Pentagon report finds Hegseth’s Signal app use jeopardized troop safety and violated policy
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hegseth could have endangered troop safety with Signal chat – Pentagon watchdog
1. BLUF (Bottom Line Up Front)
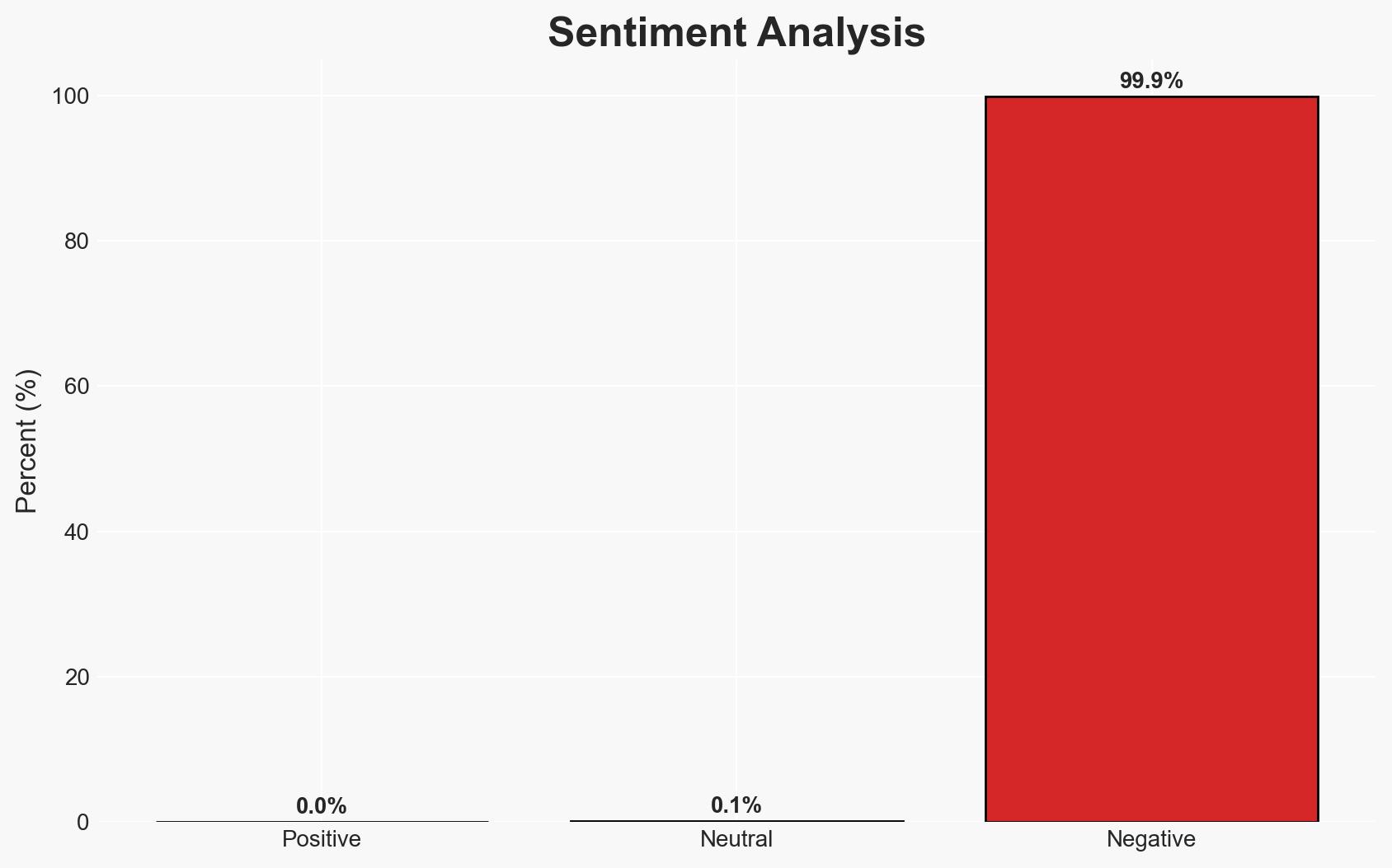
The unauthorized use of a personal device and Signal app by US Defence Secretary Pete Hegseth to discuss military operations potentially jeopardized troop safety and raised significant national security concerns. The incident, known as “Signalgate,” highlighted vulnerabilities in the administration’s handling of classified information. The most likely hypothesis is that Hegseth’s actions were a result of procedural oversight rather than intentional misconduct. Overall confidence in this assessment is moderate due to incomplete data and potential biases in the sources.
2. Competing Hypotheses
- Hypothesis A: Hegseth’s use of Signal was a procedural oversight, not intentional misconduct. Supporting evidence includes his legal authority to declassify information and his statement of no classified information being shared. Contradicting evidence includes the accidental inclusion of a journalist in the chat and the use of a personal device, which suggests a lack of adherence to protocol.
- Hypothesis B: Hegseth intentionally bypassed security protocols to expedite communication. Supporting evidence includes the deliberate use of a personal device and app known for encryption, potentially indicating a desire to circumvent official channels. However, the lack of direct evidence of intent and his legal authority to declassify information contradicts this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the absence of direct evidence of intent to bypass protocols and Hegseth’s authority to declassify information. Key indicators that could shift this judgment include new evidence of intent or procedural changes following the incident.
3. Key Assumptions and Red Flags
- Assumptions: Hegseth had the authority to declassify the information; the leak was unintentional; Signal was used for its encryption features.
- Information Gaps: Complete transcripts of the Signal chat; Hegseth’s rationale for using a personal device; any internal communications about the incident.
- Bias & Deception Risks: Potential bias in Hegseth’s public statements; media portrayal of the incident; possible deception in the administration’s denial of classified information being shared.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of communication practices within the administration and potential policy changes. It may also impact US credibility in handling sensitive information.
- Political / Geopolitical: Potential erosion of trust in US leadership and diplomatic relations, particularly with allies concerned about information security.
- Security / Counter-Terrorism: Increased risk to operational security and troop safety if communication protocols are not tightened.
- Cyber / Information Space: Highlighted vulnerabilities in digital communication practices could lead to enhanced cybersecurity measures.
- Economic / Social: Limited direct economic impact, but potential social unrest if perceived as a broader pattern of negligence in national security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive review of communication protocols; issue interim guidance on the use of personal devices for official business.
- Medium-Term Posture (1–12 months): Develop and implement enhanced training for officials on information security; establish clear accountability measures for breaches.
- Scenario Outlook:
- Best: Implementation of robust security protocols restores confidence.
- Worst: Further breaches lead to significant operational risks and diplomatic fallout.
- Most-Likely: Incremental improvements in security practices with ongoing scrutiny.
6. Key Individuals and Entities
- Pete Hegseth, US Defence Secretary
- Mike Waltz, then-National Security Adviser
- The Atlantic, media outlet involved
- Jeffrey Goldberg, Editor-in-Chief of The Atlantic
7. Thematic Tags
National Security Threats, national security, information security, military operations, classified information, communication protocols, cyber risk, diplomatic relations
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us