Over 10,000 Fortinet firewalls remain vulnerable to critical 2FA bypass attacks despite available patches
Published on: 2026-01-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Over 10K Fortinet firewalls exposed to actively exploited 2FA bypass
1. BLUF (Bottom Line Up Front)
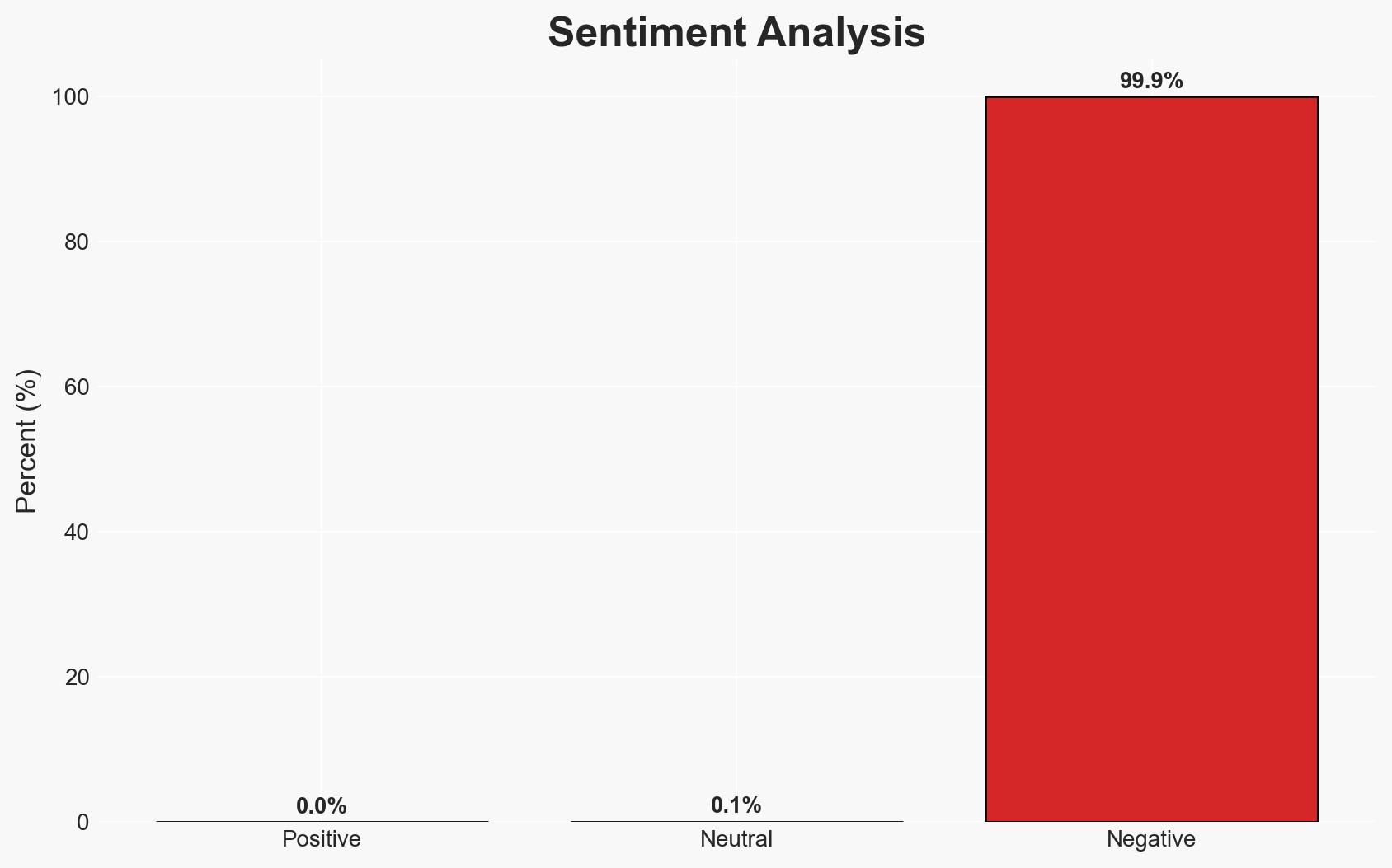
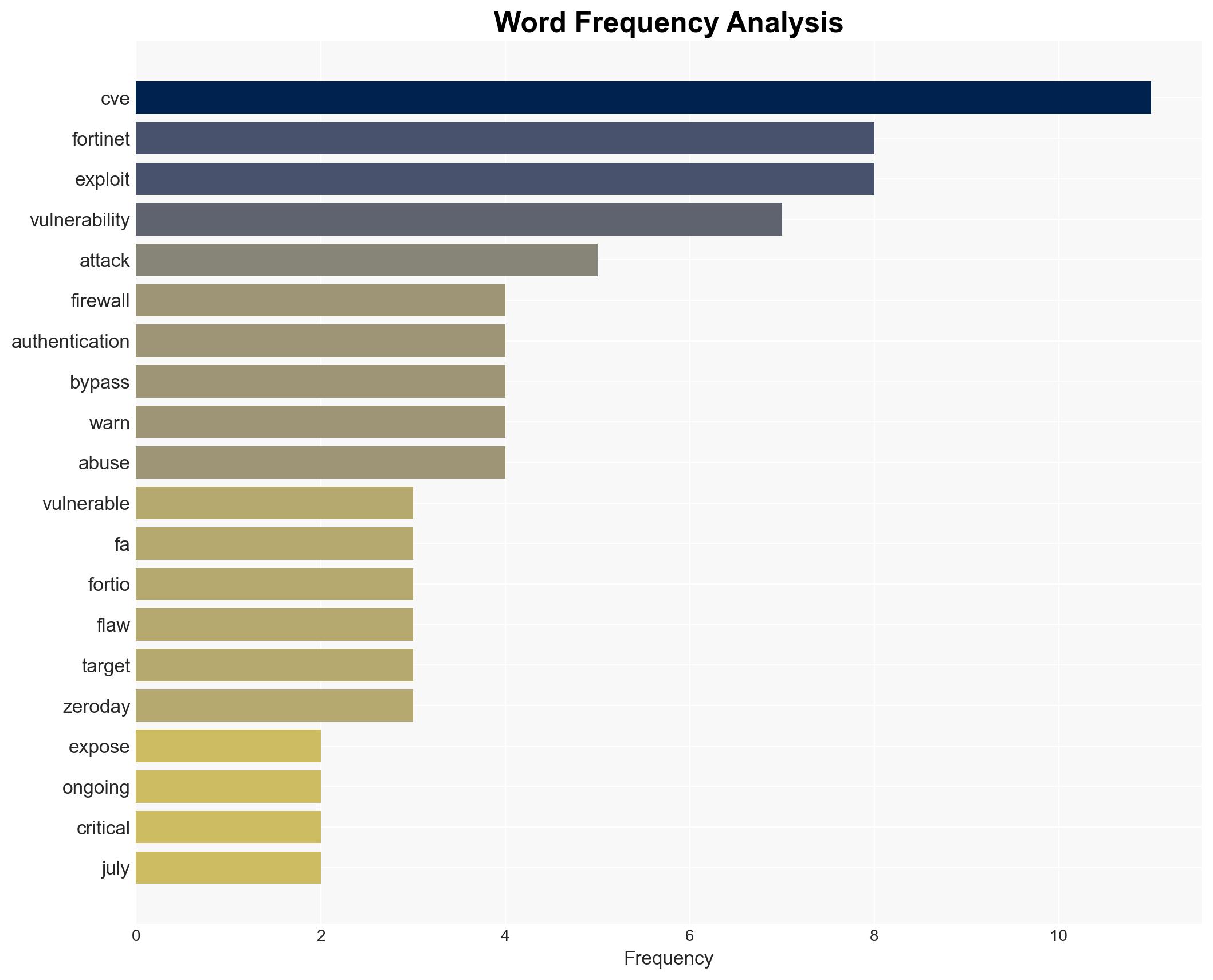
Over 10,000 Fortinet firewalls remain vulnerable to a critical 2FA bypass exploit (CVE-2020-12812), posing significant cybersecurity risks. This vulnerability is actively exploited, particularly targeting configurations with LDAP enabled. The exposure affects numerous entities, including over 1,300 in the United States, with moderate confidence that state-sponsored actors are involved. Immediate mitigation is essential to prevent further exploitation.
2. Competing Hypotheses
- Hypothesis A: The primary threat actors exploiting the vulnerability are state-sponsored groups aiming to gather intelligence or disrupt operations. This is supported by historical targeting patterns and previous warnings from CISA and the FBI. However, the specific actors involved remain unidentified.
- Hypothesis B: Cybercriminal groups are exploiting the vulnerability for financial gain, such as ransomware deployment. This is plausible given the known use of the vulnerability in ransomware attacks, but lacks direct attribution evidence.
- Assessment: Hypothesis A is currently better supported due to past state-sponsored activity targeting Fortinet vulnerabilities and the strategic value of compromised firewalls. Indicators such as increased targeting of critical infrastructure could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability remains unpatched due to lack of awareness or resource constraints; state-sponsored actors prioritize intelligence gathering over immediate disruption; Fortinet’s advisories are fully accurate.
- Information Gaps: Specific attribution of current exploitations; detailed impact assessments on affected networks; confirmation of mitigation measures taken by affected entities.
- Bias & Deception Risks: Potential over-reliance on vendor reports; confirmation bias towards state-sponsored actor involvement; possible underestimation of cybercriminal capabilities.
4. Implications and Strategic Risks
This vulnerability’s continued exploitation could lead to significant disruptions in affected sectors, particularly if leveraged by state-sponsored actors for strategic gains. The situation may escalate if not addressed promptly, affecting geopolitical stability and economic interests.
- Political / Geopolitical: Increased tensions between nations if state-sponsored involvement is confirmed, potentially leading to retaliatory cyber operations.
- Security / Counter-Terrorism: Heightened threat environment for critical infrastructure, necessitating enhanced defensive measures.
- Cyber / Information Space: Potential for widespread data breaches and information operations leveraging compromised systems.
- Economic / Social: Disruption of services could lead to economic losses and erode public trust in cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch vulnerable systems; increase monitoring for signs of exploitation; disseminate threat intelligence to potentially affected entities.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing; enhance cybersecurity resilience through training and resource allocation; invest in advanced threat detection capabilities.
- Scenario Outlook: Best: Rapid patching reduces threat; Worst: Major breach occurs; Most-Likely: Continued exploitation with moderate impact. Triggers include patch adoption rates and actor activity levels.
6. Key Individuals and Entities
- Fortinet (vendor)
- CISA (Cybersecurity and Infrastructure Security Agency)
- FBI (Federal Bureau of Investigation)
- Shadowserver (Internet security watchdog)
- Arctic Wolf (cybersecurity company)
- Chinese Volt Typhoon (threat group)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, state-sponsored threats, vulnerability management, critical infrastructure, cyber-espionage, ransomware, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us