Ongoing Exploitation of WinRAR Vulnerability by Diverse Cyber Threat Actors
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: WinRAR path traversal flaw still exploited by numerous hackers
1. BLUF (Bottom Line Up Front)
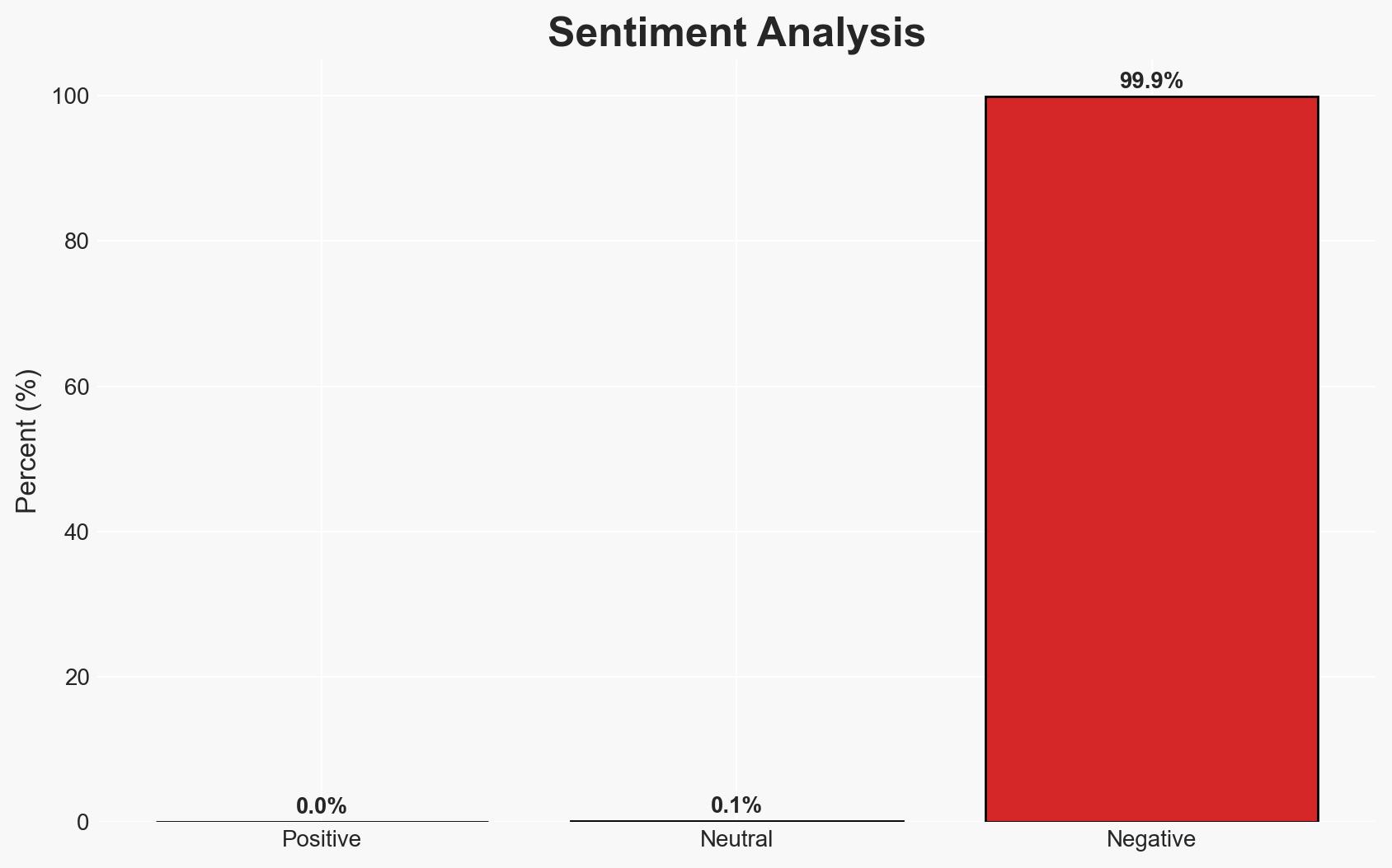
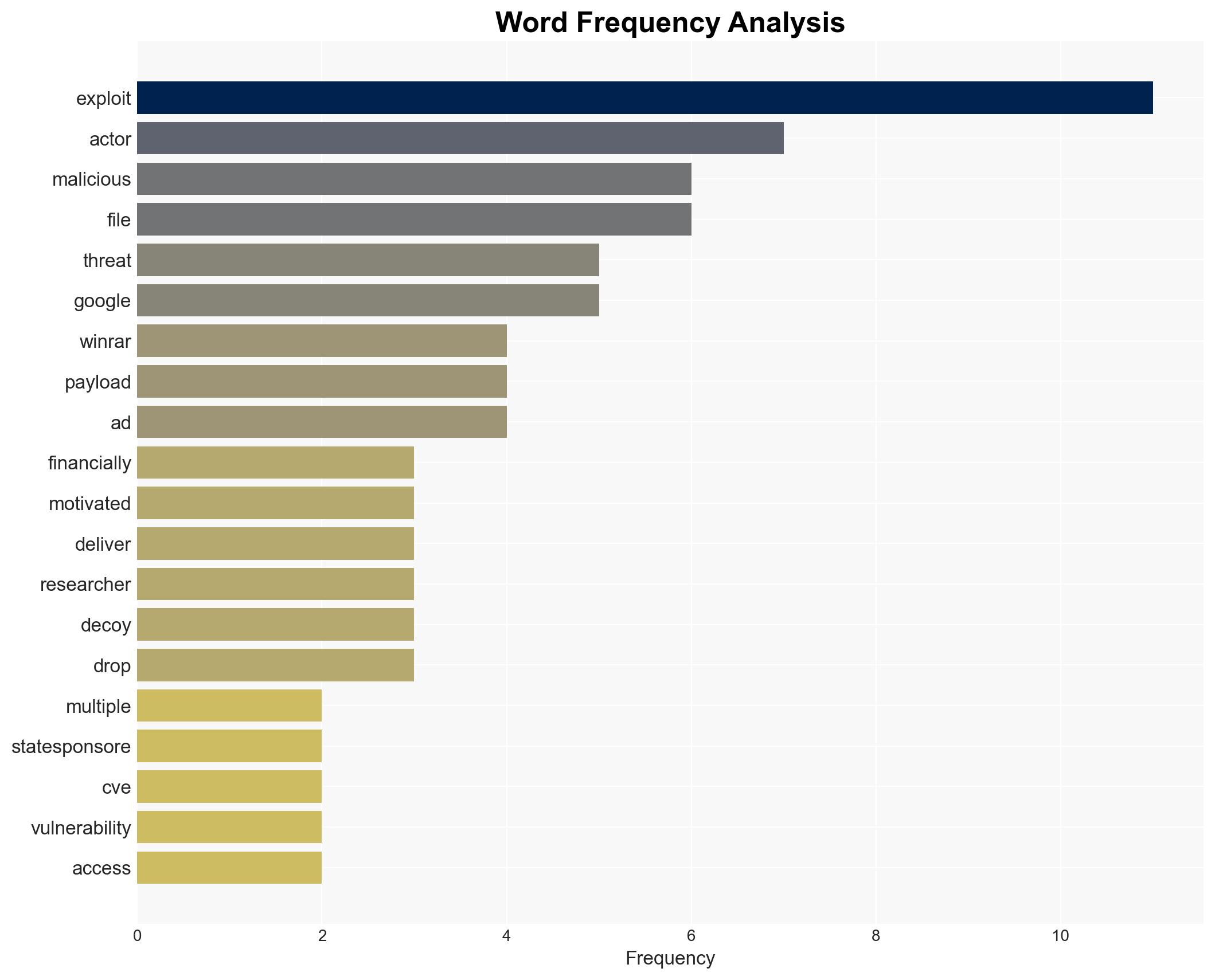
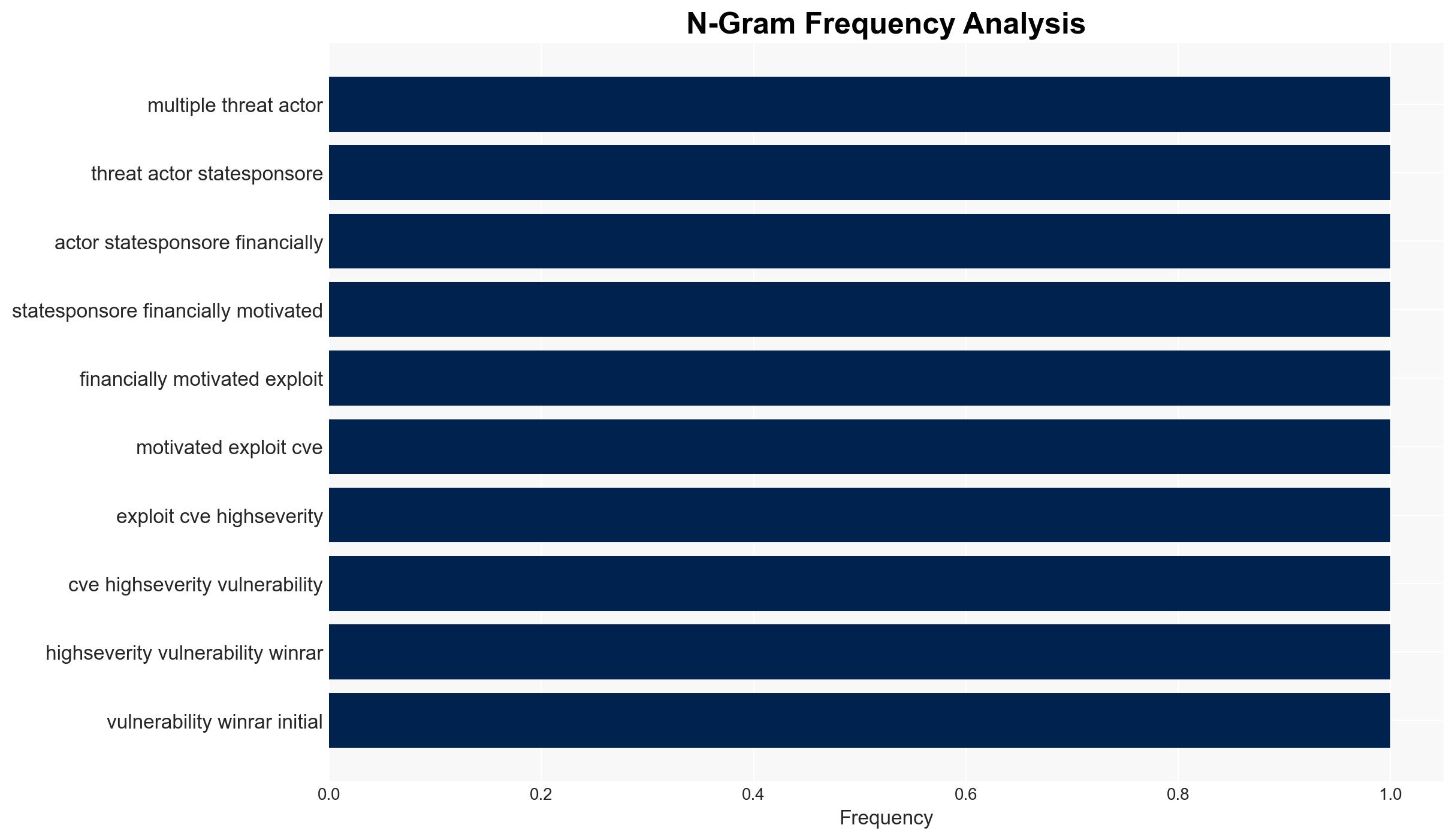
The CVE-2025-8088 vulnerability in WinRAR is actively exploited by both state-sponsored and financially motivated cyber actors, posing a significant threat to cybersecurity. The exploitation involves path traversal to deliver malicious payloads, impacting entities such as Ukrainian military units. The current assessment indicates a moderate confidence level in the ongoing risk and the involvement of multiple threat actors.
2. Competing Hypotheses
- Hypothesis A: The exploitation of the WinRAR vulnerability is primarily driven by state-sponsored actors for espionage purposes, as evidenced by the involvement of groups like UNC4895 and APT44 targeting Ukrainian military units. However, the presence of financially motivated actors suggests a broader spectrum of motivations.
- Hypothesis B: The exploitation is predominantly a commoditized cybercrime operation, facilitated by the sale of exploits by actors like “zeroplayer,” with state-sponsored activities being a secondary aspect. The widespread use by various actors supports this view, but the targeted nature of some attacks suggests strategic objectives.
- Assessment: Hypothesis A is currently better supported due to the specific targeting of Ukrainian military entities by known state-sponsored groups, indicating strategic objectives. Indicators such as changes in geopolitical tensions or new exploit sales could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability remains unpatched or inadequately mitigated; state-sponsored actors have strategic motivations; financially motivated actors are opportunistic.
- Information Gaps: Details on the full scope of affected entities; specific motivations of financially motivated actors; potential mitigation measures in place.
- Bias & Deception Risks: Potential bias in attributing state-sponsored activity without full evidence; deception by actors to obfuscate true motivations.
4. Implications and Strategic Risks
The exploitation of the WinRAR vulnerability could lead to increased cyber espionage and financial crime, affecting geopolitical stability and economic security.
- Political / Geopolitical: Escalation of cyber tensions between Russia and Ukraine; potential for retaliatory cyber actions.
- Security / Counter-Terrorism: Increased threat to military and governmental cybersecurity; potential for broader cyber warfare tactics.
- Cyber / Information Space: Enhanced cyber threat landscape; potential for misinformation campaigns leveraging compromised systems.
- Economic / Social: Economic impact due to financial theft and disruption; potential erosion of trust in digital systems.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement patches and mitigations for WinRAR; enhance monitoring of known threat actor activities; increase awareness among potential targets.
- Medium-Term Posture (1–12 months): Develop resilience measures against similar vulnerabilities; strengthen international cyber cooperation; invest in threat intelligence capabilities.
- Scenario Outlook: Best: Vulnerability patched and threat actor activity diminishes. Worst: Continued exploitation leads to significant geopolitical tensions. Most-Likely: Ongoing exploitation with periodic spikes in activity, driven by geopolitical and financial incentives.
6. Key Individuals and Entities
- UNC4895 (RomCom/CIGAR)
- APT44 (FROZENBARENTS)
- TEMP.Armageddon (CARPATHIAN)
- Turla (SUMMIT)
- China-linked actors
- “zeroplayer” (exploit supplier)
7. Thematic Tags
cybersecurity, cyber-espionage, vulnerability exploitation, state-sponsored actors, financial cybercrime, geopolitical tensions, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us