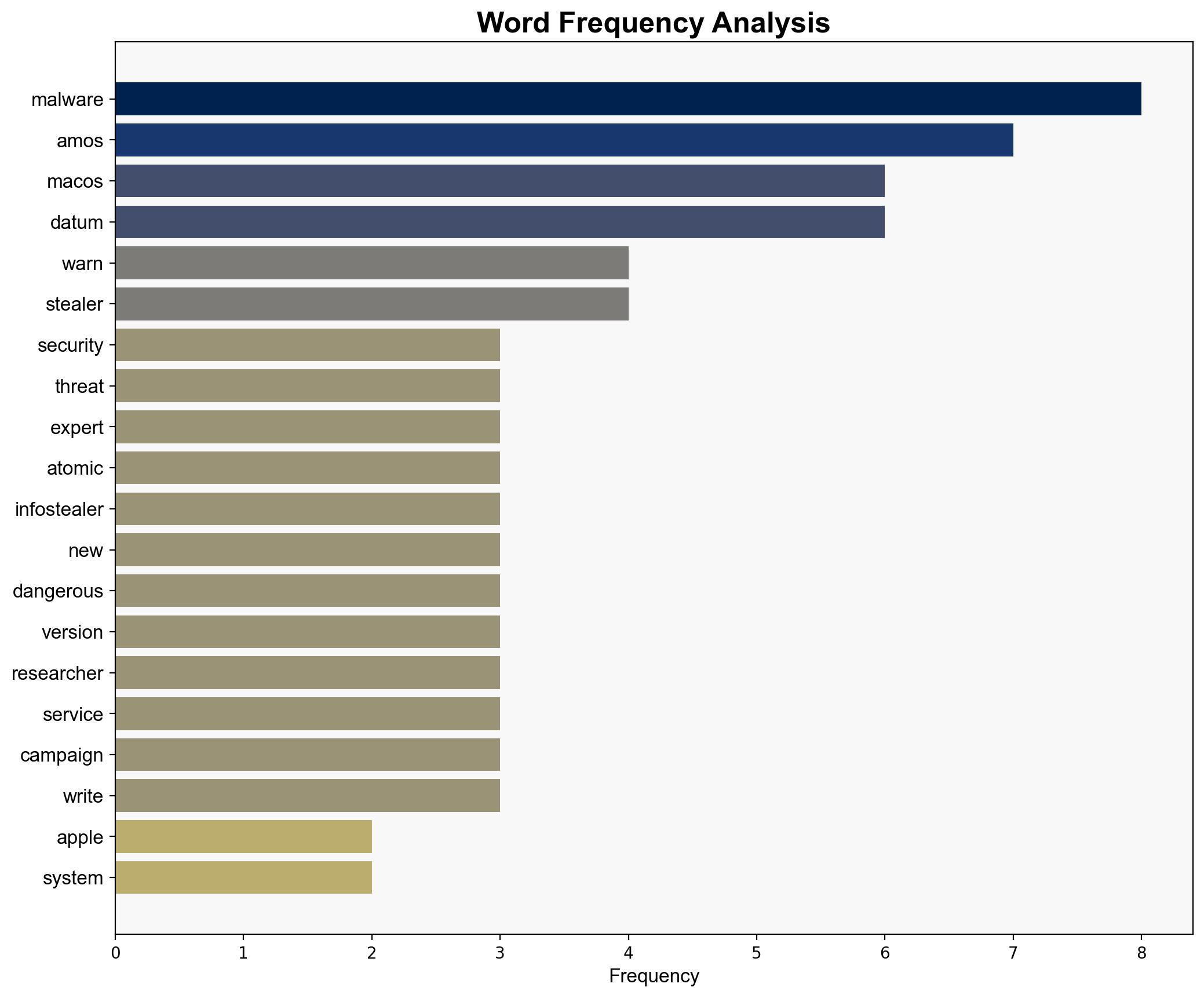
The Atomic Stealer malware, a significant threat to Apple’s macOS ecosystem, has received a major upgrade, enhancing its persistence and backdoor capabilities. This development poses an increased risk to global cybersecurity, particularly for Apple users. Immediate attention and action are required to mitigate potential widespread data breaches and system compromises.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The upgraded Atomic Stealer now includes a backdoor persistence mechanism, allowing it to survive system reboots and maintain unauthorized access. This advancement suggests a strategic move by cyber adversaries to enhance malware resilience and infiltration capabilities.
Indicators Development
Key indicators include unusual system behavior, unauthorized access attempts, and anomalies in data transmission. Monitoring these indicators can facilitate early detection of the malware.
Bayesian Scenario Modeling
The probabilistic assessment indicates a high likelihood of increased attack vectors targeting macOS users, with potential pathways including phishing campaigns and malicious software distribution via fake applications.
3. Implications and Strategic Risks
The enhanced capabilities of Atomic Stealer could lead to significant data breaches, affecting personal and corporate data integrity. The malware’s ability to bypass macOS security features increases the risk of widespread exploitation, potentially impacting economic stability and national security.
4. Recommendations and Outlook
- Implement robust endpoint protection solutions and regularly update security protocols to counteract the new malware variant.
- Conduct user awareness campaigns to educate on identifying phishing attempts and suspicious software.
- Scenario-based projections suggest that without intervention, the malware could proliferate rapidly, leading to widespread data theft (worst case). Conversely, enhanced security measures could contain the threat (best case).
5. Key Individuals and Entities
Alia Gnjxa (independent researcher), Ryan Chenkie (software developer)
6. Thematic Tags
national security threats, cybersecurity, macOS vulnerabilities, malware persistence, data protection