Oracle hopes talk of cloud data theft dies off CISA just resurrected it for Easter – Theregister.com
Published on: 2025-04-18
Intelligence Report: Oracle Cloud Data Theft and CISA Alert
1. BLUF (Bottom Line Up Front)
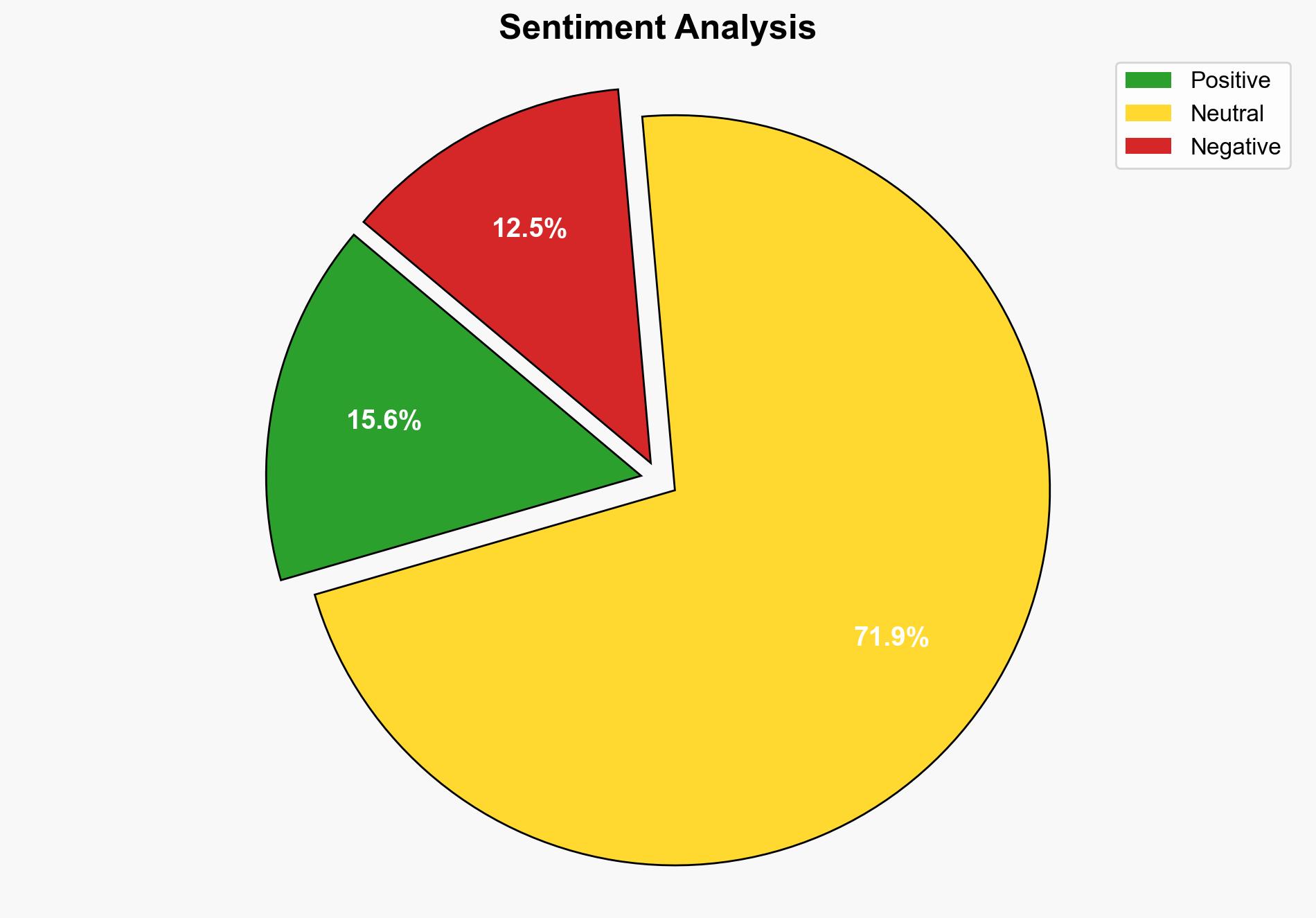
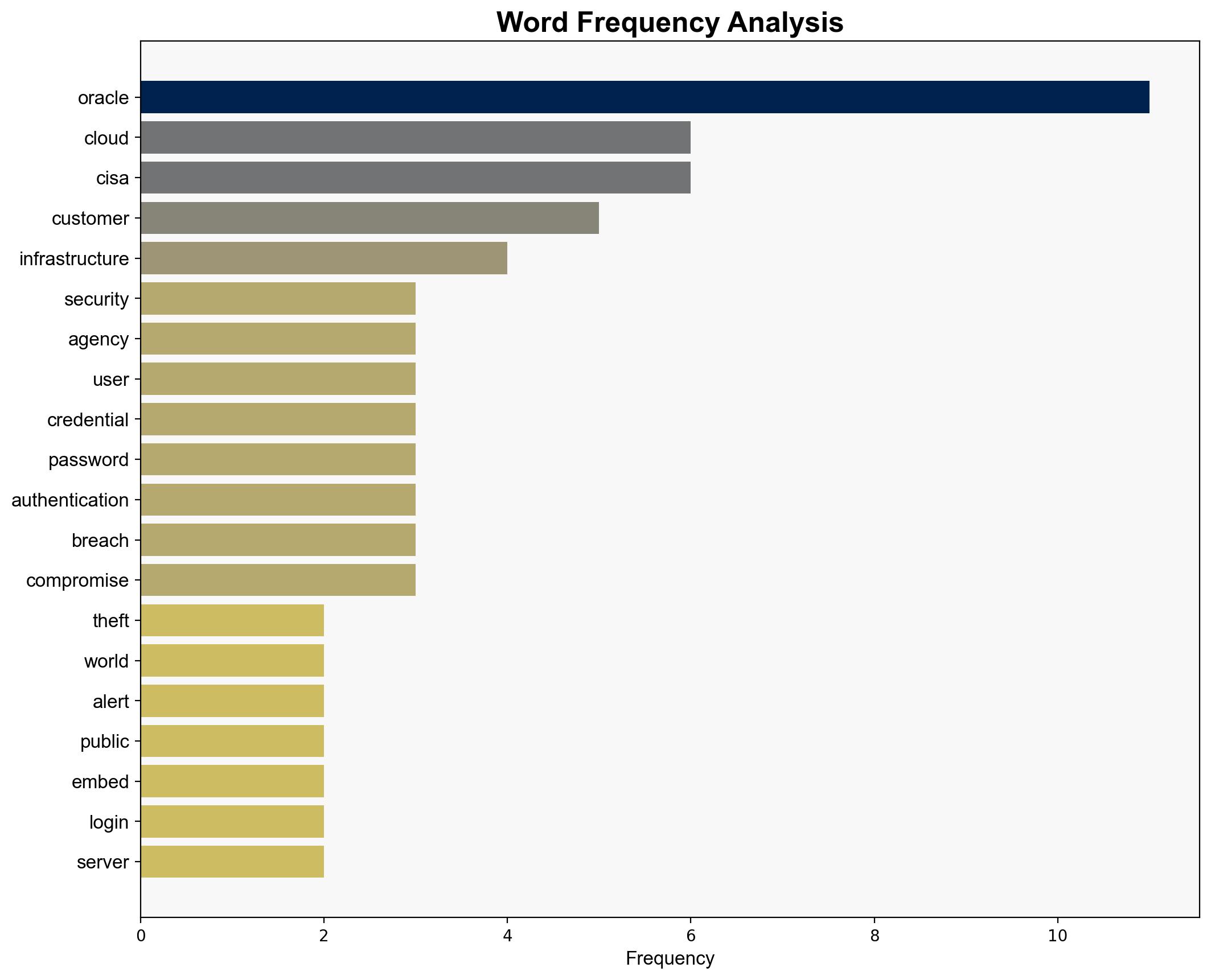
Oracle’s public cloud infrastructure experienced a security breach, leading to the theft of customer data, including encrypted passwords and authentication tokens. The Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert recommending immediate security measures. This incident poses significant risks to enterprise environments, with potential legal and reputational repercussions for Oracle.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
The breach may have resulted from a failure to patch obsolete login servers, leading to unauthorized access. Possible motivations include financial gain through the sale of stolen credentials or exploitation of compromised systems.
SWOT Analysis
Strengths: Oracle’s extensive cloud infrastructure and resources for damage control.
Weaknesses: Delayed acknowledgment of the breach and inadequate initial response.
Opportunities: Strengthening security protocols and rebuilding customer trust.
Threats: Legal actions, loss of customer confidence, and potential further breaches.
Indicators Development
Warning signs include unusual authentication activity, increased phishing attempts, and unauthorized access to privileged accounts. Monitoring these indicators can help preempt further security incidents.
3. Implications and Strategic Risks
The breach highlights vulnerabilities in cloud infrastructure security and the need for robust incident response strategies. It may influence regulatory scrutiny and impact Oracle’s market position. The incident underscores the importance of timely breach disclosure and comprehensive cybersecurity measures.
4. Recommendations and Outlook
- Implement immediate password resets and enforce phishing-resistant multi-factor authentication (MFA).
- Conduct a thorough security audit and patch all obsolete systems.
- Enhance transparency in communication with stakeholders to rebuild trust.
- Prepare for potential legal challenges and strengthen legal defenses.
- Scenario-based projections suggest increased regulatory oversight and potential shifts in customer loyalty if security measures are not improved.
5. Key Individuals and Entities
Oracle, CISA, The Register, Texas lawsuit plaintiffs.