PAN-SA-2025-0018 Chromium and Prisma Browser Monthly Vulnerability Update November 2025 Severity MEDIUM – Paloaltonetworks.com
Published on: 2025-11-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: PAN-SA-2025-0018 Chromium and Prisma Browser Monthly Vulnerability Update November 2025 Severity MEDIUM – Paloaltonetworks.com
1. BLUF (Bottom Line Up Front)
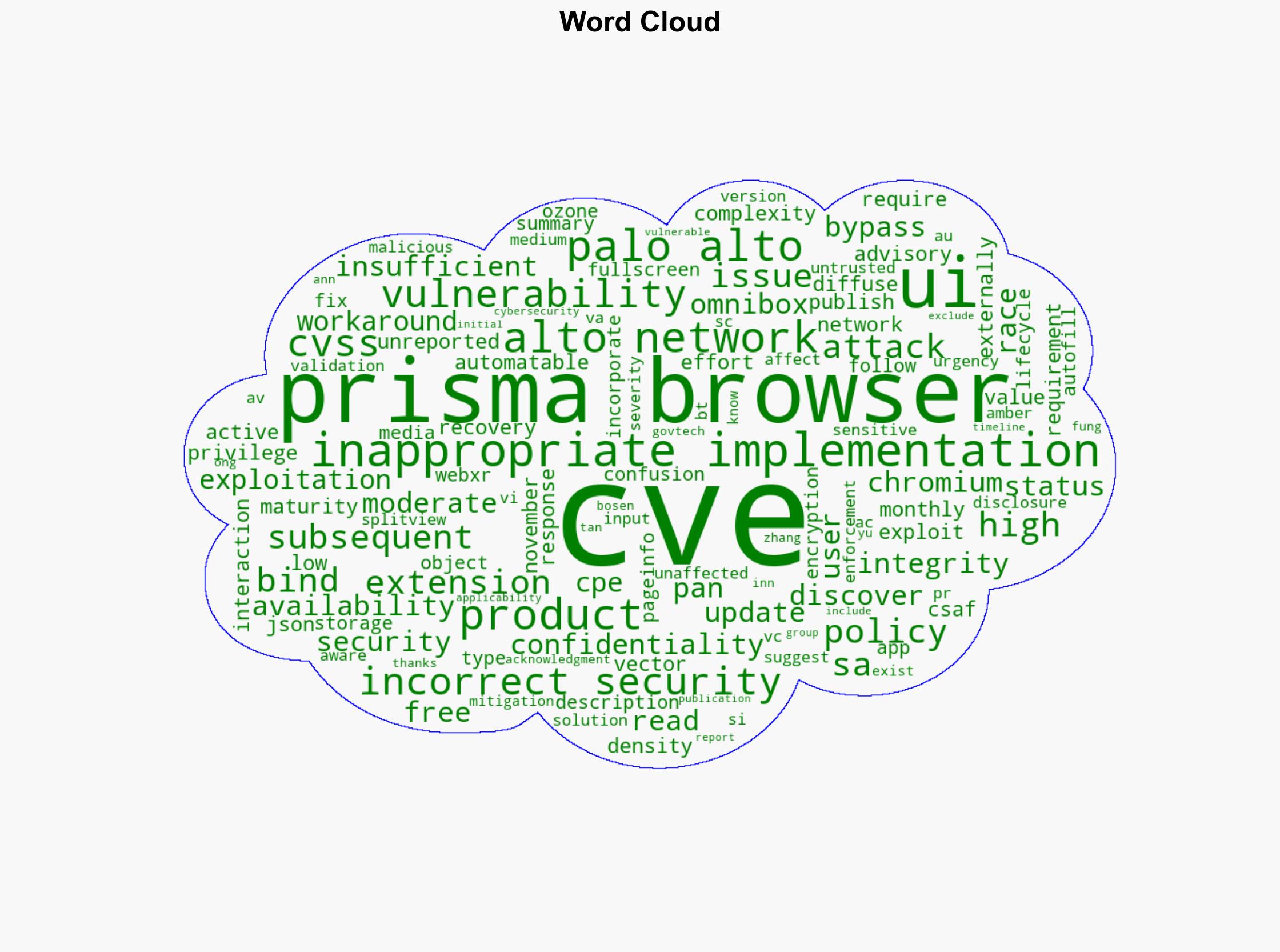
It is assessed with moderate confidence that the vulnerabilities identified in the Chromium and Prisma browsers pose a medium-level threat primarily due to their low attack complexity and high confidentiality, integrity, and availability impacts. The most supported hypothesis suggests that these vulnerabilities could be exploited by cybercriminals to gain unauthorized access to sensitive information. Immediate patching and user awareness campaigns are recommended to mitigate potential exploitation.
2. Competing Hypotheses
Hypothesis 1: The vulnerabilities in the Chromium and Prisma browsers are likely to be exploited by cybercriminals to gain unauthorized access to sensitive information, given the low attack complexity and high impact on confidentiality, integrity, and availability.
Hypothesis 2: The vulnerabilities will remain largely unexploited due to the moderate response effort required and the lack of known active exploitation, as reported by Palo Alto Networks.
Hypothesis 1 is more supported due to the nature of the vulnerabilities (e.g., inappropriate implementation, race conditions) that are commonly targeted by attackers. The lack of current exploitation reports does not preclude future attempts, especially given the vulnerabilities’ potential impact.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the vulnerabilities have not been widely exploited due to the absence of reported incidents. It is also assumed that the vulnerabilities will be patched promptly by affected organizations.
Red Flags: The advisory’s lack of specific exploitation details could indicate underreporting or a delay in detection. The absence of known workarounds suggests a potential gap in immediate mitigation strategies.
4. Implications and Strategic Risks
The vulnerabilities could lead to significant data breaches if exploited, impacting user trust and organizational reputation. Politically, state-sponsored actors could leverage these vulnerabilities for espionage, while economically, businesses could face financial losses due to data theft. The informational risk includes potential misinformation campaigns exploiting the vulnerabilities’ existence.
5. Recommendations and Outlook
- Actionable Steps: Organizations should prioritize patching affected systems and conduct user training to recognize potential phishing attempts. Implementing additional security measures, such as network segmentation and enhanced monitoring, is advised.
- Best Case Scenario: Vulnerabilities are patched swiftly, with no significant exploitation incidents reported.
- Worst Case Scenario: Delayed patching leads to widespread exploitation, resulting in major data breaches and financial losses.
- Most Likely Scenario: Some exploitation occurs, but prompt patching and mitigation efforts limit the overall impact.
6. Key Individuals and Entities
Tan Inn Fung, Yu Ann Ong, Zhang Bosen – GovTech Cybersecurity Group (credited with discovering and reporting the vulnerabilities).
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology