Open-source malware surges raising cyber security concerns – BusinessLine
Published on: 2025-10-18
Intelligence Report: Open-source malware surges raising cyber security concerns – BusinessLine
1. BLUF (Bottom Line Up Front)
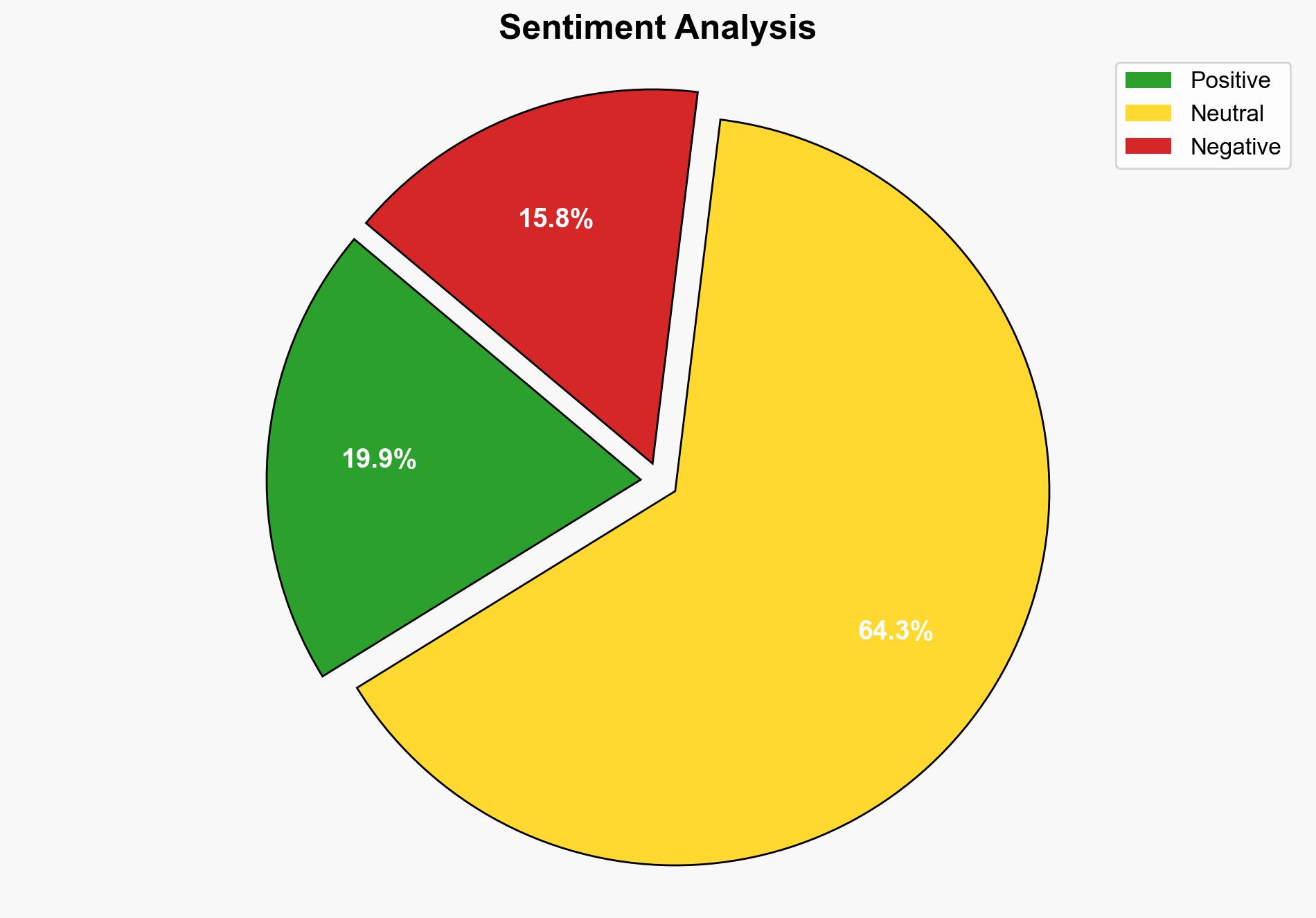
The surge in open-source malware represents a significant threat to cybersecurity, primarily due to the exploitation of trusted open-source ecosystems. The most supported hypothesis suggests that this increase is driven by sophisticated, organized cyber actors leveraging AI to embed malicious code within widely used software packages. Confidence level: High. Recommended action: Enhance automated detection systems and strengthen security protocols within open-source communities.
2. Competing Hypotheses
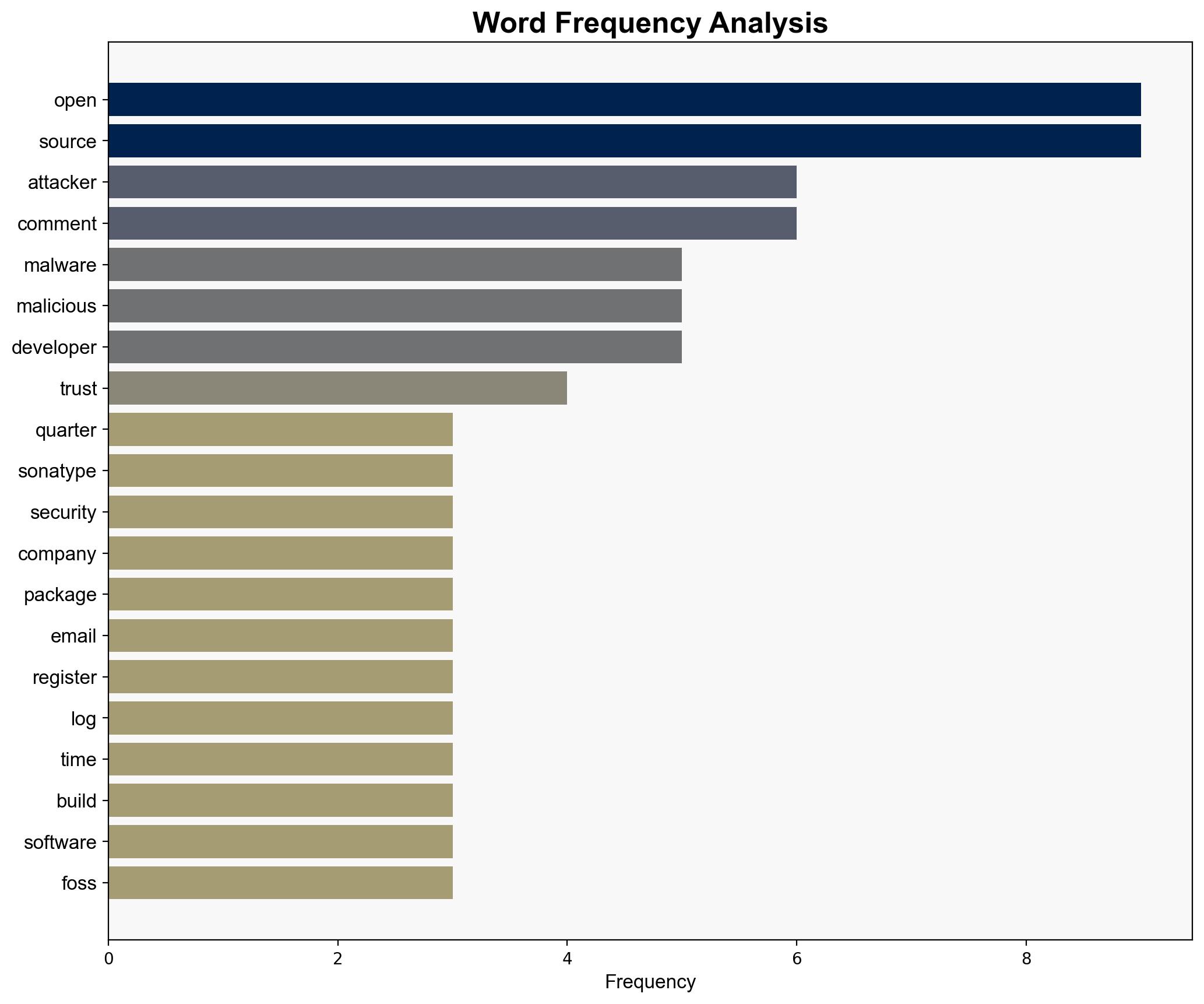
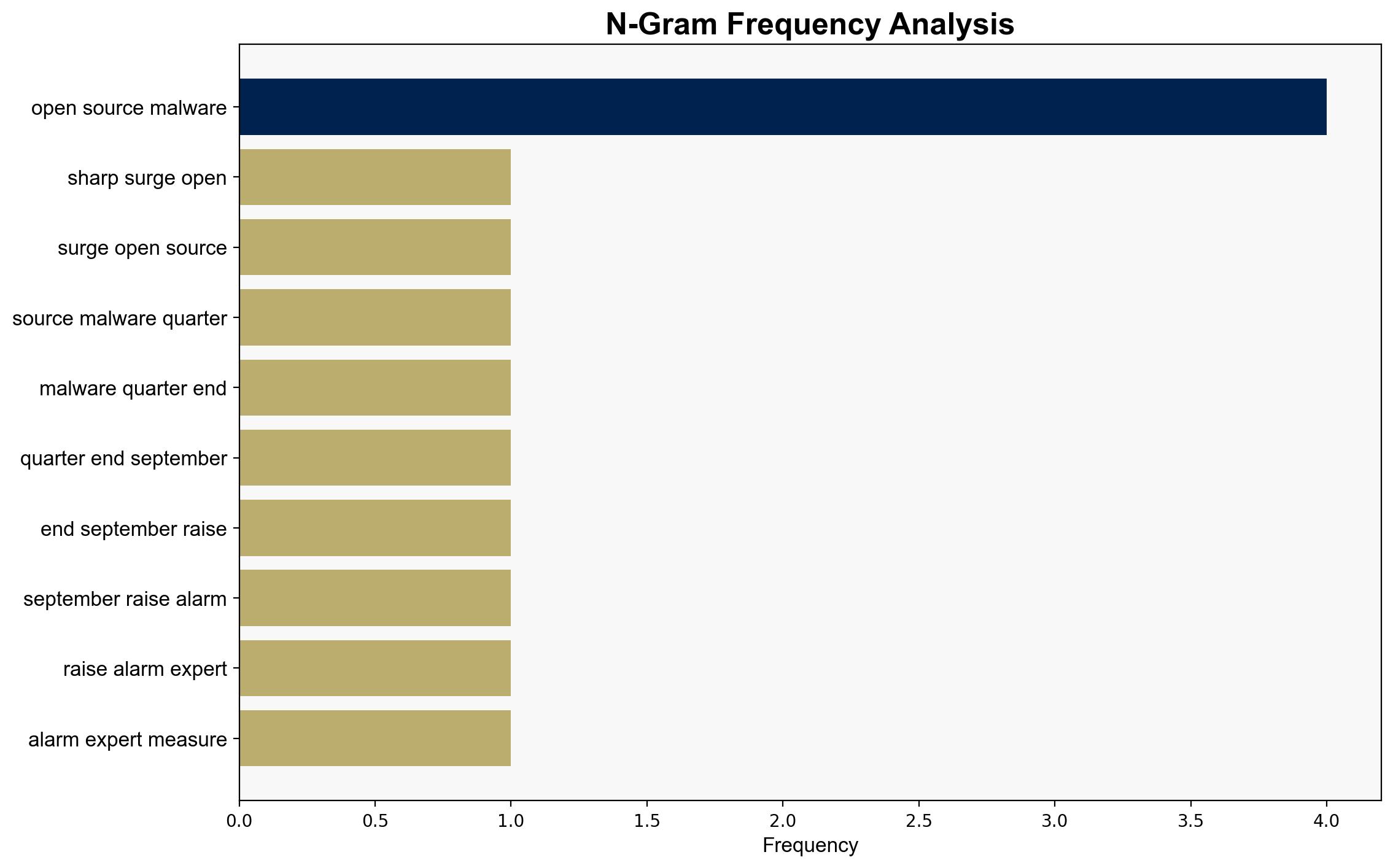
Hypothesis 1: The surge in open-source malware is primarily driven by organized cybercriminal groups using AI to exploit vulnerabilities in open-source ecosystems. These actors are embedding malicious code in widely trusted packages, turning them into vectors for large-scale data theft and supply chain attacks.
Hypothesis 2: The increase in open-source malware is largely opportunistic, driven by individual hackers exploiting the relatively low barrier to entry and high trust in open-source platforms. These actors use social engineering tactics, such as phishing, to gain access and distribute malware.
Using ACH 2.0, Hypothesis 1 is better supported due to the sophisticated nature of the attacks and the strategic use of AI, as indicated by the structured and patient approach described in the source text.
3. Key Assumptions and Red Flags
– Assumptions for Hypothesis 1 include the belief that cybercriminal groups have the resources and expertise to deploy AI effectively.
– Hypothesis 2 assumes that individual hackers can achieve similar levels of impact as organized groups.
– Red flags include the lack of specific attribution to known cybercriminal groups and the potential underestimation of individual hacker capabilities.
– Blind spots may involve the evolving nature of AI tools and their accessibility to less organized actors.
4. Implications and Strategic Risks
The proliferation of open-source malware could lead to widespread data breaches, undermining trust in digital infrastructure and open-source software. This could have cascading effects on economic stability and national security, as critical systems may become compromised. There is also a geopolitical risk if state-sponsored actors exploit these vulnerabilities to conduct espionage or disrupt critical infrastructure.
5. Recommendations and Outlook
- Enhance collaboration between open-source communities and cybersecurity firms to develop robust automated detection and response systems.
- Implement stricter verification processes for open-source contributions and increase awareness of social engineering tactics among developers.
- Scenario-based projections:
- Best Case: Successful implementation of enhanced security measures reduces the incidence of malware, restoring trust in open-source platforms.
- Worst Case: Failure to address vulnerabilities leads to a major breach, causing significant economic and reputational damage.
- Most Likely: Incremental improvements in security measures lead to a gradual reduction in successful attacks, though the threat persists.
6. Key Individuals and Entities
– Brian Fox
– Ankit Sharma
– Anvar Sadath
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus