Pentagon Report Finds Pete Hegseth Violated Protocol with Sensitive Signal Communications, Impact Unclear
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Has the Pentagon really exonerated Pete Hegseth over Signal leaks
1. BLUF (Bottom Line Up Front)
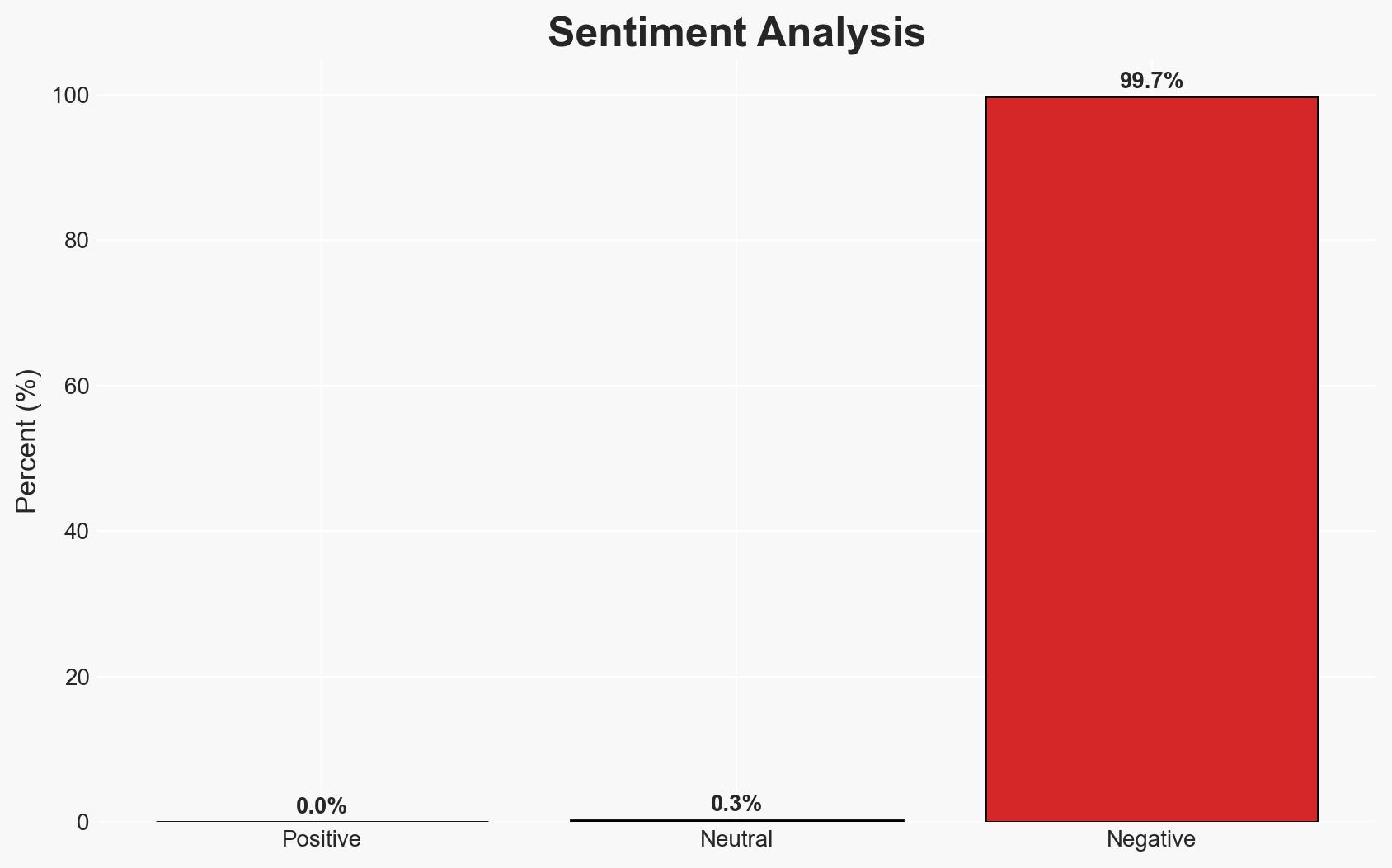
The Pentagon inspector general’s report has not fully exonerated Pete Hegseth, despite his claims. The report highlights protocol violations regarding the use of Signal for sensitive communications, posing potential risks to military operations. The situation remains politically sensitive, with moderate confidence that further scrutiny could impact Hegseth’s position. Key stakeholders include US defense personnel and political figures.
2. Competing Hypotheses
- Hypothesis A: Pete Hegseth’s use of Signal for sensitive communications was a breach of protocol, but his authority to declassify information mitigates the severity of the breach. Supporting evidence includes the inspector general’s acknowledgment of his declassification authority. Contradicting evidence involves the unauthorized sharing of information with non-officials.
- Hypothesis B: Hegseth’s actions represent a significant security breach that could have compromised military operations, warranting disciplinary action. This is supported by the report’s findings of unauthorized information sharing and potential endangerment of US troops. Contradicting evidence includes the lack of explicit consequences outlined in the report.
- Assessment: Hypothesis A is currently better supported due to the inspector general’s acknowledgment of Hegseth’s declassification authority, though this judgment could shift if further evidence of operational compromise emerges.
3. Key Assumptions and Red Flags
- Assumptions: The inspector general’s report accurately reflects the extent of Hegseth’s protocol violations; Hegseth’s declassification authority is applicable in this context; the report’s findings are comprehensive and unbiased.
- Information Gaps: Details on the specific content of the Signal communications and the full scope of unauthorized recipients are missing.
- Bias & Deception Risks: Potential bias in media reporting and political motivations influencing the interpretation of the report; risk of Hegseth’s public statements being strategically misleading.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of communication protocols within the Pentagon and potential political fallout affecting Hegseth’s career.
- Political / Geopolitical: Heightened bipartisan scrutiny may lead to legislative or executive actions affecting defense leadership.
- Security / Counter-Terrorism: Potential review and tightening of communication protocols to prevent similar breaches.
- Cyber / Information Space: Increased focus on secure communication practices and potential vulnerabilities in using non-secure apps.
- Economic / Social: Limited direct impact, though public trust in defense leadership may be affected.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough review of communication protocols; initiate training for Pentagon officials on secure communication practices.
- Medium-Term Posture (1–12 months): Develop partnerships with secure communication providers; enhance oversight mechanisms for protocol compliance.
- Scenario Outlook: Best: Protocols strengthened without major political fallout. Worst: Significant political repercussions leading to leadership changes. Most-Likely: Continued scrutiny with minor adjustments to communication practices.
6. Key Individuals and Entities
- Pete Hegseth, US Defense Secretary
- Steve Stebbins, Pentagon Acting Inspector General
- US President Donald Trump
- Vice President JD Vance
- Secretary of State Marco Rubio
- National Intelligence Director Tulsi Gabbard
7. Thematic Tags
Counter-Terrorism, protocol violations, secure communications, military operations, political scrutiny, defense leadership, information security
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us