Palo Alto Networks addresses critical DoS vulnerability that could disable firewalls for unauthorized users
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Palo Alto Networks warns of DoS bug letting hackers disable firewalls
1. BLUF (Bottom Line Up Front)
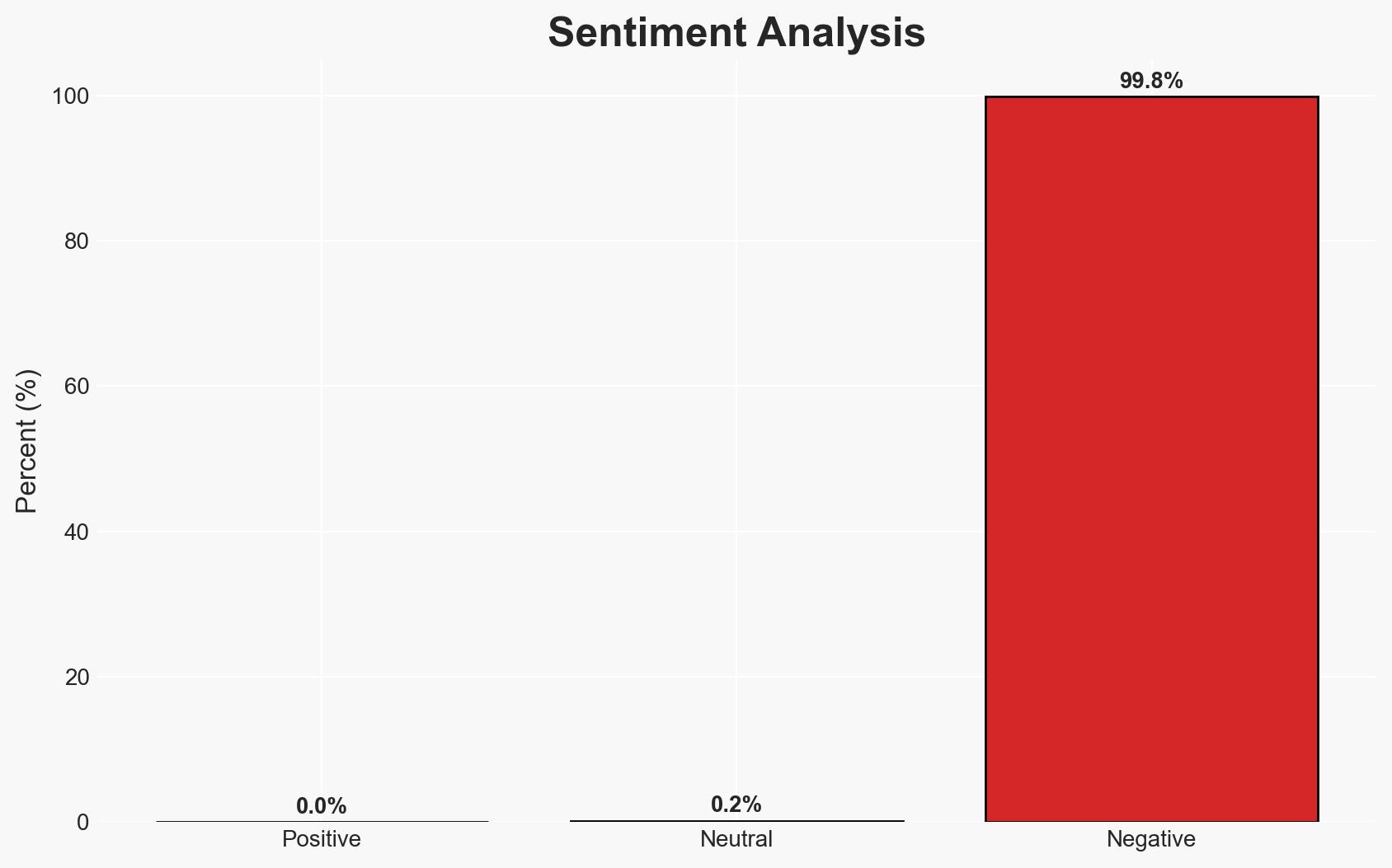
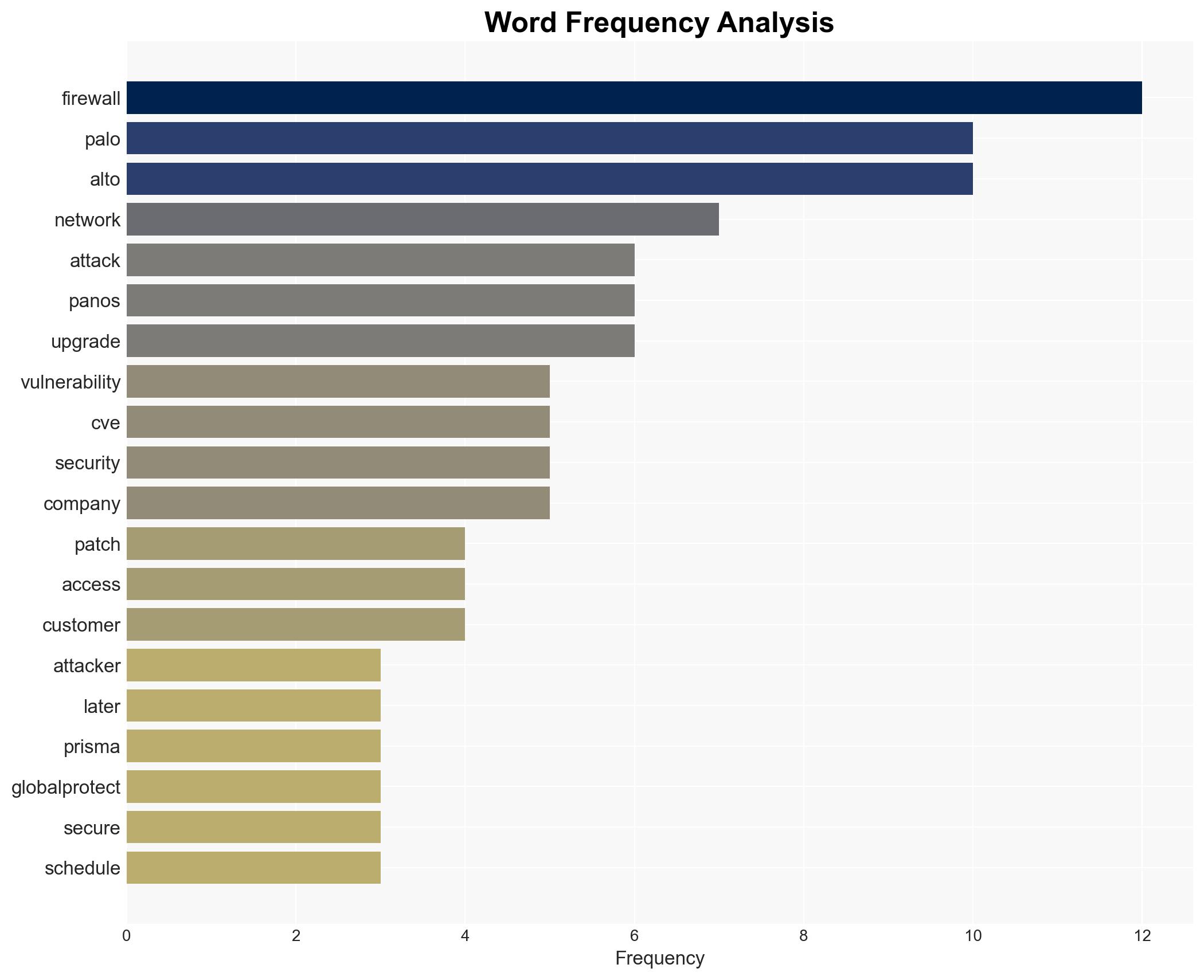
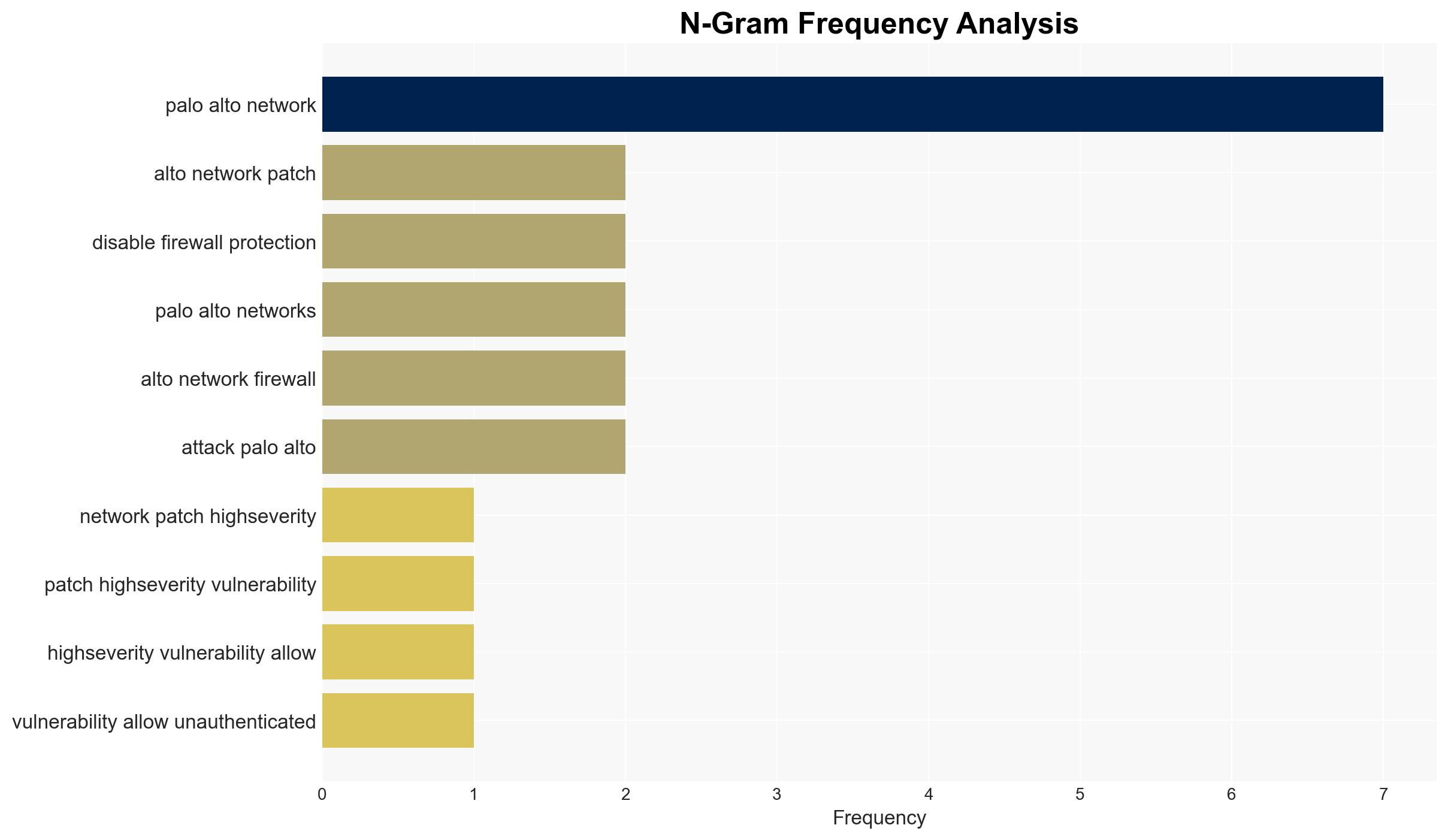
Palo Alto Networks has patched a high-severity vulnerability (CVE-2026-0227) affecting its next-generation firewalls and Prisma Access configurations, potentially allowing unauthenticated attackers to disable firewall protections via denial-of-service (DoS) attacks. The vulnerability has not yet been exploited in the wild, but the risk remains significant due to the exposure of nearly 6,000 firewalls online. The situation demands immediate attention to ensure all systems are patched. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The vulnerability will be exploited in the near term, leading to significant disruptions. This is supported by the history of Palo Alto Networks’ firewalls being targeted and the current exposure of many systems online. However, the lack of current exploitation evidence contradicts this.
- Hypothesis B: The vulnerability will be effectively mitigated through timely patching, preventing significant exploitation. This is supported by Palo Alto Networks’ proactive patching efforts and scheduled upgrades. The uncertainty lies in the speed and completeness of these updates.
- Assessment: Hypothesis B is currently better supported due to the company’s ongoing patching efforts and lack of evidence of current exploitation. Indicators such as an increase in attack attempts or delays in patching could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is not currently being exploited; Palo Alto Networks will complete patching in a timely manner; the exposed firewalls are representative of the broader network.
- Information Gaps: Specific data on the number of unpatched systems and the timeline for completing all patches.
- Bias & Deception Risks: Potential underreporting of exploitation attempts by affected entities; reliance on vendor-provided information which may be optimistic.
4. Implications and Strategic Risks
This vulnerability could lead to increased cyber threats if not addressed promptly, impacting both public and private sector entities relying on Palo Alto Networks’ firewalls. The situation could exacerbate existing cybersecurity challenges and strain resources.
- Political / Geopolitical: Potential for increased tensions if state actors exploit the vulnerability, leading to accusations and retaliatory measures.
- Security / Counter-Terrorism: Heightened risk of cyber-attacks disrupting critical infrastructure and services.
- Cyber / Information Space: Increased focus on securing network infrastructures; potential for misinformation campaigns exploiting the vulnerability.
- Economic / Social: Potential financial losses for affected organizations; erosion of trust in cybersecurity solutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Ensure all affected systems are patched; increase monitoring for signs of exploitation; communicate with stakeholders about the importance of timely updates.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular security audits and incident response planning; strengthen partnerships with cybersecurity firms for threat intelligence sharing.
- Scenario Outlook:
- Best: All systems are patched promptly, preventing exploitation.
- Worst: Delays in patching lead to widespread exploitation and significant disruptions.
- Most-Likely: Majority of systems are patched in time, with minor isolated incidents of exploitation.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, vulnerability management, network security, denial-of-service, threat mitigation, Palo Alto Networks, firewall protection
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us