Pakistan enforces VPN bans and surveillance backdoors, intensifying digital authoritarianism and censorship.
Published on: 2026-01-07
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Pakistan blocks global VPNs mandates state surveillance backdoors in digital crackdown
1. BLUF (Bottom Line Up Front)
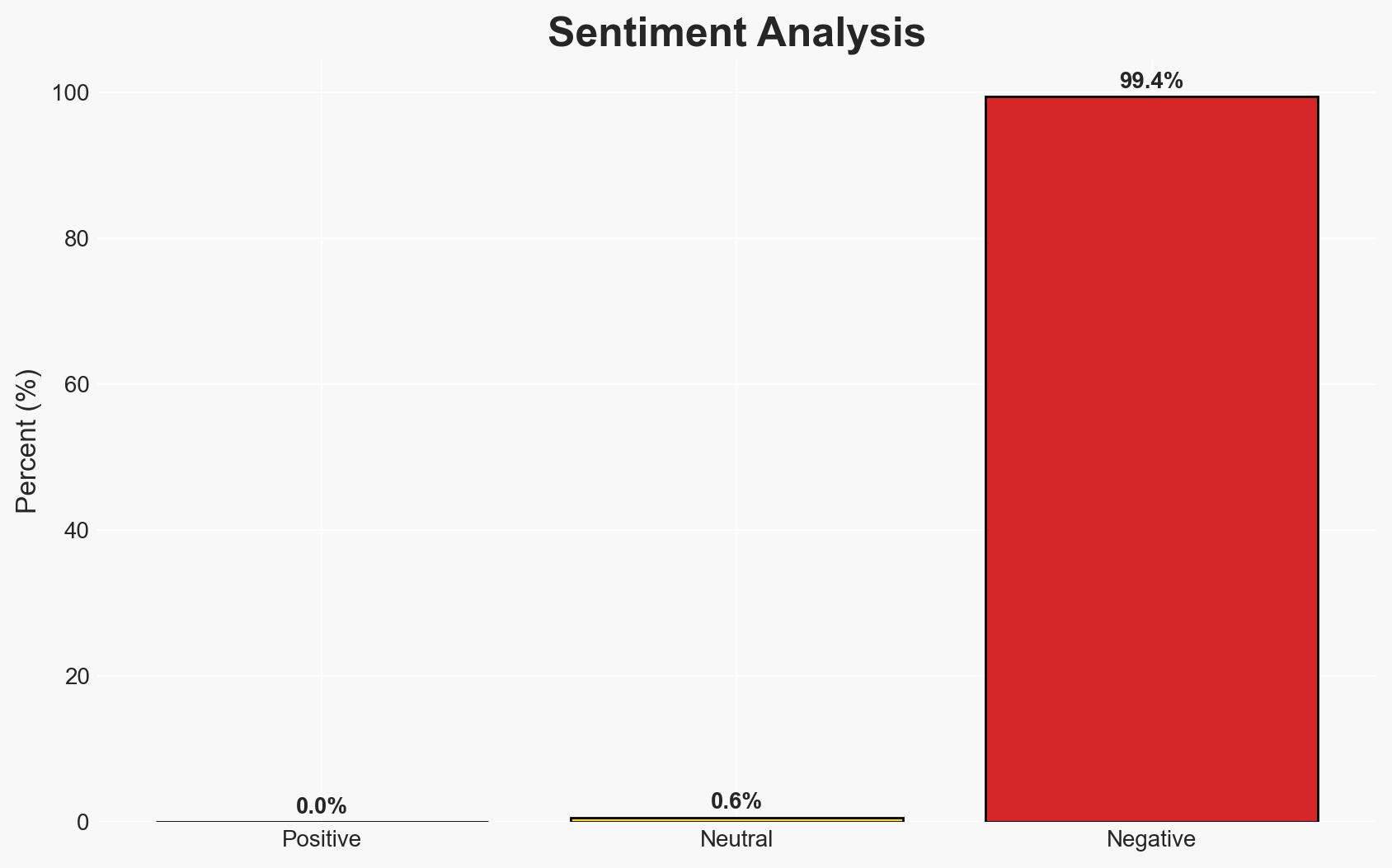
Pakistan’s recent policy to block global VPN services and mandate state surveillance backdoors represents a significant move towards digital authoritarianism, impacting citizens’ privacy and the tech sector. This action aligns with global trends of increased state control over digital spaces. The most likely hypothesis is that this is a strategic effort to suppress dissent and control information flow. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
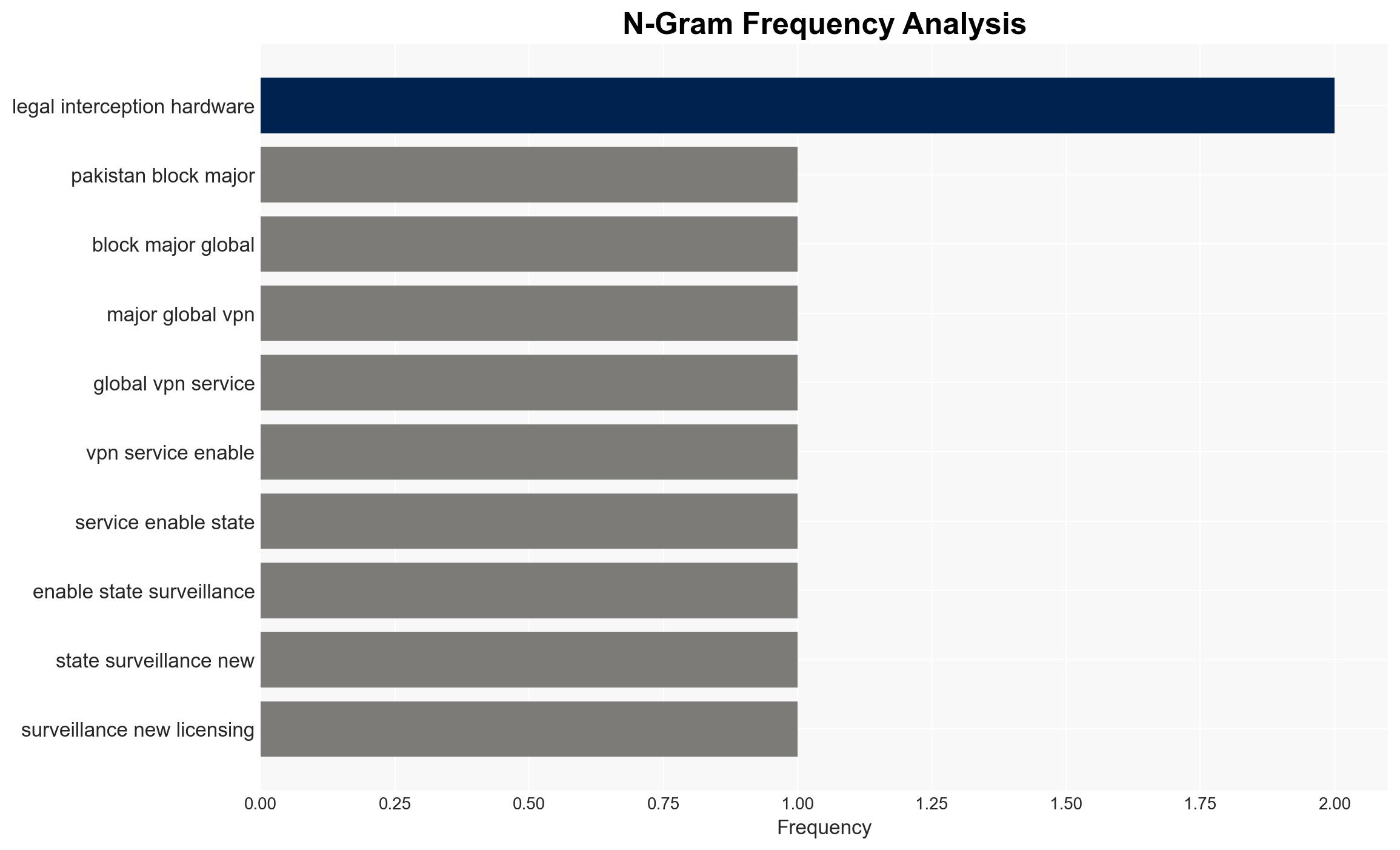
- Hypothesis A: The Pakistani government is implementing these measures primarily to enhance national security by monitoring potential threats. Supporting evidence includes the installation of “Legal Interception” hardware. However, this is contradicted by the broad scope of surveillance and the impact on civil liberties, suggesting ulterior motives.
- Hypothesis B: The primary goal is to suppress dissent and control information, aligning with authoritarian practices globally. This is supported by the immediate impact on digital rights and the tech sector, as well as the historical context of similar actions by other regimes. Contradictory evidence is minimal, but the stated security rationale could partially justify the measures.
- Assessment: Hypothesis B is currently better supported due to the alignment with global authoritarian trends and the significant impact on civil liberties and economic innovation. Indicators such as increased domestic unrest or international condemnation could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The government prioritizes control over digital spaces; VPNs are primarily used for privacy rather than illicit activities; the tech sector will be significantly impacted.
- Information Gaps: Detailed government rationale for the policy; data on the actual impact on national security; public sentiment and compliance levels.
- Bias & Deception Risks: Potential government narrative framing this as a security measure; confirmation bias in interpreting global patterns as uniformly authoritarian.
4. Implications and Strategic Risks
This development could lead to increased domestic unrest and international criticism, affecting Pakistan’s global standing and economic prospects. Over time, it may contribute to a more controlled and censored information environment.
- Political / Geopolitical: Potential for increased diplomatic tensions and isolation; alignment with other authoritarian regimes.
- Security / Counter-Terrorism: Possible short-term gains in monitoring capabilities, but long-term risks of radicalization due to suppressed dissent.
- Cyber / Information Space: Increased state control over digital communications; potential for cyber resistance or circumvention efforts.
- Economic / Social: Negative impact on the tech sector and innovation; potential for social unrest due to perceived oppression.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor public and international reactions; assess compliance and enforcement effectiveness; engage with digital rights organizations for insights.
- Medium-Term Posture (1–12 months): Develop resilience measures for affected sectors; explore diplomatic channels to address human rights concerns; consider partnerships to support digital freedom.
- Scenario Outlook:
- Best: Policy rollback due to international pressure and domestic unrest.
- Worst: Further entrenchment of surveillance and control, leading to increased isolation.
- Most-Likely: Continued enforcement with gradual adaptation by citizens and tech sector.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
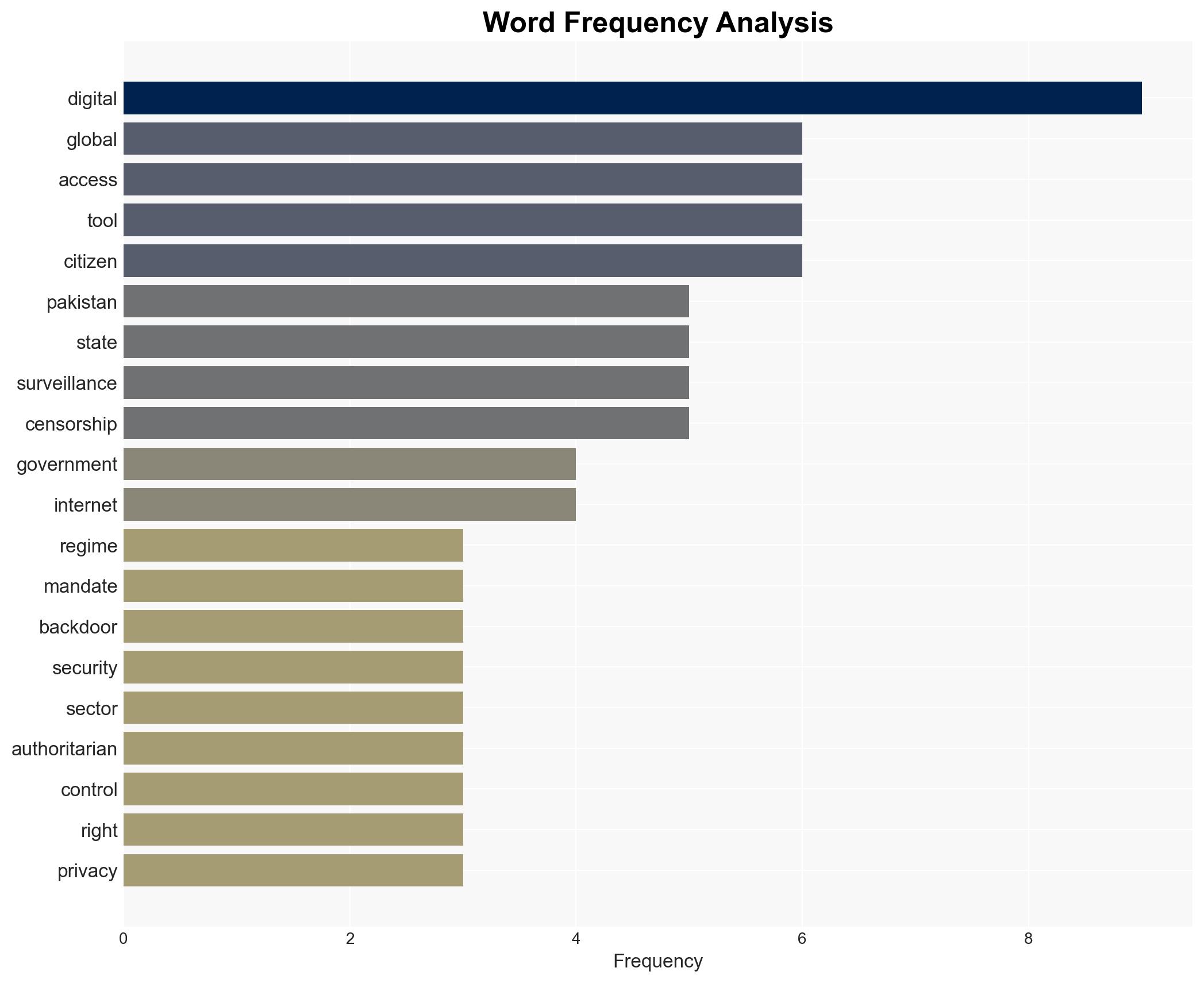
cybersecurity, digital authoritarianism, state surveillance, VPN restrictions, internet freedom, tech sector impact, information control, civil liberties
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us