OpenClaw’s rise raises alarms as malicious extensions exploit user trust to spread malware
Published on: 2026-02-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Moltbot is now OpenClaw – but watch out malicious ‘skills’ are still trying to trick victims into spreading malware
1. BLUF (Bottom Line Up Front)
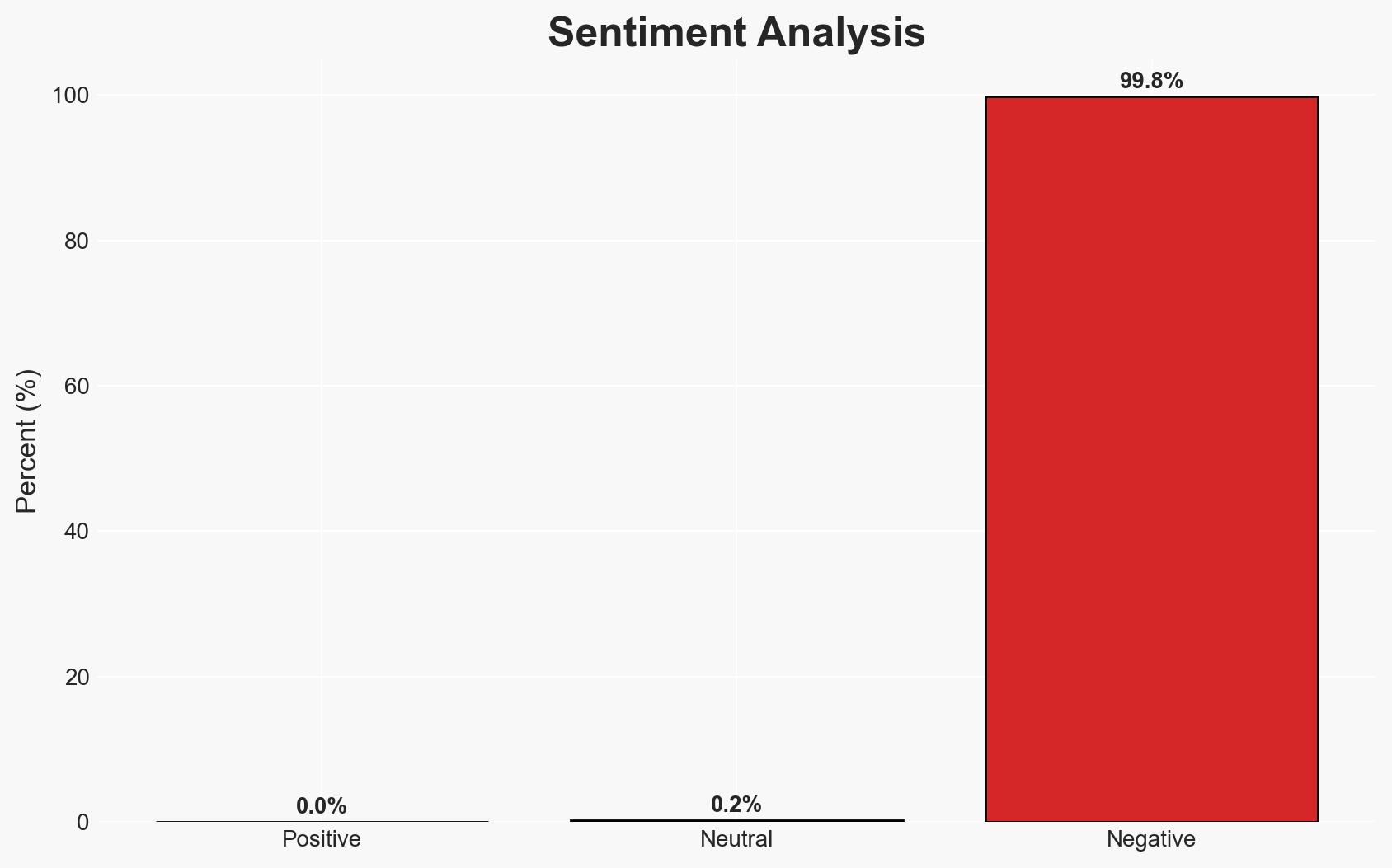
The rebranding of Moltbot to OpenClaw has been exploited by threat actors to distribute malware via malicious ‘skills’ in its ecosystem. This poses a significant cybersecurity risk to users across Windows and macOS platforms, with moderate confidence in the assessment that the lack of sandboxing and reliance on user trust are primary vulnerabilities. The situation requires immediate attention from cybersecurity stakeholders.
2. Competing Hypotheses
- Hypothesis A: The primary threat arises from the inherent vulnerabilities in OpenClaw’s ecosystem, particularly the lack of sandboxing for third-party skills, which allows malicious actors to exploit these extensions to distribute malware. This is supported by the recent incidents of malicious skills being uploaded and the reliance on user trust.
- Hypothesis B: The threat is primarily due to social engineering tactics rather than technical vulnerabilities, as attackers rely on convincing users to execute commands that lead to malware installation. This is supported by the use of obfuscated terminal commands and fake extensions.
- Assessment: Hypothesis A is currently better supported due to the systemic nature of the vulnerabilities in the OpenClaw ecosystem, which allows for widespread exploitation. Indicators such as the rapid upload of malicious skills and the lack of sandboxing reinforce this judgment. However, increased sophistication in social engineering tactics could shift this assessment.
3. Key Assumptions and Red Flags
- Assumptions: OpenClaw will continue to allow third-party skills without sandboxing; users will not consistently verify the legitimacy of skills; attackers will exploit name changes for deception.
- Information Gaps: The full extent of the compromised systems and the specific methods used by attackers to bypass existing security measures.
- Bias & Deception Risks: Potential underestimation of user vigilance and over-reliance on reported incidents without considering unreported cases; possible misinformation from threat actors exploiting the rebranding.
4. Implications and Strategic Risks
This development could lead to increased cybersecurity incidents and a loss of trust in AI-driven automation tools. It may also prompt regulatory scrutiny and changes in software security standards.
- Political / Geopolitical: Potential for increased international cooperation on cybersecurity standards and regulations.
- Security / Counter-Terrorism: Heightened threat environment as attackers leverage AI tools for broader cyber operations.
- Cyber / Information Space: Increased risk of cyber-espionage and data breaches through compromised systems.
- Economic / Social: Potential economic impact due to data breaches and loss of consumer trust in AI technologies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of OpenClaw’s ecosystem for malicious skills, implement stricter verification processes for skills, and increase user awareness campaigns.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to improve threat detection capabilities, and advocate for industry-wide standards for AI tool security.
- Scenario Outlook: Best: Improved security measures and user awareness reduce incidents. Worst: Continued exploitation leads to significant breaches and regulatory backlash. Most-Likely: Incremental improvements in security with ongoing challenges from sophisticated attacks.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
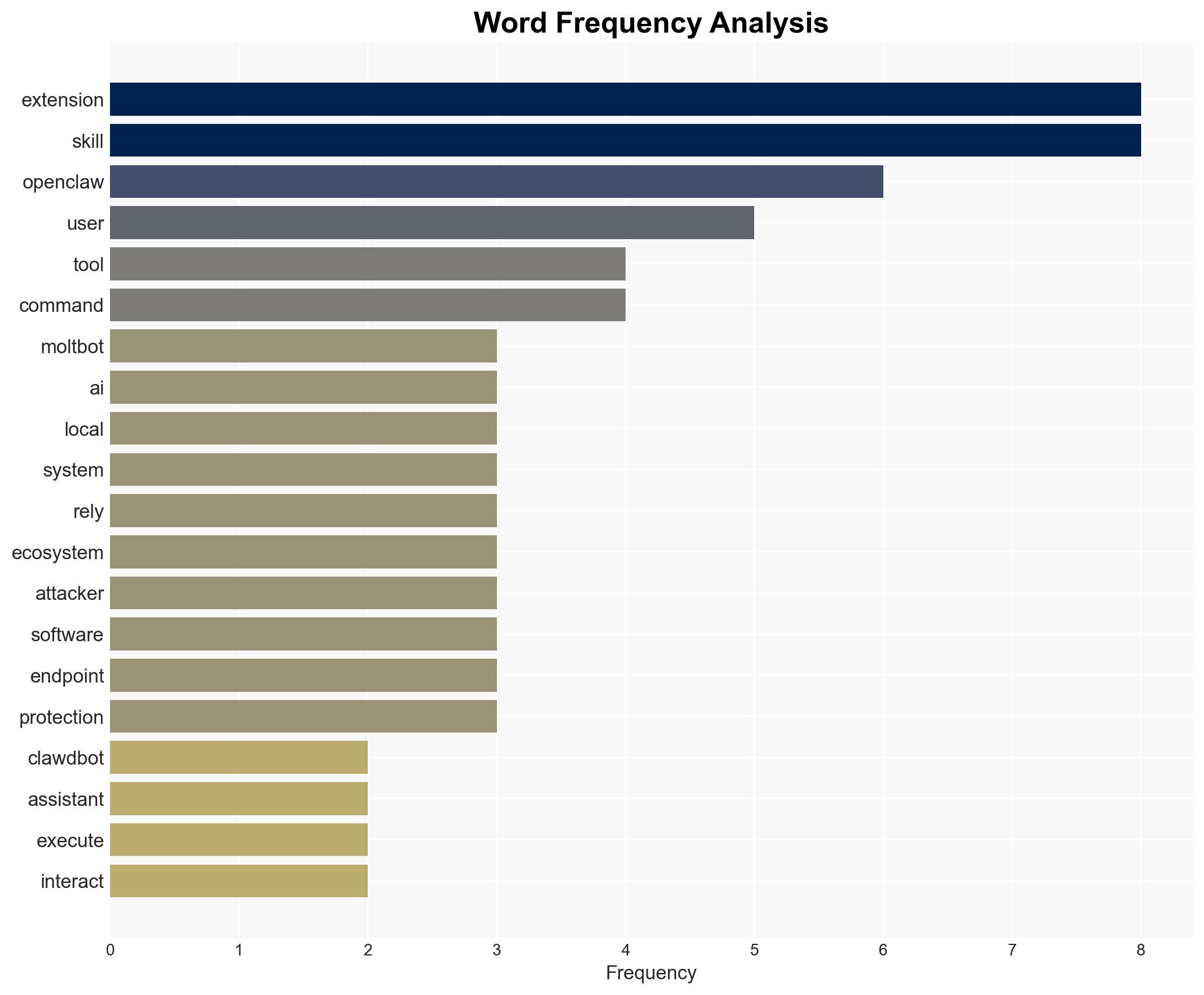
cybersecurity, malware, AI tools, social engineering, software vulnerabilities, user trust, digital threats
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us