Pakistani-based malware empire ‘punished’ software pirates with infostealers earning millions of dollars in just five years – here’s how to stay safe – TechRadar
Published on: 2025-08-17
Intelligence Report: Pakistani-based malware empire ‘punished’ software pirates with infostealers earning millions of dollars in just five years – here’s how to stay safe – TechRadar
1. BLUF (Bottom Line Up Front)
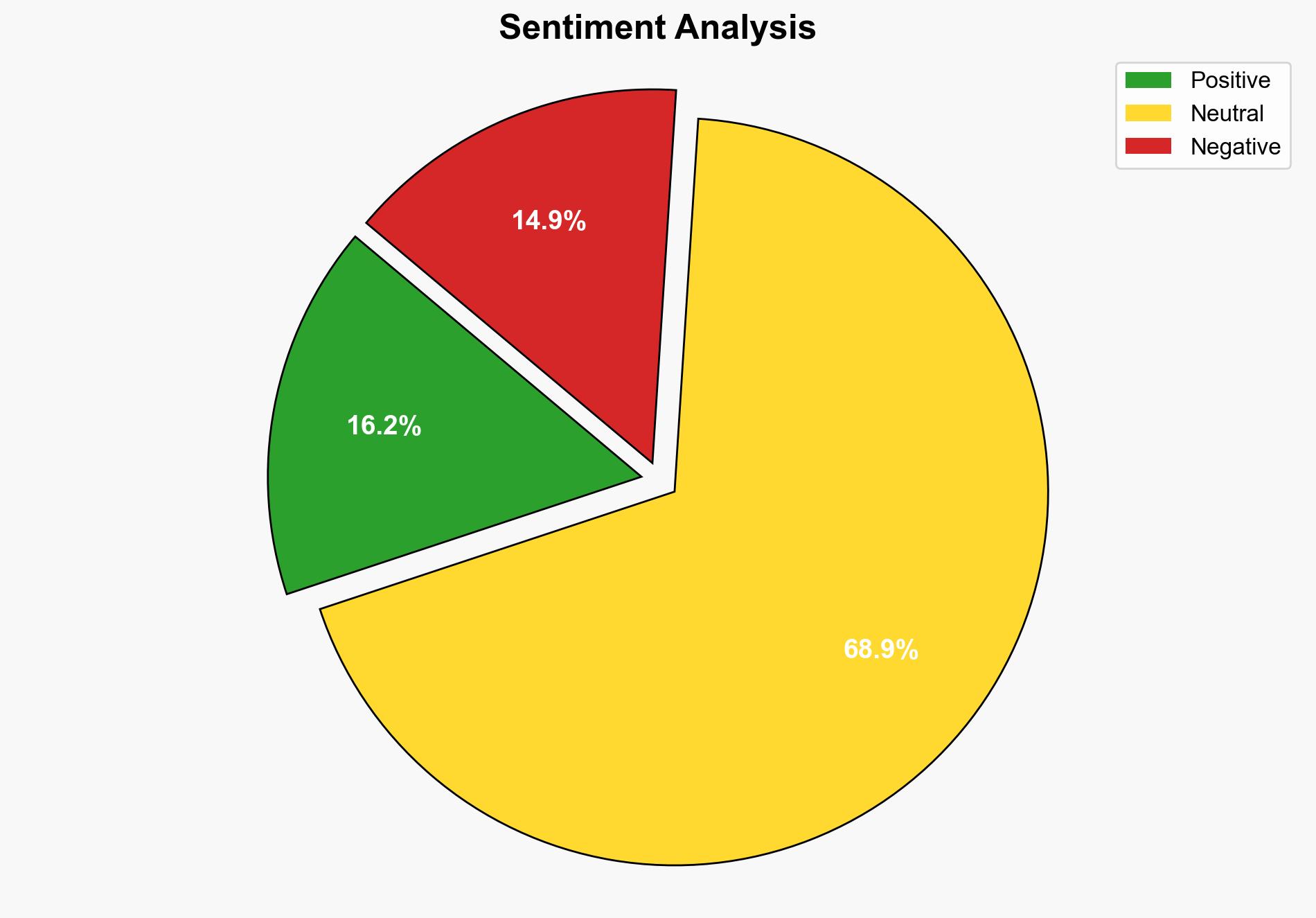
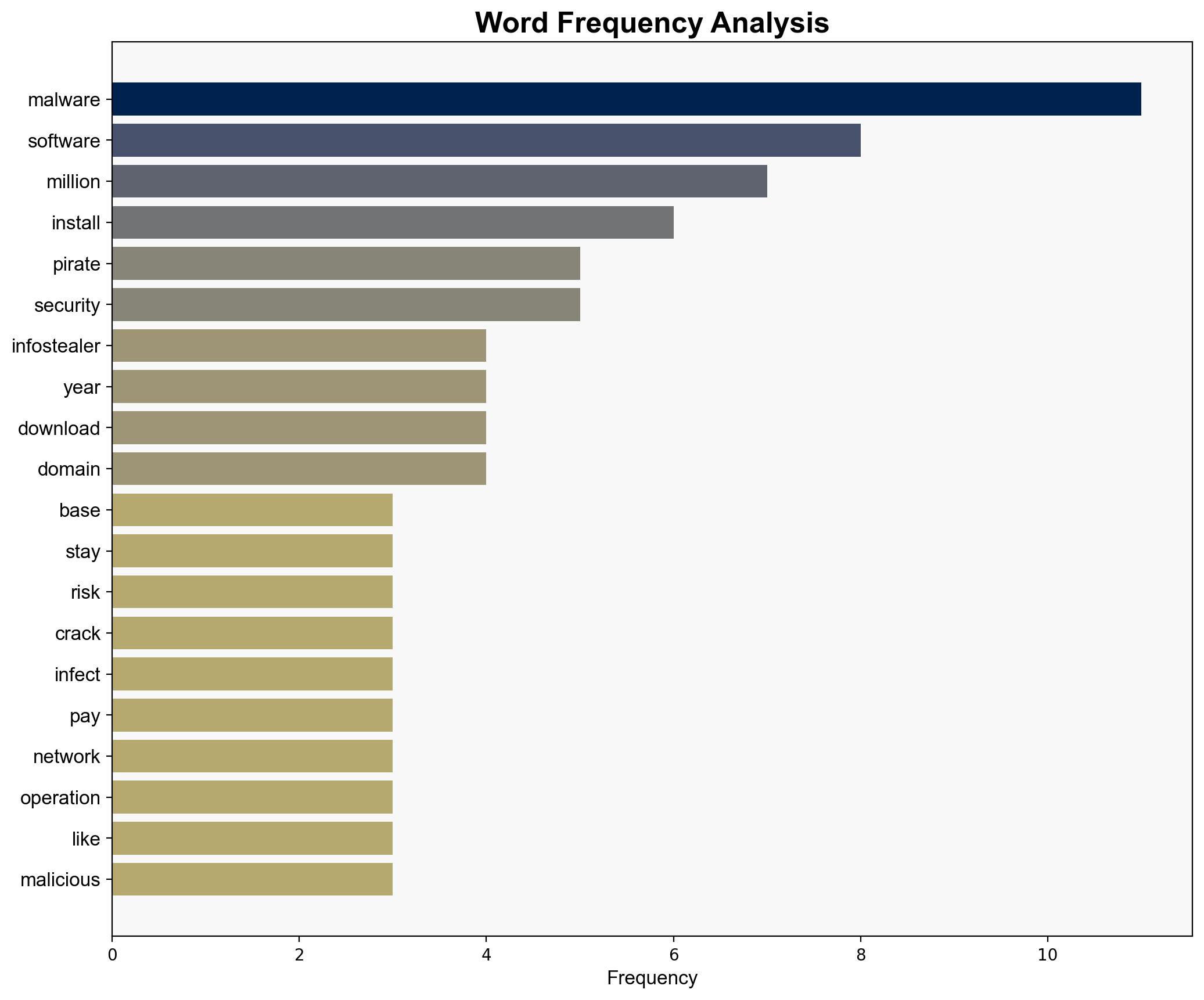
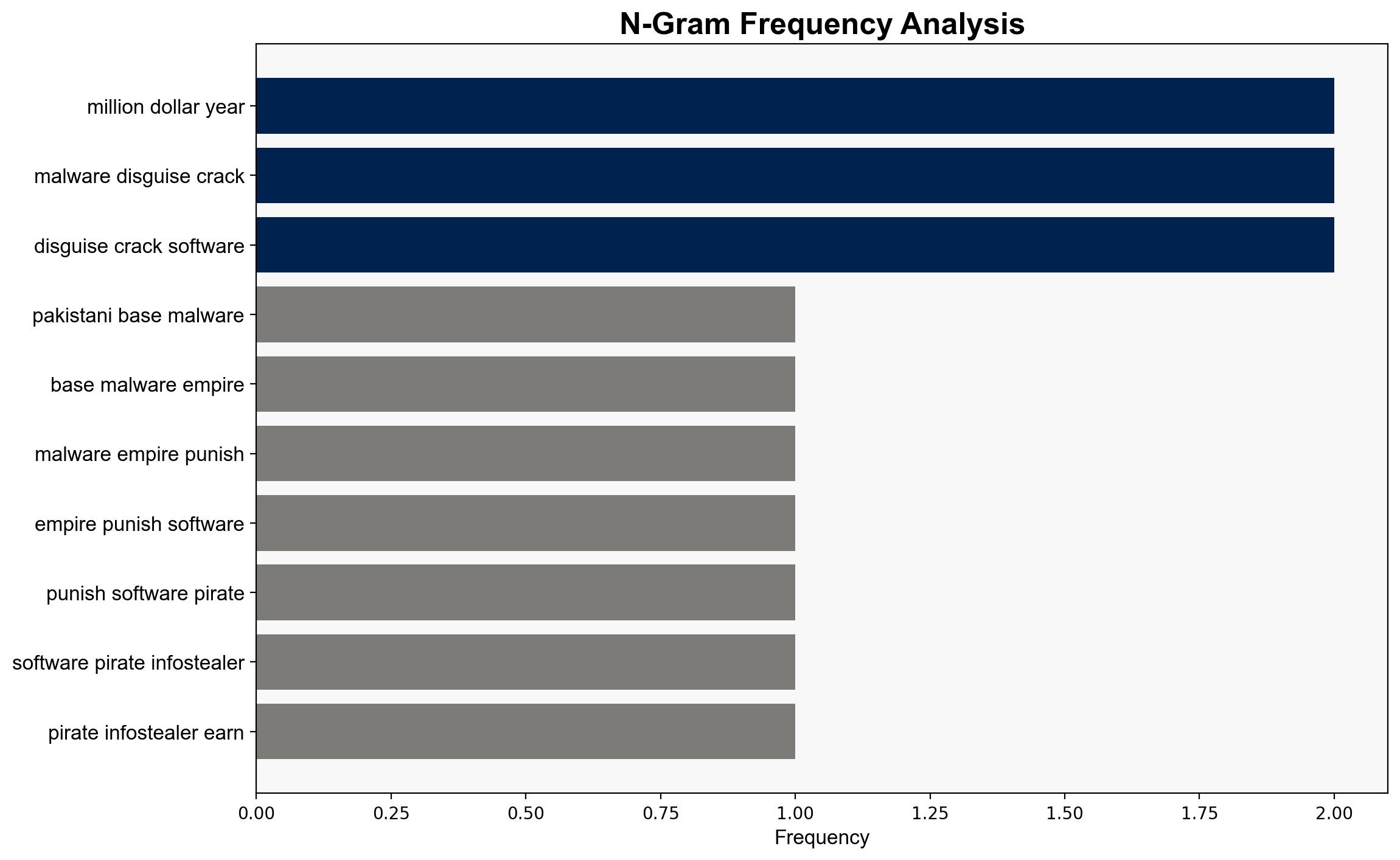
The most supported hypothesis is that a Pakistani-based cybercriminal network has effectively monetized software piracy by embedding infostealers in pirated software, generating significant revenue through a sophisticated affiliate network. Confidence Level: Moderate. Recommended action includes enhancing cybersecurity awareness and implementing robust protective measures against pirated software.
2. Competing Hypotheses
Hypothesis 1: The primary goal of the Pakistani-based cybercriminal network is financial gain through the distribution of infostealers embedded in pirated software. This operation is highly organized, leveraging SEO and affiliate networks to maximize reach and revenue.
Hypothesis 2: The operation serves a dual purpose: financial gain and potentially gathering intelligence or conducting espionage activities under the guise of a financially motivated cybercrime operation. The involvement of family members and recurring surnames suggests a deeper, possibly state-linked agenda.
Using ACH 2.0, Hypothesis 1 is better supported due to the clear financial structure and evidence of revenue generation, whereas Hypothesis 2 lacks direct evidence of espionage activities.
3. Key Assumptions and Red Flags
Assumptions:
– The network’s primary motivation is financial.
– SEO and affiliate networks are the main methods for spreading malware.
Red Flags:
– Lack of direct evidence linking the operation to espionage.
– Potential bias in assuming all operations are financially motivated without considering geopolitical implications.
– The report’s reliance on a single source (CloudSEK) may limit perspective.
Blind Spots:
– Possible underestimation of the network’s adaptability and potential state support.
4. Implications and Strategic Risks
The operation highlights the risk of using pirated software as a vector for cybercrime, potentially affecting millions globally. The economic impact includes financial losses for individuals and businesses, while the geopolitical risk involves potential state involvement in cyber operations. The psychological impact includes eroding trust in digital platforms and software security.
5. Recommendations and Outlook
- Enhance public awareness campaigns about the risks of pirated software.
- Strengthen international collaboration to dismantle affiliate networks.
- Encourage software developers to implement stronger anti-piracy measures.
- Best Case: Increased cybersecurity measures reduce the operation’s effectiveness.
- Worst Case: The network adapts, increasing sophistication and reach.
- Most Likely: Continued financial success with gradual adaptation to countermeasures.
6. Key Individuals and Entities
No specific individuals are named in the source text. The network is primarily traced to Bahawalpur and Faisalabad, suggesting a localized operational base.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus