Palo Alto Networks disclose a data breach linked to Salesloft Drift incident – Securityaffairs.com
Published on: 2025-09-02
Intelligence Report: Palo Alto Networks disclose a data breach linked to Salesloft Drift incident – Securityaffairs.com
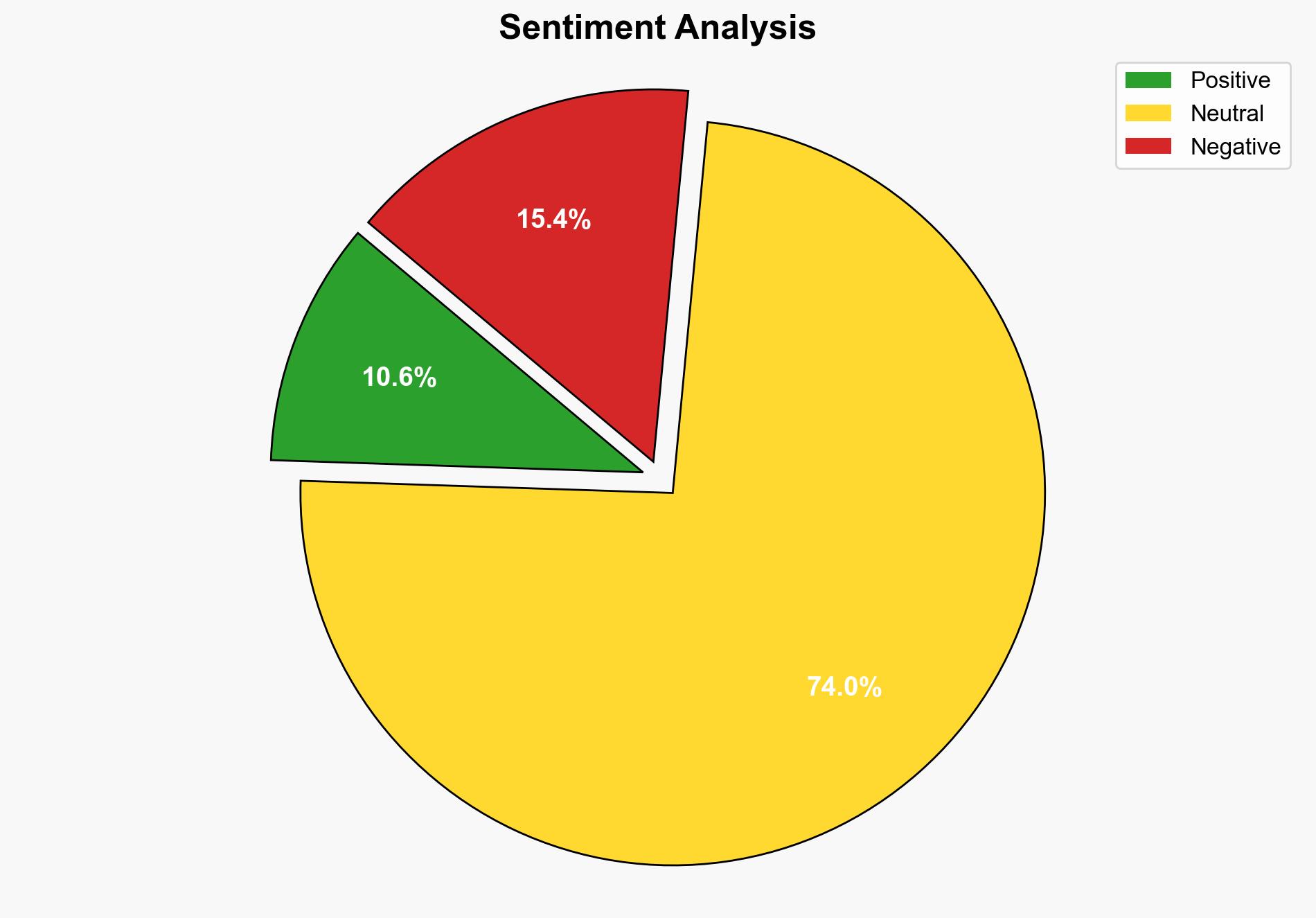
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the breach was primarily a result of a supply chain attack exploiting OAuth tokens, impacting multiple organizations including Palo Alto Networks and Zscaler. The confidence level is moderate, given the complexity of the attack and ongoing investigations. It is recommended that affected organizations enhance their supply chain security protocols and conduct thorough audits of third-party integrations.
2. Competing Hypotheses
1. **Hypothesis A**: The breach was a targeted supply chain attack aimed at exploiting OAuth tokens to gain unauthorized access to Salesforce data across multiple organizations.
2. **Hypothesis B**: The breach was an opportunistic attack exploiting known vulnerabilities in the Salesloft Drift application, with the primary goal of data exfiltration for financial gain.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the coordinated nature of the attack and the specific targeting of Salesforce integrations, suggesting a strategic intent rather than opportunistic exploitation.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the attackers had prior knowledge of the OAuth token vulnerabilities and the integration points within Salesforce.
– **Red Flags**: The rapid revocation of tokens and rotation of credentials by affected companies suggests potential foreknowledge of the breach, which could indicate insider involvement or prior warnings that were not publicly disclosed.
– **Blind Spots**: The full scope of data exfiltrated and the potential for further unauthorized access remain unclear, posing a risk of underestimating the attack’s impact.
4. Implications and Strategic Risks
The breach highlights vulnerabilities in SaaS integrations and the potential for widespread impact through supply chain attacks. The risk of similar attacks could escalate if attackers leverage exfiltrated data to target other organizations. Economically, affected companies face potential reputational damage and financial losses. Geopolitically, the incident underscores the need for international cooperation in cybersecurity defense.
5. Recommendations and Outlook
- Conduct comprehensive security audits of all third-party integrations and SaaS applications.
- Implement enhanced monitoring and anomaly detection for OAuth token usage.
- Develop a robust incident response plan specifically for supply chain attacks.
- Scenario Projections:
- Best Case: Rapid containment and mitigation prevent further breaches, and lessons learned strengthen future defenses.
- Worst Case: Attackers leverage exfiltrated data for further breaches, causing significant financial and reputational damage.
- Most Likely: Affected organizations strengthen defenses, but similar attacks continue to pose a threat due to persistent vulnerabilities.
6. Key Individuals and Entities
– Palo Alto Networks
– Salesloft
– Drift
– Zscaler
– Salesforce
7. Thematic Tags
national security threats, cybersecurity, supply chain vulnerabilities, data breach, SaaS security